Invisible Internet Project (I2P) is the most important anonymous network project in the world as per cyber security experts. Users of this tool may browse the sites and use the services without disclosing a single byte of their information to third parties, including the authorities. Although I2P was introduced in 2003, the network continues to grow and expand.
I2P is based on the principle of overlay, that is, an anonymous and secure layer runs on top of another network. One of the main features of I2P is decentralization, as there are no DNS servers on this network, as these are replaced by automatically updated “address books”.
Each I2P user can get their own key, which cannot be tracked by others. Below are some differences between this anonymous network and Tor browser:
- Tor uses onion routing, sending its traffic through the well-known eight proxy method that alone does not protect against decryption attempts. On the other hand, I2P relies on traffic encryption
- Tor resorts to using SOCKS, while I2P prefers to use its own API
- I2P tunnels are unidirectional unlike Tor
Still, not everything is a difference between these tools, as both of them share a fundamental feature: these platforms cannot be accessed without additional software. We know what it takes to use Tor, but what is required to use I2P? The required items are shown below:
- Java in its version for Windows systems, available here
- Official I2P installer, available on its website
- If you have Windows, open “→ All I2P →” and select “Start I2P”. If you have Linux, you probably know what to do yourself
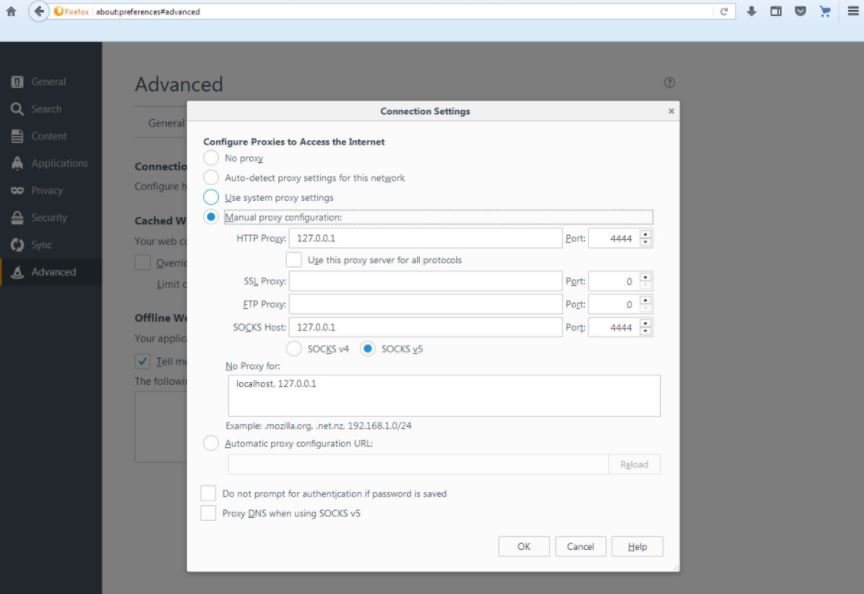
- The next step is to open a browser like Firefox and access “→ Settings → Network → Use Proxy”. We’ll fill in the fields in the same way as in the following screenshot
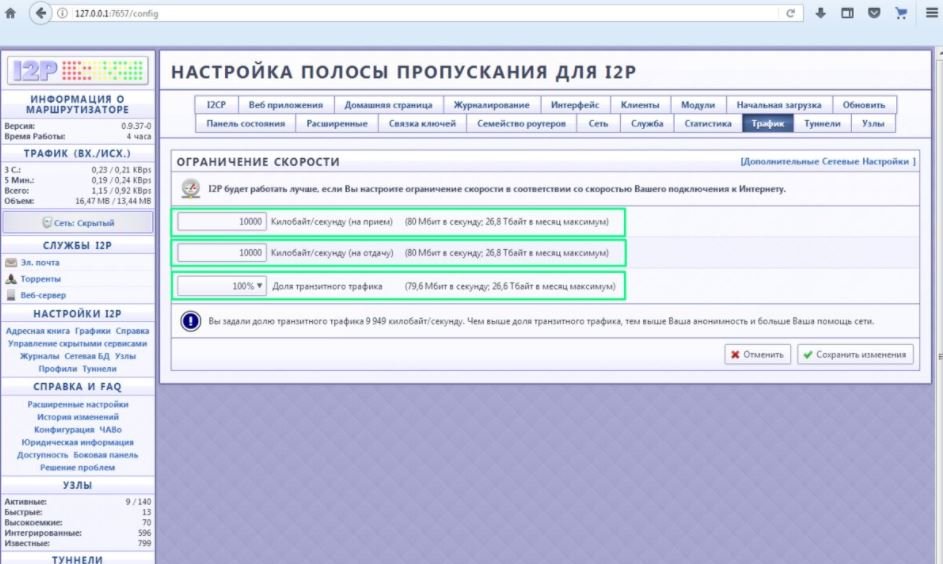
You can access the console yourself using http://127.0.0.1:7657/home.
