Avanan cybersecurity specialists report the detection of a new phishing method in which threat actors look for susceptible targets among low-ranking employees who have access to an organization’s IT structure.
Usually, a phishing attack involves the usurpation of the identity of a senior executive in an organization, which makes sense if we remember that in these attacks hackers will appeal to the authority of these people to achieve their objectives, usually related to financial fraud.
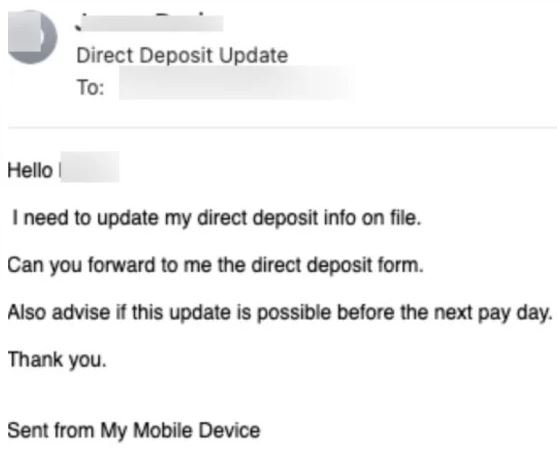
As cybersecurity experts and company directors began to take more careful stances, threat actors had to rethink their approach, targeting lower-ranking employees but capable of accessing sensitive information. In the example shown below, we can see that a target employee with access to the company’s financial systems receives a request to update data from a direct deposit.
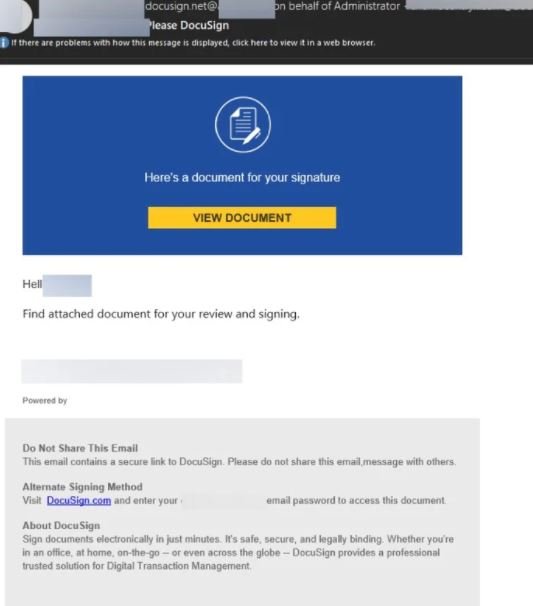
Avanan experts also noted that these attacks typically involve the use of DocuSign, a cloud platform for document signing, which gives a legitimate look to phishing messages. Hackers ask users to enter their credentials to sign the sent document, which will allow attackers to intercept sensitive data.
Phishing attacks are still as effective as ever, so it’s critical that users have the knowledge they need to differentiate legitimate content from a potential threat. Remember that when receiving an email from unknown users, you should try to identify unsolicited attachments, spelling errors, and login windows, as these factors indicate a potential phishing attack.
If you identify a security threat, do not interact with the message received and notify your organization’s IT department, where they will find the best way to deal with this security risk.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











