Security testing course specialists report detection of a malicious campaign in which attackers use automated SharePoint messages to send phishing emails against Office 365 users.
One feature that stands out in this attack is that the email used by threat actors is not targeted against a specific user, but tries to encompass any possibilities related to the recipient’s work. In this way, cybercriminals take advantage of the high chances of a user falling into the trap, thereby gaining access to their login credentials and using them maliciously.
After analyzing some emails related to the attack, security testing course experts concluded that these messages are brief and use terms and structures similar to the text of automatic notifications. Threat actors use the target company name in every possible place with the aim of making victims believe that it is internal communication; like other phishing campaigns, the email contains a link to a malicious site.
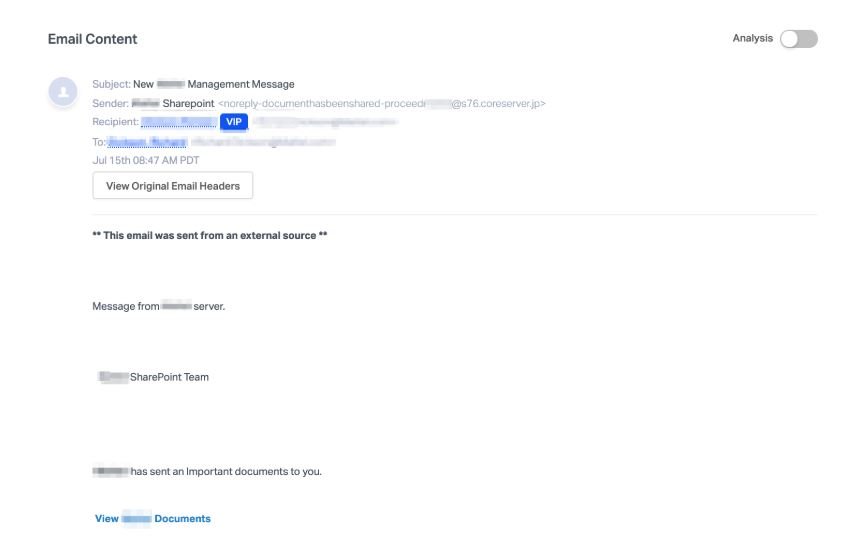
Regarding the payload used in the attack, its discharge starts by providing the victim with a button; by clicking on it, users are redirected to a submission form in which threat actors will extract the login credentials of the victims. The malicious website could also download a PDF document to redirect users to other websites.
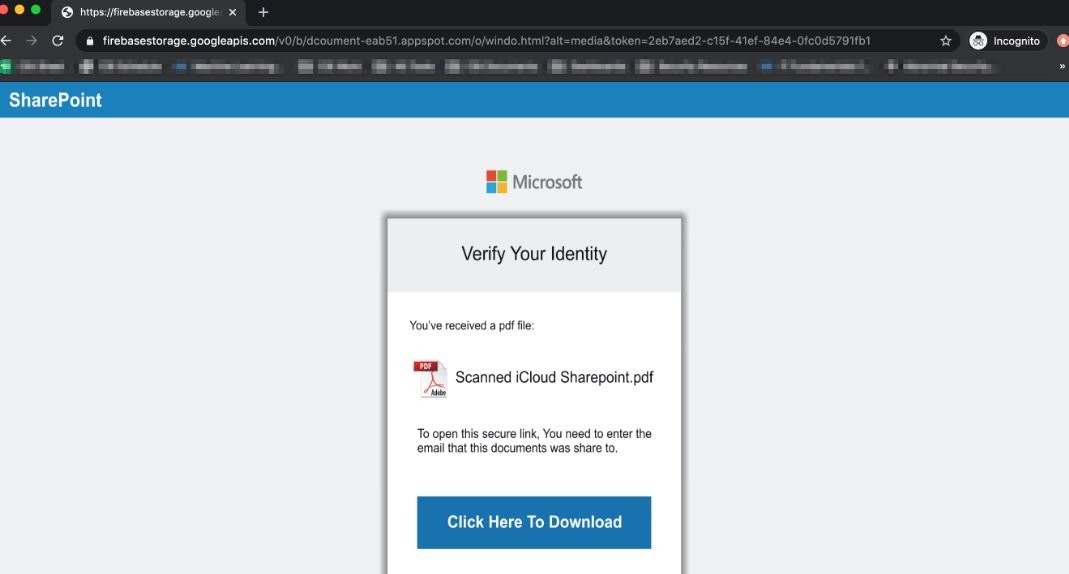
This attack could compromise organization-wide networks, as threat actors will be able to launch subsequent attacks to extract higher-privileged credentials and access sensitive information from the target organization, security testing course specialists mention.
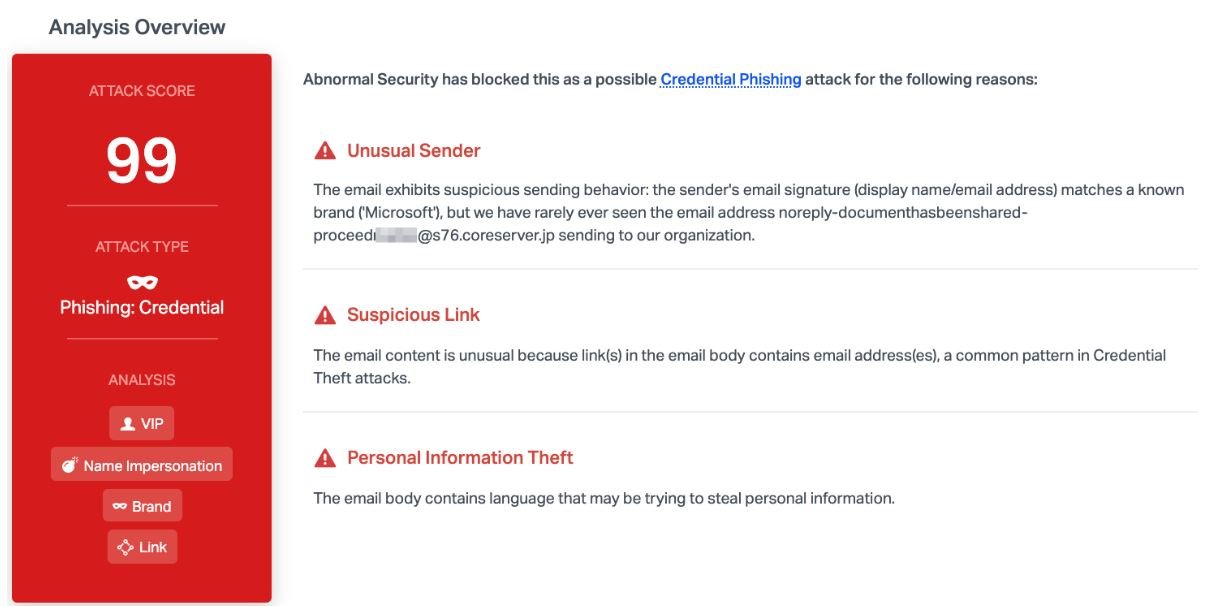
The report indicates that this attack is highly effective thanks to the technique to hide the malicious URL of the hackers, disguised as text via a hyperlink. If the URL was not hidden, the target user might detect malicious activity. In addition, the page to which users are redirected is virtually identical to a secure Sharepoint file, where users are prompted to enter their login credentials. The hackers even took the time to include the official Microsoft and Sharepoint logos, giving the website a more legitimate look.
The recommendation for users is the same when it comes to a phishing campaign, it is best to ignore these kinds of messages and notify the IT area to analyze the situation and, if necessary, contain the threats before it is too late.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