This allows you to start using I2P. You can go to the “Traffic” section and there you can change the transit traffic ratio to 100% and increase the number of kilobytes to load and download per second to maximum, as shown in the following screenshot. Practice shows that this reduces network response time.
What can I2P find?
Although this is not as vast a world as tor extensions, proper search will allow you to find multiple really interesting platforms. Remember that this is an anonymous network, so it would not be uncommon to find forums for potentially illegal activity.
Blogs and forums
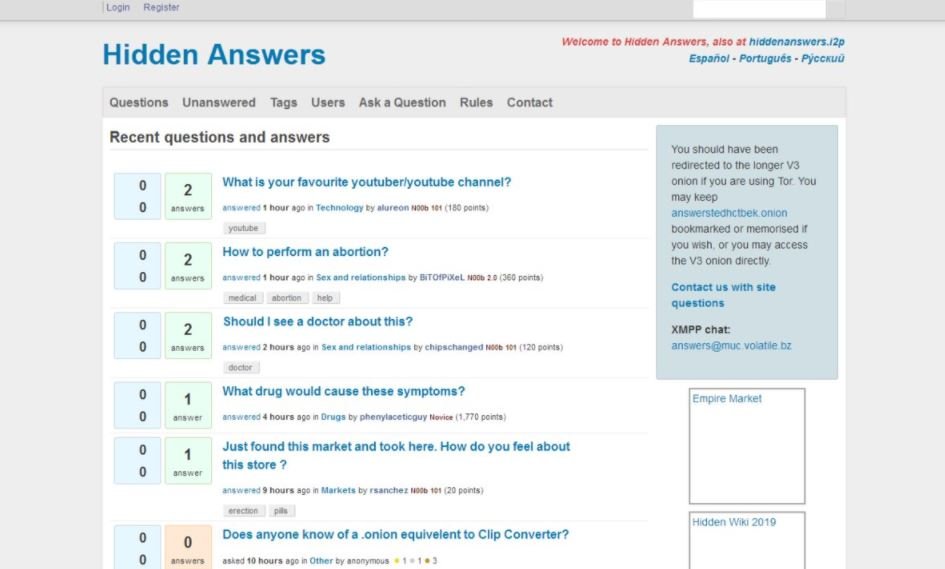
The Hidden Answers forum is a good starting point. This is a platform in people asking questions to discuss any topic, from popular youtubers to how to perform an abortion. Any forum user can answer any question, so needless to say that applying the tips available in this forum is not the best idea. SecretChat, the Russian-speaking counterpart of Hidden Answers, is also a good alternative.
I2P is full of personal blogs, especially on topics that many users would not dare to have on the conventional Internet. Of course, I2P is not safe from pornographic sites, although it should be mentioned that there is nothing too different from what any Internet user can find.
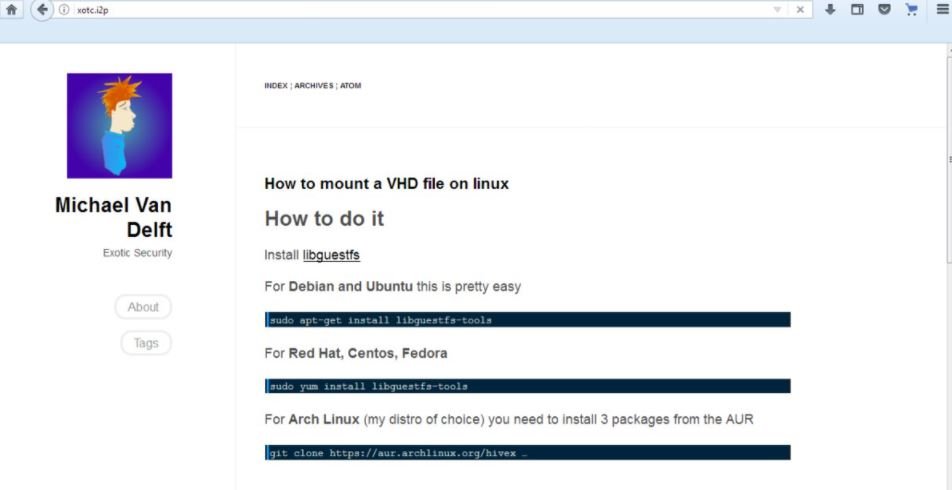
Not all blogs available on I2P are useless. In your personal space, cyber security expert shares helpful network security tips, as well as material that will be of great help to programmers around the world.
