Cybersecurity specialists published a report that points out how AirGuard, an application for Android that allows users of this operating system works detecting an Apple AirTag device potentially used for malicious purposes.
Launched in April 2021, this device allows iPhone users to track their devices through the Find My service. However, it has been reported on multiple occasions that malicious users can use them to track a person without permission, stealthily hiding them in a backpack, clothing or any other similar site.
Despite Apple’s efforts to counter malicious use of these devices, this remains a severe problem, especially when the tracked user does not have a tool to detect an Apple device from the abusive behavior patterns established by the company.
In 2021 Apple launched the Tracker Detect app for Android users, which would inform users that there is an AirTag enabled in a nearby location. However, the app only informs the user if it is being tracked, so it is not really a reliable tool.
The researchers decided to reverse engineer iOS tracking detection to better understand its inner workings and then design the AirGuard app, for automatic detection of any passive tracking activity and that works with all Find My accessories in addition to the AirTag.
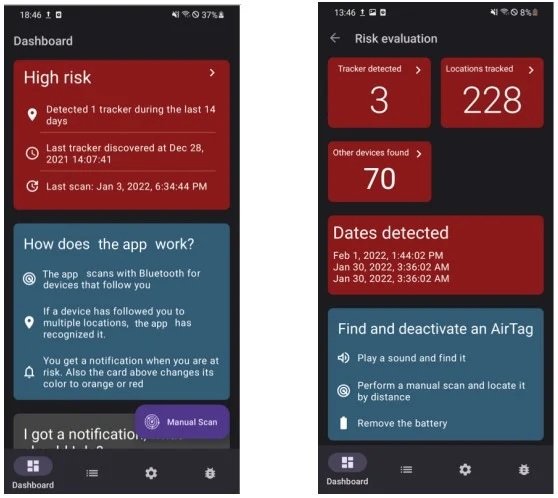
The app was launched at the end of 2021 through the official Google Play Store platform and already has about 120,000 users. With this tool it will be possible to detect all the devices of the Find My family, including the AirTags modified for tracking and espionage purposes.
The app will also be able to detect any AirTag placed in a car, which can prove difficult even for other tools from Apple itself. Finally, the researchers acknowledge that the main weakness during their testing is the limited scanning opportunities on the Android operating system, so the scope of the search could be limited.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











