Cybersecurity specialists revealed the finding of a cross-site scripting (XSS) vulnerability in Apache Velocity Tools that could be exploited by threat actors to compromise U.S. government websites, including NASA. The flaw was reported 90 days ago, although it appears to have not been corrected to date. This is a Java-based template engine and used by developers to design views in a Model-View-Controller architecture. Velocity Tool is a subproject that comprises classes that make it even easier to integrate Velocity into web applications.
Experts mention that the flaw is present in all versions of Velocity Tools even though a fix has been released for months. Although the formal disclosure process has not been formally completed, the flaw was identified as CVE-2020-13959.
The Apache Velocity Tools class that contains this flaw is included in more than 2600 unique binaries of prominent software applications available for download from npm, PyPI, Maven Central, and other open source repositories. This is a very popular composer among developers, so this report is crucial.
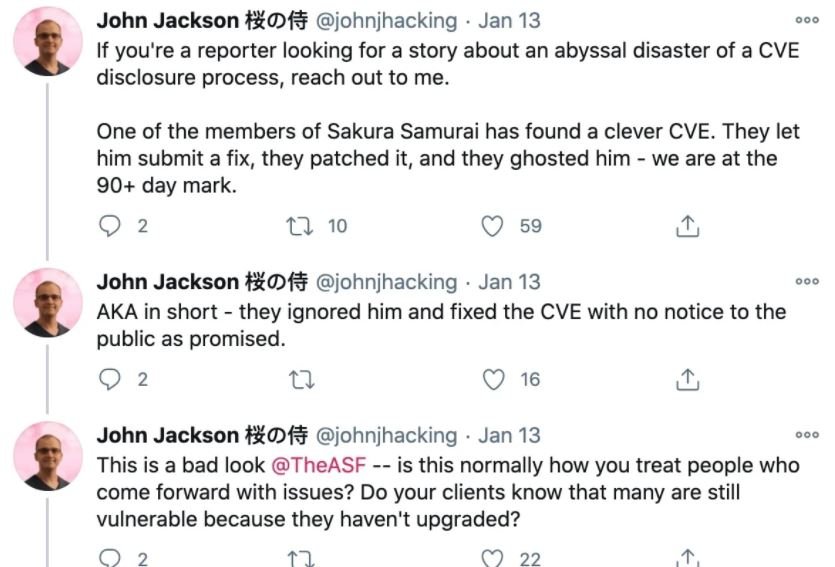
Jackson Henry, security researcher at Sakura Samurai first reported the flaw in October 2020; while the above-mentioned correction was issued, a public report never occurred, which proved troubling to the researcher and some developers.
The flaw exists in how the VelocityViewServlet view class renders the error pages. When an invalid URL is accessed, the “template not found” error page reflects the resource path portion of the URL as it is, without escaping possible XSS scripts. Subsequently, a threat actor could trick a victim into clicking on that URL, leading to a phishing platform where they can extract sensitive information.
Vulnerable deployments are employed by multiple U.S. government websites, including .nasa.gov, and .gov.au. There are some more complex variants of the attack, including social engineering attacks, which would allow threat actors to collect session cookies from registered users and hijack a large number of sessions.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











