Russia is in the midst of a national voting process about important constitutional amendments, and this time the authorities have decided to probe with an electronic voting system (e-voting) in the Moscow and Nizhny Novgorod regions, as security testing course specialists mention. The authorities say that this system will allow citizens to decrypt their own votes, giving greater confidence in this process.
This is not the first time an electronic voting system is involved in Russian elections. In 2019, Moscow’s IT department developed a remote voting system based on blockchain technology. As a result, the votes were encrypted using the department’s own version of an ElGamal encryption. After multiple tests, experts found several vulnerabilities in the encryption system.
In this new system, the voters’ ballot is encrypted with the help of TweetNaCI.js, a JavaScript library developed by a researcher named Dmitry Chestnykh, who discovered that the developers of Russia’s remote electronic voting system were using their framework.
Greater security when voting?
The above system encrypted each vote individually, using a unique secret key. Therefore, to decrypt a vote, it had to obtain the secret key of the recipient, in this case, the electoral committee. On the other hand, the new system issues a shared key for the sender and recipient; in this case the voter and the electoral committee, which can be used to encrypt the vote, as well as to decrypt it, as mentioned by security testing course experts.
To test the new system, Meduza researchers conducted an experiment on an electronic ballot that was issued with Google Chrome, discovering that obtaining the secret key is relatively easy. According to the experts, it was possible to decipher the ballot of a voter who participated in the experiment, so voters are confident that the integrity of their vote is preserved.
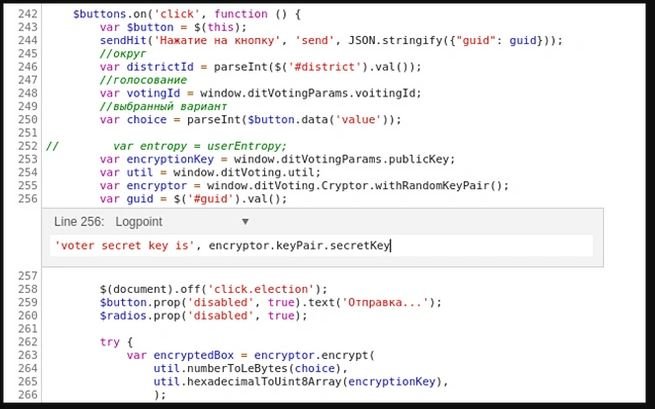
On the other hand, security testing course experts mention that this allows users to force the vote. In theory, an employer could, in addition to verifying that its employees have voted, find out how the vote was cast. In addition, saving these encryption keys does not require an employee to have technological knowledge. For example, they might be asked to download a special extension for a browser, which replaces randomly generated keys with static ones. This would greatly simplify the task of decrypting votes, as everyone would share a single encryption key.
This same feature can be used to monitor the integrity of the vote count, in case the electoral commission refuses to disclose the encryption keys for each specific electronic ballot. For example, supporters of a particular candidate might agree to install the same browser extension, which would allow them, over the course of the voting period, to track the minimum number of votes their candidate should have during the final count.
Developers of e-voting systems could ban voters from using a shared set of encryption keys, but this would be futile. According to the developer of this framework, there are multiple ways to circumvent such security controls, including browser extensions that write seemingly random encryption keys that can be restored at a later date. “An extension could simply save the keys to a central database,” Chestnykh also suggested. “The Curve25519 algorithm is very fast, so deciphering millions of votes would be easy.”
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











