Nowadays millions of users concerned about their privacy when browsing the Internet resort to using tools to hide their activity as much as possible, using methods like the web browser in incognito mode or even the use of virtual private network (VPN) solutions. However, this does not mean that users’ online activity will be completely safe as there are multiple tools to bypass these protections.
This time, the web security experts from the International Institute of Cyber Security (IICS) will talk you about Supercookie, a favicons tool to assign a unique identifier to all users of a website, which will allow you to perform a detailed track of all the online activity of the target user.
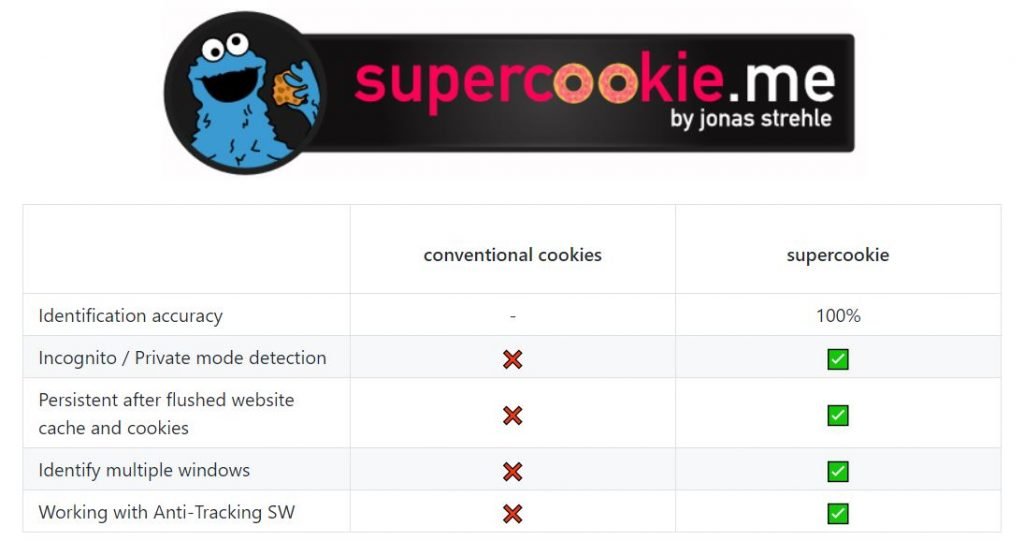
Unlike other similar tools, the identifier assigned by Supercookie is stored almost permanently and persists even if the user switches web browsers, uses incognito mode or VPNs and even despite more aggressive changes such as cache flushing and system restart, web security experts mention.
Favicons?
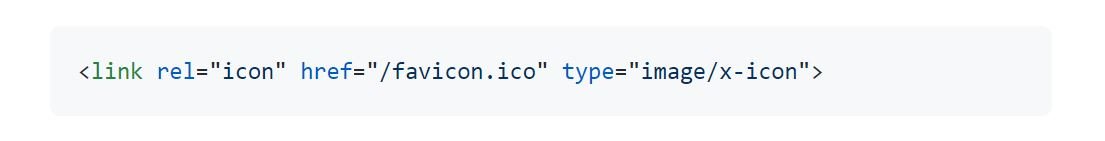
One of the main features of today’s web browsers is the use of favicons, a tiny logo (measures approximately 16×16 or 32×32 pixels) used by browsers to mark a website. In most cases, this icon is displayed in the address bar next to the web page name.
To include favicons in a website, developers must add an attribute in the header of the web page. If this tag exists, the browser prompts for the predefined font icon, and if the server response contains a valid icon file that can be rendered correctly, the browser displays this icon. If this is not true, web security experts mention that a blank favicon will be displayed.
Web browsers should facilitate access to favicons, so this information is cached in an isolated host database identified as a favicon cache (F-Cache). According to web security experts, entering data into this database should include the URL visited, favicon ID and time-to-live (TTL). This allows developers to delimit some segments of their website, but it also creates the opportunity to track users’ online activity.
When a user visits a website, the browser should check if a favicon is required by searching for the link reference source in the shortcut icon to the requested web page. The browser then initially checks the local F-Cache to find an entry with the website URL active; If a favicon entry exists, the icon will be loaded from F-Cache to be displayed to the user.
However, if an entry does not exist (for any possible reason) the browser will make a GET request to the server to load the site favicon.
Installation
Attack scenario
Threat actors may assign a unique identifier to each browser to obtain detailed logs of user activity, dodging VPN tools, cookie or cache deletions, and even becoming useless, more complex techniques such as manipulating client headers.
Web security experts mention that a web server can intuit whether a browser has already loaded a favicon or not: therefore, when the browser requests a web page, if the favicon is not in the local F-cache, another request is made for the favicon. If the icon already exists in F-Cache, no other requests are sent.
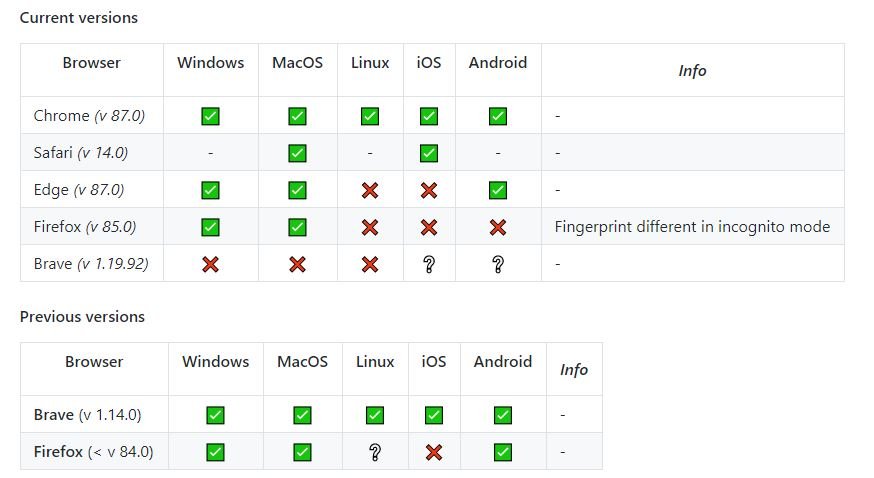
By combining the status of delivered and uneivered favicons, developers (or threat actors) can assign a unique pattern or identifier to the customer. When the website is reloaded, the web server can reconstruct the identification number with the network requests sent by the client for the missing favicons and thus identify the browser.
Supercookie is available in its developers’ GitHub repository. Remember that this is a tool created for entirely didactic purposes, so its misuse is not the responsibility of IICS or the developers. To learn more about web security, computer security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











