The fight against cybercrime is one of the main responsibilities of the ethical hacking and cyber security community. This effort depends on multiple variants, from the elaboration of a functional strategy for the prevention of cyberattacks to the monitoring of the main cybercriminal trends; in other words, those responsible for cyber security must know how hackers think to anticipate their actions and, where appropriate, repair the damage caused.
Developing a functional cyber security strategy not only requires knowing everything about vulnerable software, social engineering campaigns or malware variants employed by hackers, as it is also necessary to know what kind of physical equipment threat actors use during their attacks.
This time, cyber security experts from the International Institute of Cyber Security (IICS) will show you a list of the most popular devices in the cybercriminal and ethical hacking community. Before continuing, we remind you that this article was prepared for informational purposes and should not be taken as a call to action, so IICS is not responsible for the misuse that may be given to the information contained herein.
Sniffer USB
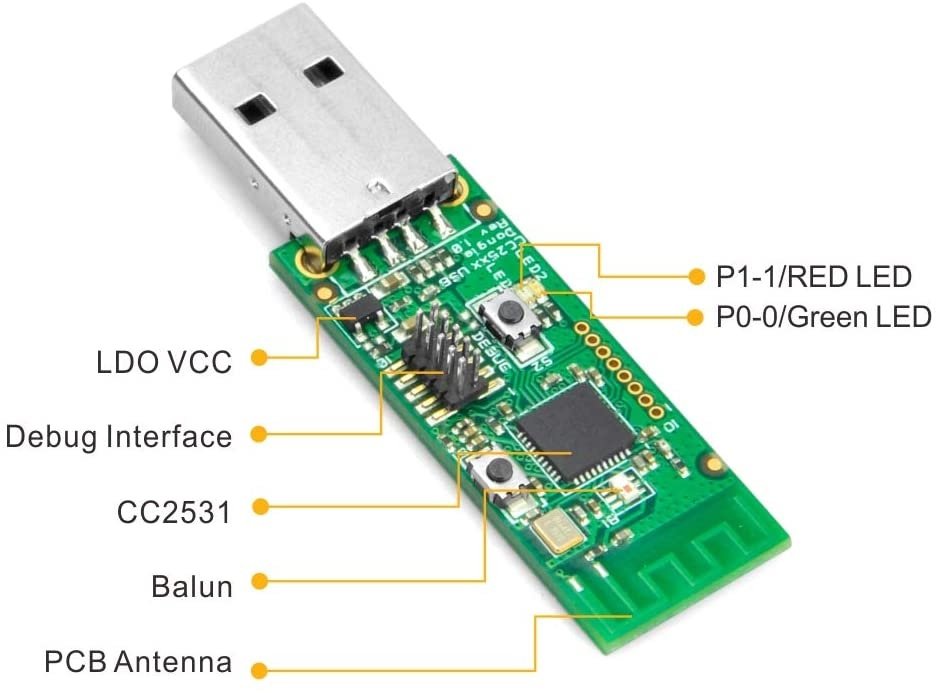
The term USB sniffer refers to devices capable of intercepting traffic on the affected networks, and can be really useful for threat actors during the network diagnostic process and even to intercept user passwords.
These devices can intercept all detected packets, or only the first bytes of any ftp, telnet, pop3 and others. According to cyber security experts, sniffers work from the premise that some passwords are transmitted over the network in clear text, which makes them vulnerable.
Yagi Antenna

Yagi antennas are a kind of longitudinal radiators used to detect radio wavelengths in a very wide spectrum; in other words, they can pick up very high frequencies and even the lowest frequencies known.
In Yagi antennas the interaction between elements is used, in which standing waves of current arise, as a result of which a traveling wave with a pronounced directional pattern appears. Such an antenna consists of one or more active vibrators and additional passive elements.
USB-Bluetooth

These devices allow users to connect a PC with other Bluetooth equipment, whether smartphones, other PCs and all kinds of technology. According to cyber security experts, data exchange occurs through a radio channel.
The range of these devices depends on the characteristics given by the manufacturer, although they can reach up to 100 meters in an open space. Employing a USB-Bluetooth adapter, threat actors can establish communication between two nearby computers and even take control of keyboards, mice, and other devices.
LAN Tap

These are devices that connect directly to a computer network cable and create a copy of the network traffic, which in turn will be sent to another location. LAN taps are normally used in the implementation of intrusion detection systems, although they are also used by malicious hackers.
The logic of these devices depends on the “request-response” scheme, cyber security experts say. Before executing a request to perform an operation, it is necessary to populate the Request data object with a certain set of values, passing this data object to the given interface.
DSTIKE Deauthenticators

This is a technology created to disconnect any wireless device from an access point. Unlike a signal jammer (based on interrupting a signal using another stronger signal), deauthenticators work at the software level, deploying a denial of service (DoS) attack against the target access point, cyber security experts say.
Usually, deauthentication is part of a complex network attack, as it is used to create an “evil twin” of the access point or to intercept a handshake process that eventually allows malicious hackers to crack a password or access sensitive information.
USB “rubber ducky”