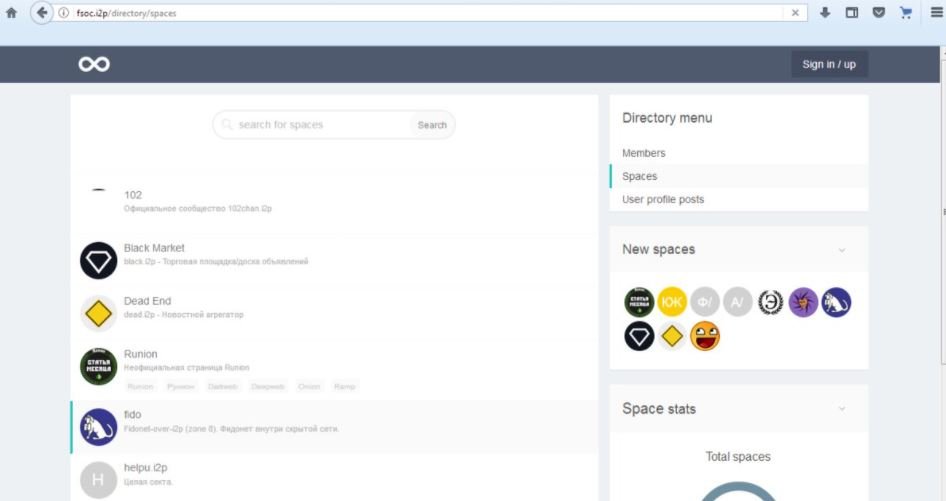
On how to find more information about the sites available on I2P, at F*ck Society users could find information about all kinds of sites on I2P where banned substances, blogs of radical political postures and other topics very typical of forums can be found on dark web.
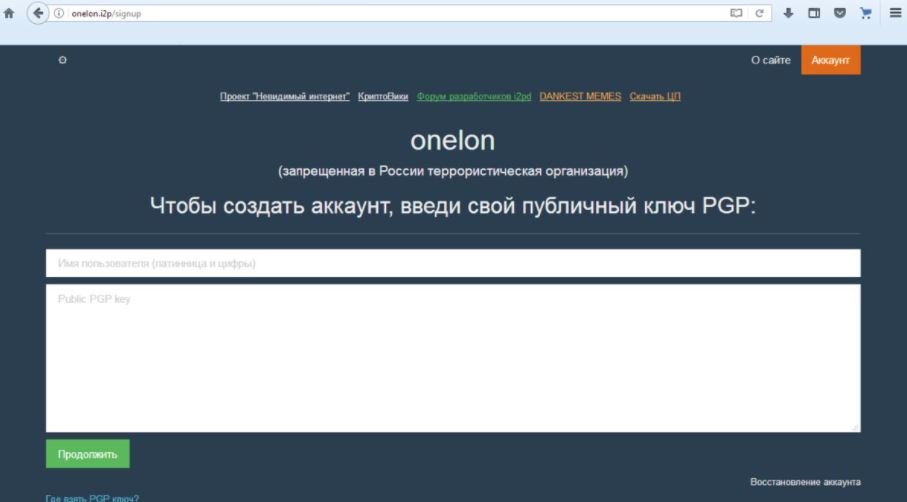
Finally, Onelon is a kind of Facebook in which there are virtually no restrictions. Users can post anything and write to any user and with any intention, although the onion browser version is much more popular.
Communications
One of the most useful services available in I2P is vPass, which helps users find a password for specific domains. Security specialists mention that virtually all tools of this class are also available in .onion, although I2P provides complete anonymity like Echelon and I2P Bote.
Trade forums
I2P would be an incomplete network if it did not have websites dedicated to the sale of all kinds of items. Forums like nvspc or Eepsites function as a counterpart to popular platforms like Hydra in .onion so that those interested in buying unusual items contact sellers around the world and make payments, usually in cryptocurrency.
Another interesting platform is Wiki I2P, a Russian-speaking wiki dedicated to project development that allows users to make edits anonymously to existing articles. This wiki also serves as a directory of links to popular platforms on I2P, although many of the links are broken.
Libraries
Platforms like Flibusta are also found in I2P, and work successfully for all kinds of users. On the other hand, platforms such as Extreme Chemistry or Fantasy World focus on users with more specific interests, although they have a reduced catalog.
File hosting
There are many file hosting services, including Buried and Serien. There are also sites for exchange through torrents.
Cybercrime
The Tor network clearly leads the way in the treatment of illegal online issues, although this does not mean that there is no cybercriminal community in I2P. However, the groups hosted on this network are really small and not any user can contact them; However, it is possible to hire denial of service (DoS) attacks, password hacking and similar services like Armada or BumpTeam

More experienced users recommend not contacting the operators of these services, as there is always the possibility of looking for problems with law enforcement agencies or even scams.
Cryptocurrency exchange
I2P is a very open network with Bitcoin and other variants of virtual assets. For example, this network allows transactions with Zcash and many other well-known cryptocurrencies. It should be remembered that the use of Bitcoin and other options may have malicious purposes thanks to its anonymity, so it is worth thinking twice before making any transaction in I2P.
An attractive option for many users
I2P is a relatively complex network for many users, mainly because there are similar options in .onion much easier to use. According to specialists, this is not the ideal network for publishing content, but its use has much more to do with anonymity in navigation; At least in this regard, I2P works much better than Tor or a VPN.
Having a decentralized network is important, even for many conventional Internet users. Although these projects sometimes have a bad reputation, I2P is a considerable effort to improve the privacy experience when using the Internet.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











