Zoom Video Communications security teams announced the patching of several vulnerabilities in their local solutions for video conferencing and other products, including Zoom Meeting Connector Controller, Zoom Virtual Room Connector and Zoom Recording Connector, among others.
Egor Dimitrenko from security firm Positive Technologies mentions that successful exploitation of the detected flaws would have allowed threat actors to inject malicious commands to escalate their privileges on the affected systems. It should be remembered that the Zoom videoconferencing platform is one of the most used today, covering more than 40% of the current market.
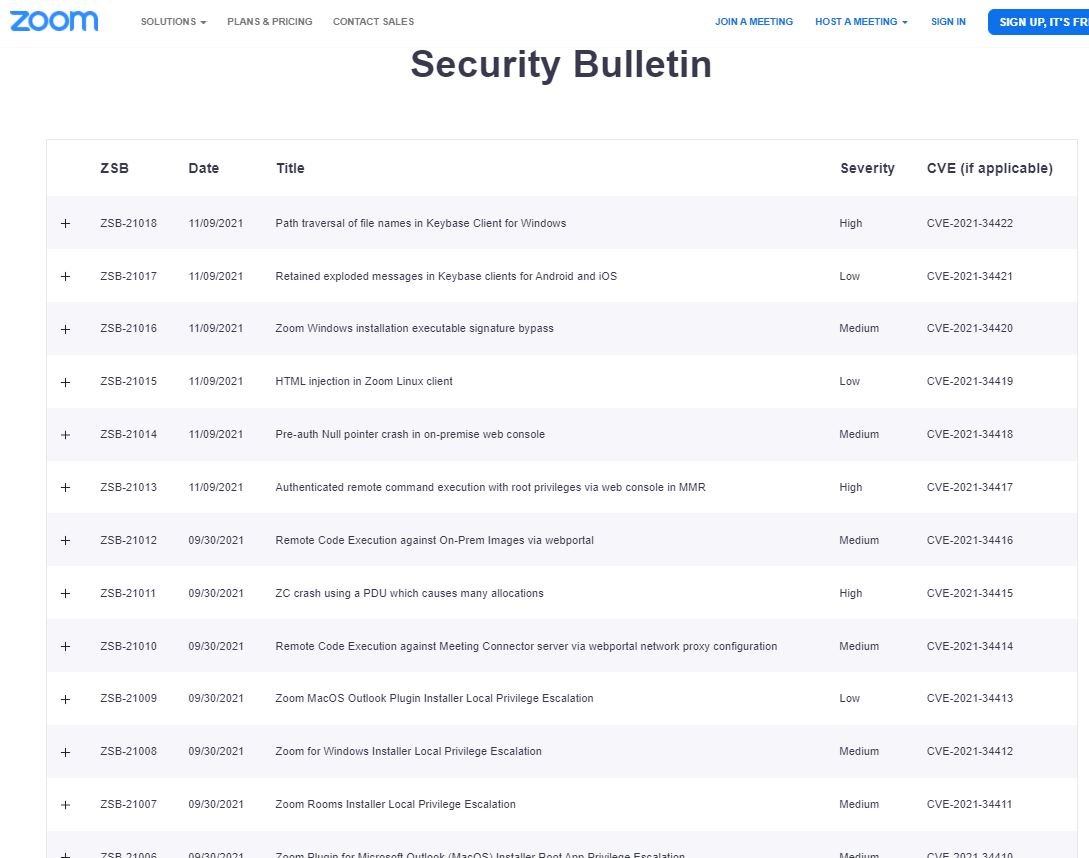
Experts note that the injection of malicious code is possible thanks to the exploitation of CVE-2021-34414, a security flaw in Zoom products that received a score of 7.2/10 according to the Common Vulnerability Scoring System (CVSS).
According to the report, the flaw lies in the following implementations:
- Zoom Meeting Connector Controller up to version 4.6.348.20201217
- Zoom Meeting Connector MMR up to version 4.6.348.20201217
- Zoom Recording Connector up to version 3.8.42.20200905
- Zoom Virtual Room Connector up to version 4.4.6620.20201110
- Zoom Virtual Room Connector Load Balancer prior to version 2.5.5495.20210326
The second vulnerability, tracked as CVE-2021-34415, received a CVSS score of 7.5/10 and its successful exploitation could lead to severe failures in the affected system. The vulnerability resides in Zoom On-Permise Meeting Connnector Controller and has been updated for version 4.6.358.20210205.
Finally, experts found that CVE-2021-34416 could facilitate some risk scenarios by injecting certain commands. The flaw received a CVSS score of 5.5/10 and resides in the following implementations:
- Zoom Meeting Connector up to version 4.6.360.20210325
- Zoom Meeting Connector MMR up to version 4.6.360.20210325
- Zoom Recording Connector up to version 3.8.42.20200905
- Zoom Virtual Room Connector up to version 4.4.6620.20201110
- Zoom Virtual Room Connector Load Balancer prior to version 2.5.5495.20210326
Dimitrenko believes that these flaws exist due to the lack of proper verification in the data entered by users: “These kinds of failures are often found in applications to which server administration tasks have been delegated. These errors could have critical consequences and, in most cases, cause threat actors to gain full control over the compromised network infrastructure.”
Given the characteristics of the affected applications, it will be best to wait for the company to issue the necessary security patches to mitigate the exploitation of these flaws. Zoom did not elaborate on the reported flaws, but recommends users of affected deployments update as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