It looks and behaves like a conventional USB drive, but it’s actually an advanced hacking tool, cyber security experts say. A rubber ducky allows threat actors to compromise almost any system in a matter of seconds, transmitting a large number of commands to the affected system via a WiFi connection.
The target recognizes the rubber ducky as a standard HID keyboard and serial port, allowing interactive commands and scripts to be executed remotely, representing a considerable attack opportunity.
Smart Key Cloner

This device copies the data from any smart key to turn it into a new device, cyber security experts mention. In addition, this device is not limited to copying smart keys, but works with any type of chip and its use does not require a connection to a PC.
IP Microcamera

An IP microcamera is so tiny that it can be hidden almost anywhere. In the case of a hacking campaign, threat actors will want to hide these devices in locations close to the target in order to inadvertently monitor their activities and discover the victim’s passwords.
WiFi Repeater

These devices copy the features of a WiFi network in order to increase its range. The power these devices supply depends on the router itself, so users don’t have to worry about turning these devices on and off every time they connect to their home WiFi network.
An important feature of the device is the LAN port, through which it can bring up to 100 Mbps of traffic through the cable without charging the air and improving the quality of the network as a whole, plus there are two external 3dBi antennas and an integrated 16dBM transmitter.
USB Data Blocker
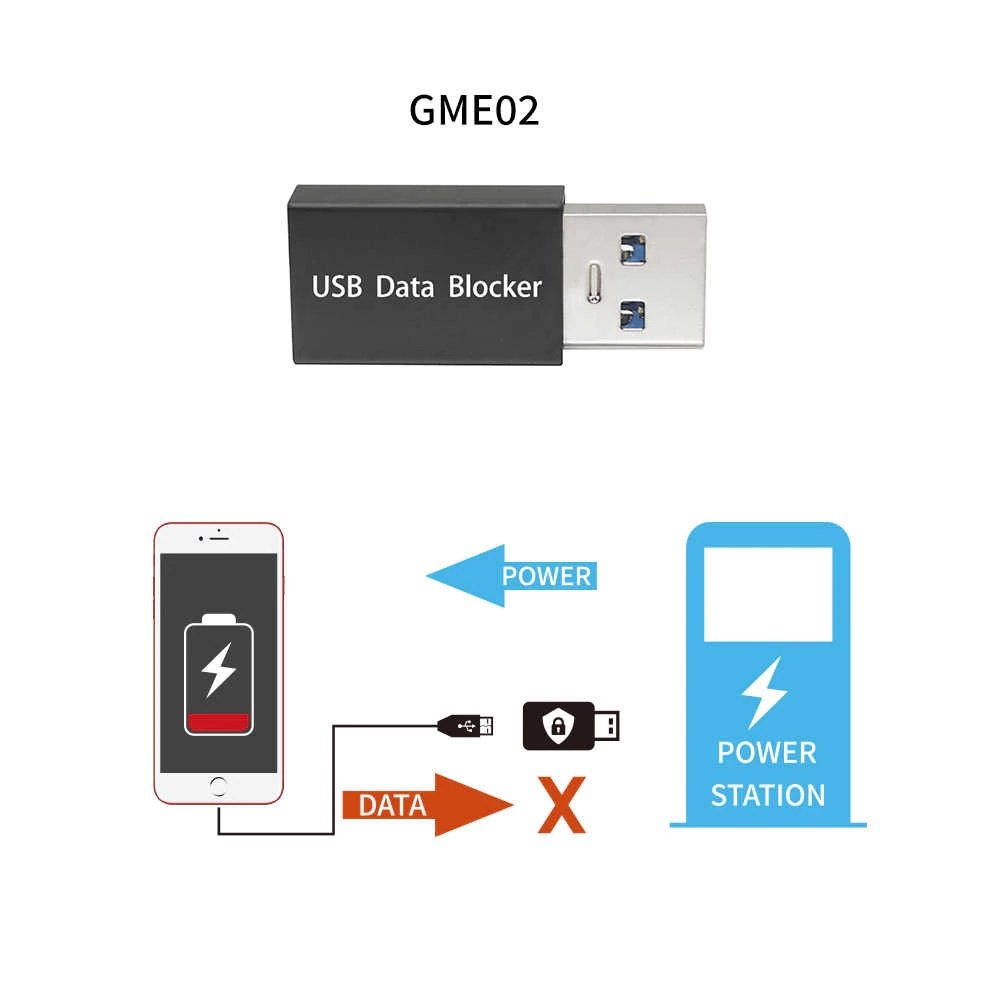
According to cyber security experts, a USB data blocker prevents the transfer of unauthorized data when charging a smartphone or any other device through a USB port. These devices are especially useful when charging a smartphone in public places such as shopping malls, airports, and public transport stations.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











