Cybersecurity specialists reported the discovery of a severe flaw in the design of some middlebox models, a term referring to computer network devices that transform, inspect, filter and manipulate traffic for purposes other than packet forwarding. Some implementations of these devices include the use of firewalls, network address translators (NATs), and deep packet inspection (DPI) systems.
Instead of trying to replicate the entire three-way handshake on a TCP connection, threat actors trying to deploy a denial of service (DDoS) attack could send a combination of non-standard packet streams to the middlebox, making it believe that the TCP handshake has ended and would allow the connection to be initiated.
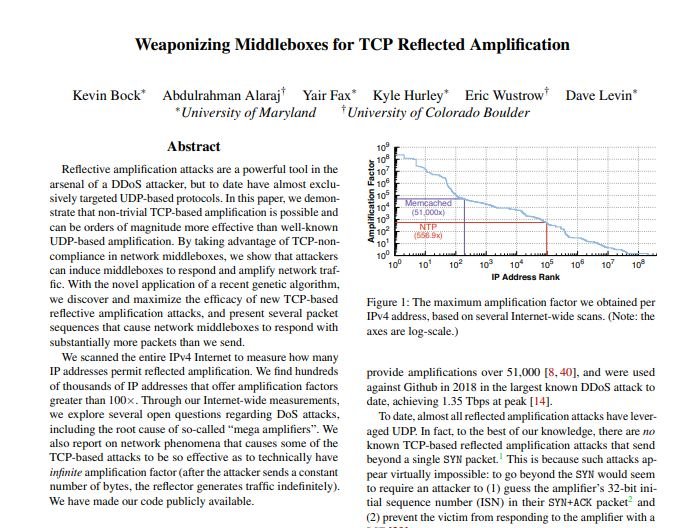
This would not be a problem under normal circumstances. However, if threat actors try to access a website banned by a system administrator (adult content, entertainment and gambling websites, among others), the middlebox would issue a blocking page that would normally be much larger than the initial package, generating a DDoS amplification effect.
After multiple tests, researchers from the University of Colorado and the University of Maryland point out that a large vector for the deployment of TCP denial of service (TCP DDoS) attacks are websites typically blocked by nation state censorship systems or by business policies.

While the research team tested several websites banned by virtually any web administrator, it was found that five specific domains tended to get answers from most middleboxes on the Internet and would be a reliable factor for these attacks:
- www.youporn.com (pornography website)
- www.roxypalace.com (betting and gambling)
- plus.google.com (social media website)
- www.bittorrent.com (file sharing platform)
- www.survive.org.uk (sex education)
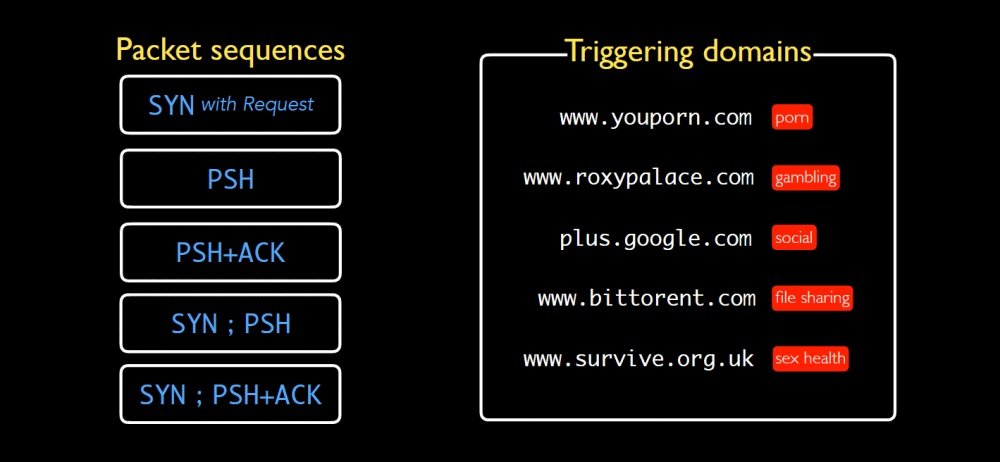
While not all middleboxes respond in the same way to these tests, the researchers concluded that these five websites can power a DDoS attack. University of Maryland researcher Kevin Bock mentions that amplification factors varied according to middlebox type, vendors, system configurations, and network configurations.
The researcher notes that a scan of the entire IPv4 Internet address space was performed at 35 different times to discover and index middleboxes that would amplify TCP DDoS attacks. In total, 200 million IPv4 addresses corresponding to network middleboxes were found that could be used for an attack. Typically, these systems operate with large traffic loads and are sometimes misconfigured with traffic loops that send the same malformed TCP packet multiple times through the same middlebox, effectively allowing the deployment of loopback DDoS attacks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











