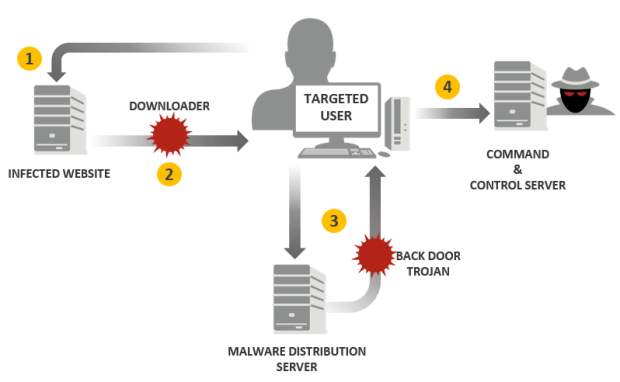
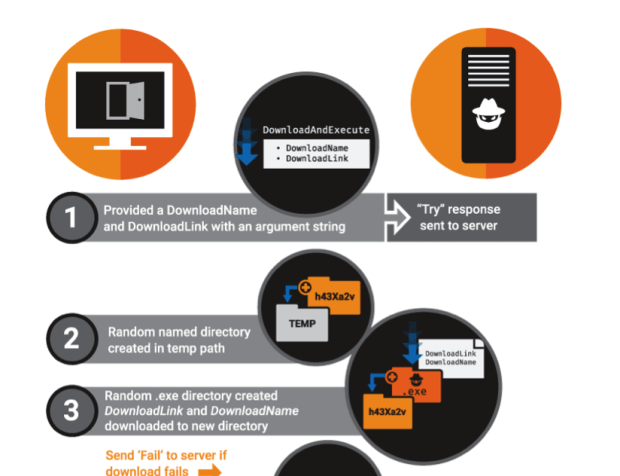
Canadian Gold-Mining firm Goldcorp hacked
Canadian Gold-Mining Company Goldcorp suffered a major data breach, 14.8 GB Data Stolen, the hackers plan to release more data dumps soon. The Canadian gold-mining firm Goldcorp suffered a major data breach,Read More →