CVE-2017-6074 – a new 11-year old Linux Kernel flaw discovered
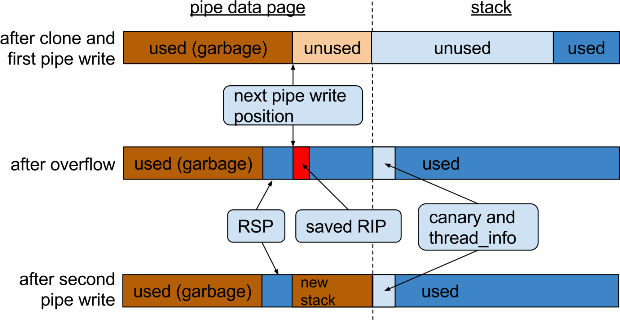
Security expert discovered a new 11-year old privilege escalation vulnerability, tracked as CVE-2017-6074, in the Linux kernel. A new privilege escalation vulnerability, tracked as CVE-2017-6074, has been discovered in the Linux kernel andRead More →