Cybersecurity specialists report the detection of a new version of the Mozi botnet that is now capable of manipulating the web traffic of the affected implementations using DNS spoofing techniques and HTTP sessions hijacking. This criminal operation was detected by Microsoft security teams, who claim that hackers began targeting Netgear, Huawei and ZTE devices.
Mozi was first detected in 2019 by Netlab researchers, reaching around 15,000 infected devices in just a couple months.
The researchers claim that these devices are valuable targets for hackers, as they can be the ideal entry point to a corporate network: “The compromise of these routers would allow Man-in-The-Middle (MiTM) attacks by hijacking HTTP and DNS spoofing; this would allow subsequent attacks such as ransomware infections and other malicious practices.”
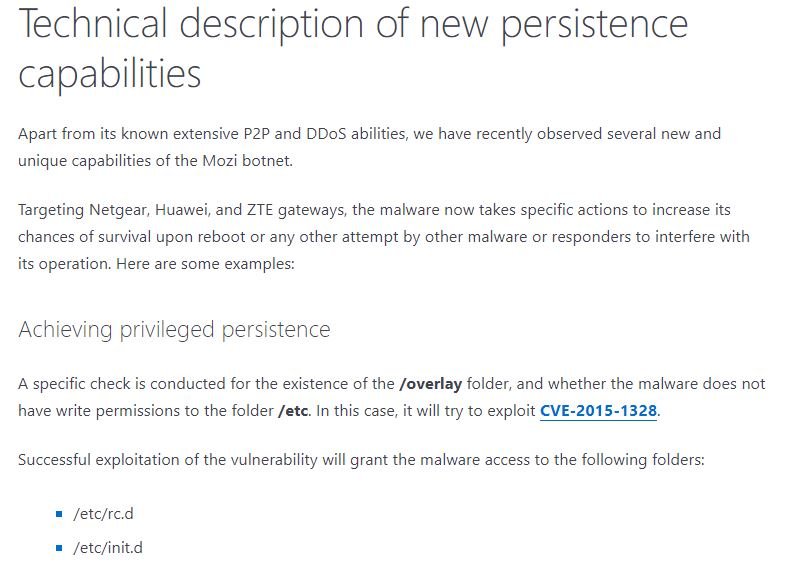
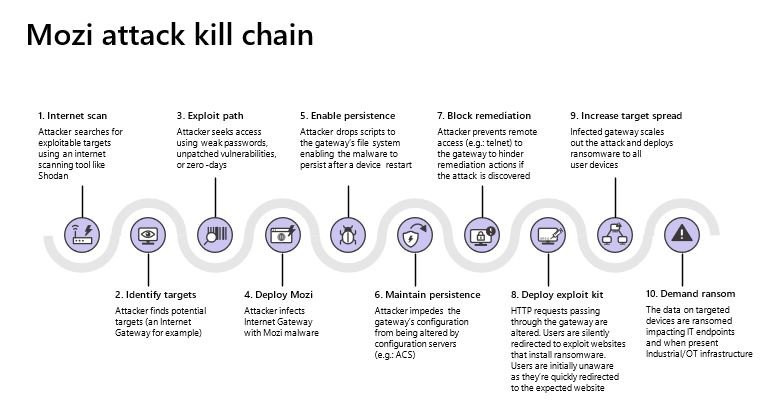
In addition to these new features, the new version of the botnet features advanced persistence and adaptation capabilities to the compromised gateway architecture, which will allow Mozi operators to prevent malicious payloads from being removed during a device reboot, something rare among ransomware developers.
Mozi’s attack method also allows threat actors to plan for more complex attacks, such as deploying modules on infected gateways for interception of HTTP and DNS requests and denial of service (DoS) conditions.
As if that weren’t enough, new versions of Mozi will also be able to tell the infected gateway to respond to DNS requests from specific web domains with a custom IP address to redirect users to a malicious server, allowing hackers to deploy phishing campaigns.
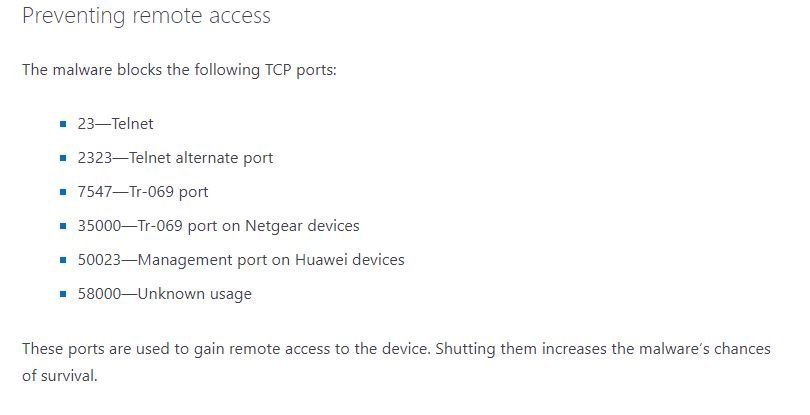
The advanced features of this botnet allow a stealth redirect of HTTP 301, which allows users to send users of legitimate websites to malicious platforms. Microsoft mentions that hackers are exploiting weak Telnet passwords, in addition to multiple un-updated vulnerabilities to gain access to affected devices.
Still, the operating system makers did not provide details about the flaws exploited in this campaign or the compromised Netgear, Huawei, and ZTE gateway models.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.