A few weeks ago the cybersecurity firm SecureList detected a series of attacks at the firmware level in which the image of the security mechanism was modified by the threat actors so that they could intercept the original execution flow in the boot sequence of the target system to implement a complex chain of infection.
Experts say that in recent months there has been a significant increase in threats targeting Unified Extensible Firmware Interface (UEFI) implementations. These threats include a UEFI boot kit used as part of the FinSpy surveillance toolkit, the ESPectre bootkit, and a recently detected operation impacting organizations in the Middle East.
A common point among these malicious operations is that the affected UEFI components is that the affected UEFI components reside in EFI System Partition (ESP), storage space created for some UEFI components. Key elements of ESP include the operating system bootloader and loader, invoked during the system boot sequence and which can be affected by malicious bootkits.
In addition to these security issues, the finding of a different type of bootkit composed of implants residing in the UEFI firmware within the SPI flash stands out. These types of bootkits are very stealthy and difficult to mitigate, making them a considerable security threat.
The bootkit identified by SecureList, dubbed MoonBounce, is considered a particular evolution in this class of threats, as it is characterized by its complex attack flow compared to similar hacking tools, in addition to the obvious technical capabilities of its developers.
After a detailed analysis, the researchers found some of the main features of MoonBounce:
- UEFI firmware is manipulated to embed the malicious payload
- Due to its location in the SPI flash, the implant is able to persist in the system despite formatting or replacement of the hard drive
- The main purpose of the attack appears to be the implementation of user-mode malware to organize the execution of more payloads downloaded from the Internet
Threat actors incorporated the UEFI implant into the CORE_DXE component of the firmware, which is called from the beginning in the Driver Execution Environment (DXE) phase of the UEFI boot sequence. The infection begins with a set of hooks that intercept the execution of various functions in the EFI boot services table, including AllocatePool, CreateEventEx, and ExitBootServices. Those hooks divert the flow of these functions to a malicious shellcode that attackers add to the image CORE_DXE, which in turn configures additional hooks on the back components of the boot chain, including the Windows system loader.
This chain of hooks facilitates the deployment of malicious code from the image CORE_DXE to other components during system boot, allowing the introduction of a malicious driver into the memory address space of the Windows kernel. In turn, this driver is responsible for implementing the malware in user mode by injecting it into a svchost.exe process; finally, the user-mode malware arrives at an encoded C&C URL (hxxp://mb.glbaitech.com/mboard.dll) and attempts to obtain another stage of the payload to run in memory, which the researchers were unable to retrieve.
In the image below, we can observe the stages taken from the moment the boot services are called hooked in the context of the execution of DXE Foundation to the implementation of the malware in user mode and it runs during the execution of the operating system.
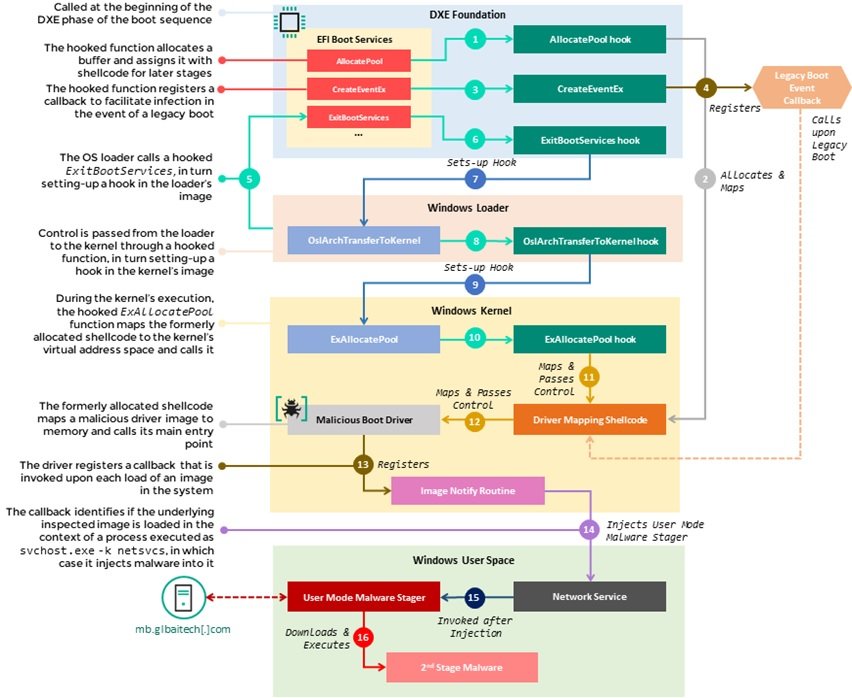
At the moment it is unknown how it is that the threat actors manage to carry out the firmware infection, although it is known that it is a process carried out remotely. While similar threats above manifested as additions of DXE drivers to the overall firmware image in the SPI flash, in this case a much stealthier technique can be seen in which an existing firmware component is modified to alter its regular behavior.
The particular functions were modified with an inline hook, which means replacing the prologue of the function with a specific instruction to divert the execution to a function determined by the threat actors. This form of binary instrumentation requires hackers to obtain the original image and then analyze and change it to introduce malicious logic, which involves remote access to the target system.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











