Intel security teams announced the detection of two critical vulnerabilities in a wide variety of products and whose exploitation would allow threat actors to perform privilege escalation attacks on affected devices. Tracked as CVE-2021-0157 and CVE-2021-0158, the flaws received a score of 8.2/10 according to the Common Vulnerability Scoring System (CVSS).
In the report, the first vulnerability was described as insufficient management of the control flow in the BIOS firmware for some Intel processors, while the second flaw is based on incorrect input validation in the same component. The reports were submitted by security firm SentinelOne.
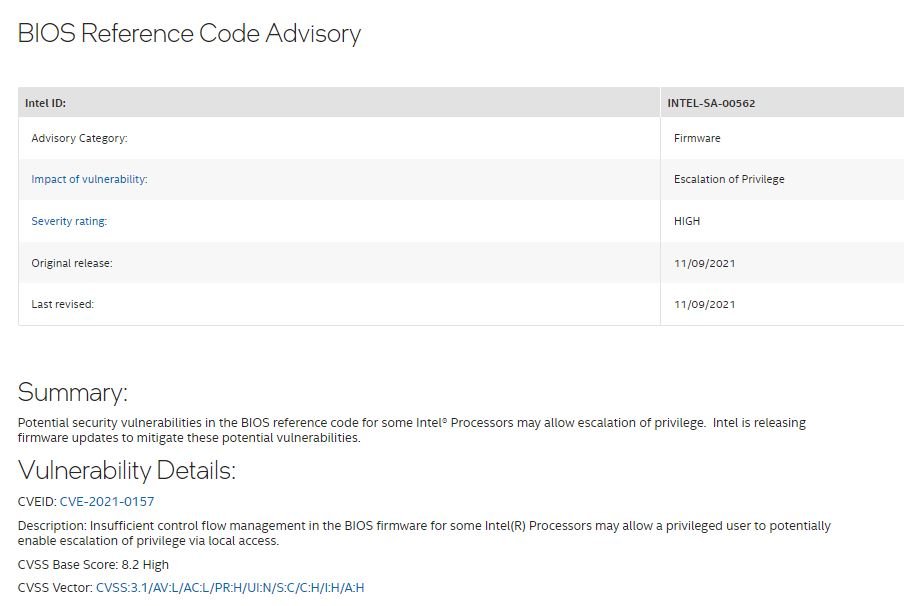
Although privilege escalation flaws could put systems exposed to this flaw at risk, a successful attack would require local access to the affected system. Below is a list of the affected products:
- Intel Xeon processors
- Intel Xeon E3 v6 processors
- Intel Xeon W processors
- Third-generation Intel Xeon Scalable processors
- 11th Generation Intel Core processors
- Tenth generation Intel Core processors
- Seventh generation Intel Core processors
- Intel Core X-Series Processors
- Intel Celeron N-series processor
- Intel Pentium Silver processors
While Intel has not shared additional details about exploiting the flaw, the company recommends administrators of affected deployments upgrade as soon as possible. The update process could prove problematic because motherboard vendors don’t release BIOS updates frequently and don’t support their products with security updates for a long time.
Considering that seventh-generation Intel Core processors were released in 2015, it’s doubtful that vendors will keep releasing security BIOS updates for them, so some users will be left without a practical way to fix the above flaws and will have to resort to a workaround.
In addition to these reports, Intel addressed a privilege escalation vulnerability tracked as CVE-2021-0146 and with a CVSS score of 7.2/10. According to the report, the affected products allow the activation of test or debug logic at run time for some Intel processors, allowing an unauthenticated user to enable the error with prior physical access.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











