Updating all the software solutions that we use daily is one of the main cybersecurity practices, since it allows us to keep our systems always protected by applying the corrections that the manufacturers of these products prepare for the possible exploitation of security flaws. However, it is necessary to stay alert, as threat actors can also use fake updates to hack our systems.
For years, hacking groups have used malicious updates jointly with phishing campaigns to launch attacks against unsuspecting users. In the most recent campaign, reported by Malwarebytes, it has been detected that users of the Microsoft Edge web browser are receiving a fake update that hides a malicious payload.
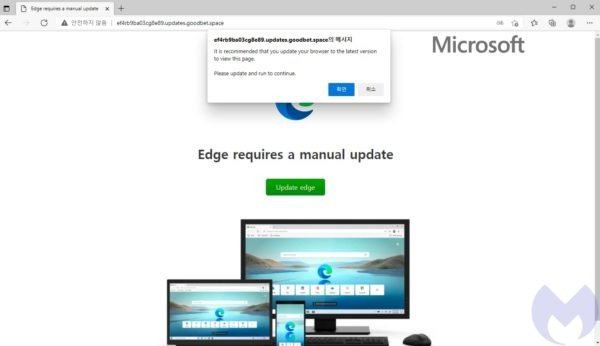
This malicious update delivers the Magnitude exploit kit, a set of tools that aim to install a powerful ransomware variant known as Magniber. The campaign was detected a few weeks ago and focuses on users in South Korea.
According to experts, the attack follows a fully identifiable chain and described below:
- The target user visits a malicious website
- This ad redirects the user to Magnigate malware
- Magnigate runs IP address and browser checks to determine if the user meets the criteria for choosing a victim; if so, Magnigate will redirect the user to a home page of the exploit kit
- The exploit kit chooses a way to attack the user; in this case the malicious microsoft edge update
- This fake update hides a malicious Windows application package (.appx) file
- The .appx file downloads the Magniber ransomware, which will start encrypting the compromised files
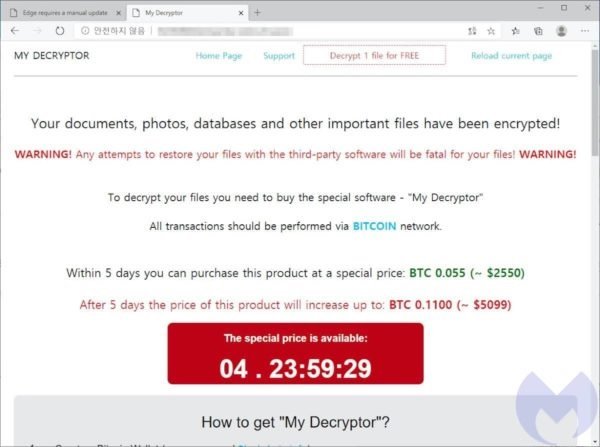
At the moment it is unknown if this campaign pursues specific objectives beyond demanding the ransom of the affected users, although the researchers do not rule out that behind this campaign there is hidden activity of state threat actors.
In the past, the Magnitude malware has exploited known vulnerabilities in Flash and Internet Explorer, although it can easily adapt to the latest trends. In December 2021, this malware also began exploiting a sandbox bypassing vulnerability in Chrome browsers.
It is worth mentioning that Edge is based on the same browser as Chrome, uses the same V8 JavaScript engine, and is vulnerable to the same security flaws. Still, its exploitation is only possible in outdated web browsers, so the best way to prevent an attack is to keep your browser always updated to the latest version available; if you want to know which browser version your system is running, just go to the Settings menu in Microsoft Edge.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











