Mobile security specialists from IMB Trusteer have confirmed the reappearance of BrazKing, a banking Trojan for Android devices distributed through third-party applications and which employs a complex SMS phishing campaign to attract potential victims. According to the researchers, this new iteration allows malware to operate almost inadvertently, avoiding requesting too much permission on the target system.
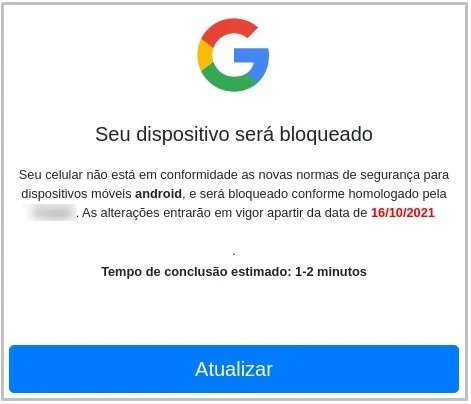
If users click on the links attached to the SMS, they will be redirected to HTTPS-certified websites where the victim is warned that their Android version is outdated, so they offer to download an APK to perform a supposed update.
When users download this APK, the Trojan will install itself on the device and ask for permission to access the “Accessibility Service”. The compromise of this feature allows threat actors to take screenshots and record keystrokes without requesting access to other system functions.
In addition to the tasks mentioned, hackers use the Accessibility Service for other activities, including:
- Manipulation of banking applications in a function similar to a remote access Trojan (RAT)
- Access to SMS messages without the android.permission.READ_SMS permission, which would allow access to multi-factor authentication tokens
- Access to contact list without android.permission.READ_CONTACTS permission
Another standout feature of BrazKing is its ability to evade a security feature in Android 11 that prevents apps on Google Play from accessing the list of apps installed on a device. Attackers can display fake screens in the form of a URL from the malicious server in a web view window, added from the Accessibility Service.
Experts believe that the evolution of BrazKing is a sign of the adaptability of cybercriminals, since they have achieved a tool capable of intercepting all kinds of confidential information without requesting lots of permissions.
The ability to intercept authentication tokens and other verification codes certainly puts affected users at severe risk. As in other hacking campaigns that start from phishing, the best protection is to ignore suspicious messages and not install applications from unofficial sources.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











