Earlier this week, VMware announced the correction of multiple critical vulnerabilities in products such as VMware ESXi, Workstation and Fusion, most of them reported during last year’s Tianfu Cup ethical hacking summit in China.
During the event he highlighted the work of the Kunlun Lab hacking team, which won rewards of more than $650,000 USD for their work demonstrating the exploitation of some of these flaws.
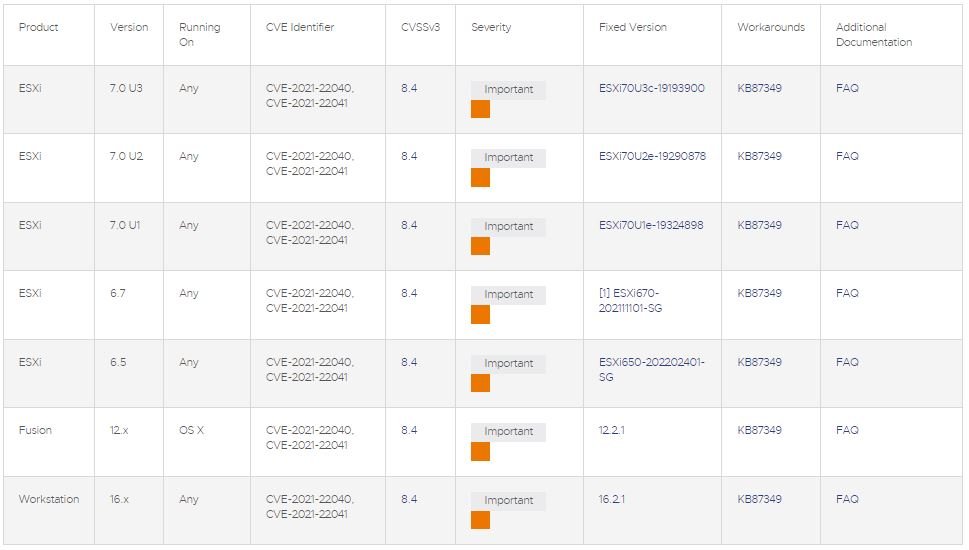
Below is a brief description of the failures addressed according to a company report:
- CVE-2021-22040: A use-after-free error in the ESXi, Workstation, and Fusion XHCI USB driver whose exploitation would allow local threat actors with administrator privileges to execute code as the VMX process of the virtual machine running on the host
- CVE-2021-22041: A bug in the ESXi, Workstation, and Fusion USB UHCI driver would allow local attackers with administrator privileges to execute code as the VMX process of a virtual machine running on the host
- CVE-2021-22042: Unauthorized access to settingsd in ESXi would allow malicious hackers within the VMX process to escalate their privileges on the affected system
- CVE-2021-22043: A settingsd TOCTOU error in ESXi that exists due to the way temporary files are handled would allow threat actors to escalate their privileges on the affected system
The firm has also announced some alternative solutions for administrators who cannot update their implementations at the moment, in addition to recommending that clients apply the measures they consider necessary as soon as possible since the successful exploitation of these failures could result in catastrophic scenarios.
Finally, VMware mentioned that these failures were notified to the Chinese government, in compliance with a recently enacted law that states that Chinese researchers who find zero-day vulnerabilities must notify government agencies and manufacturers of the affected technology directly. Researchers will not be able to sell this information to third parties outside of China unrelated to the manufacturer/developer.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











