The cybersecurity community understands as cyber forensics the procedures and methodological techniques to identify, collect, preserve, extract, interpret, document and present the evidence of an investigation on a computer system, so that these reports can demonstrate or rule out malicious activity on the affected systems.
Specialists say that this research plays a fundamental role in the investigation of cybercriminal incidents, although sometimes researchers face multiple questions and crossroads during the analysis, increasing the workload unnecessarily. That is why it is necessary to find a way to make these processes more efficient.
On this occasion, experts from the cyber forensics course of the International Institute of Cyber Security (IICS) will show you Hoarder, a script created to collect and analyze the most valuable elements for forensic investigations or incident response instead of creating images of the entire hard drive.
Available on GitHub, this tool can represent a great advantage for cyber forensics investigation, lightening the workload of experts and allowing defining the most characteristic features of a cyberattack.
Tool usage
Hoarder analyzes the Hoarder.yml configuration and produces an extensive help message for ease of use, mention the experts of the cyber forensics course.
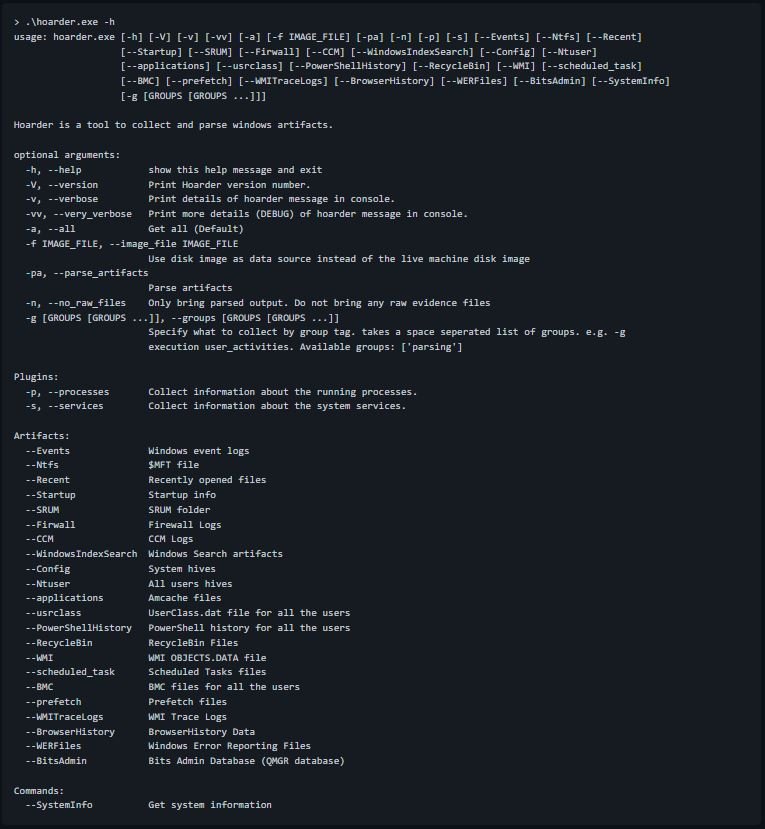
For example, if you want to collect all the artifacts specified in Hoarder.yml, you must use the following commands:
> .\hoarder.exe –all or > .\hoarder.exe -a or just > .\hoarder.exe
At the end of the execution, a ZIP file called <HOSTNAME>.zip will be generated, which contains all the artifacts in addition to hoarder.log which contains the debug records of the script.
To collect all artifacts with group tag analysis, run the command:
> .\hoarder.exe -g parsing
Configuration
The tool has a default configuration (Hoarder.yml):
- If you are running from the binary executable: The default Hoarder.yml settings are embedded in it. if you place your own hoarder.yml next to hoarder.exe you use it instead of the default settings
- If you are running from the source, you can modify Hoarder.yml or rename it and name your own Hoarder.yml configuration
Here’s an example of collecting and analyzing files or folders:
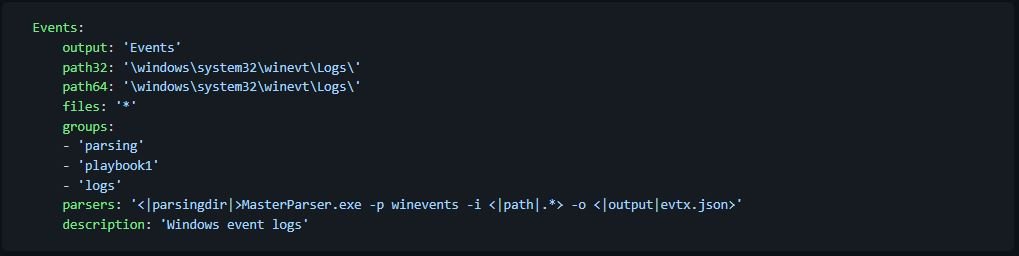
- Events: Name of the artifact. this name will be used as an argument on the hoarder command line
- Output: Output folder for this artifact
- path32: Path to the artifact for 32-bit systems
- path64: Path to artifact for 64-bit systems
- Files: File names
- Groups: They function as tags and each artifact can be configured to be part of one or more groups
- Parsers: One or more parsers to run this artifact
Parsing
Starting with version 4.0.0, Hoarder has support for the analysis of collected artifacts. As mentioned in the IICS cyber forensics course, there are three main parts to the analysis:
- parsers.zip: Contains the binaries, scripts, and data files of your parser To add your own parsers, place a parsers.zip file next to hoarder.exe containing all the parsers used
- configuration: in Hoarder.yml, add your parser command
- command-line arguments: -pa for the accumulator to bring raw and analyzed artifacts, and -n for the accumulator to bring only analysis results
Commands and plugins
The researchers of the cyber forensics course mention that the tool contains the following features:
- Pluings: Preset functions within the script that can be called for specific results, such as processes and services
- Commands: Defined within Hoarder.yml to execute unique built-in commands
The tool also supports the execution of system commands. The following example shows the execution of the systeminfo command:

To learn more about information security risks, malware variants, vulnerabilities and information technologies, and more information on the cyber forensics course feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











