How to Infiltrate Industrial OT Networks and Stay Undetected for Half a Decade
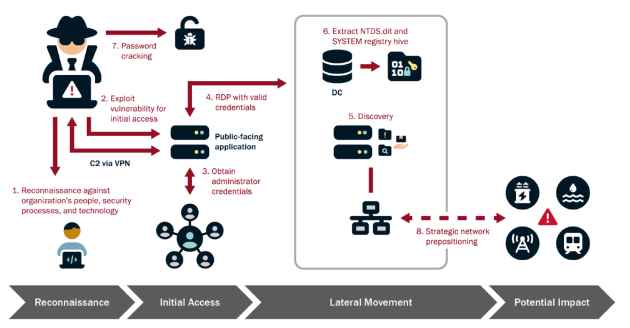
The Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the National Security Agency (NSA), Federal Bureau of Investigation (FBI), and international partners, has issued a critical advisory warning aboutRead More →