Cybersecurity specialists have found a variant of “replay attack” that would allow threat actors to unlock and even start some models of keyless cars manufactured by Honda and Acura from a nearby location. According to the report, the attack consists of hackers capturing radio frequency signals sent from an electronic key fob to the car, which would allow them to take control of the target system without using the authentic key.
The report indicates that the vulnerability especially affects older keyless car models, although fortunately there are methods to protect against this variant of hacking.
Tracked as CVE-2022-27254, this flaw was described as a variant Man-in-The-Middle (MiTM) attack, or replay attack, in which cybercriminals intercept radio frequency signals that are normally sent from a remote key fob to the car, manipulating these signals and sending them back at a later time in order to unlock the car doors.
This report was presented by researchers Blake Berry, Hong Liu, Ruolin Zhou and Sam Curry, who even released a video demonstrating the deployment of the attack. The researchers mention that the attack is functional mainly on Honda Civic models (LX, EX, EX-L, Touring, Si, Type R) launched between 2016 and 2020.
These kinds of mistakes are more frequent than you might think. In 2020, Berry reported a similar flaw in other Honda models, claiming that the auto company simply ignored its report, exposing millions of drivers of models like.
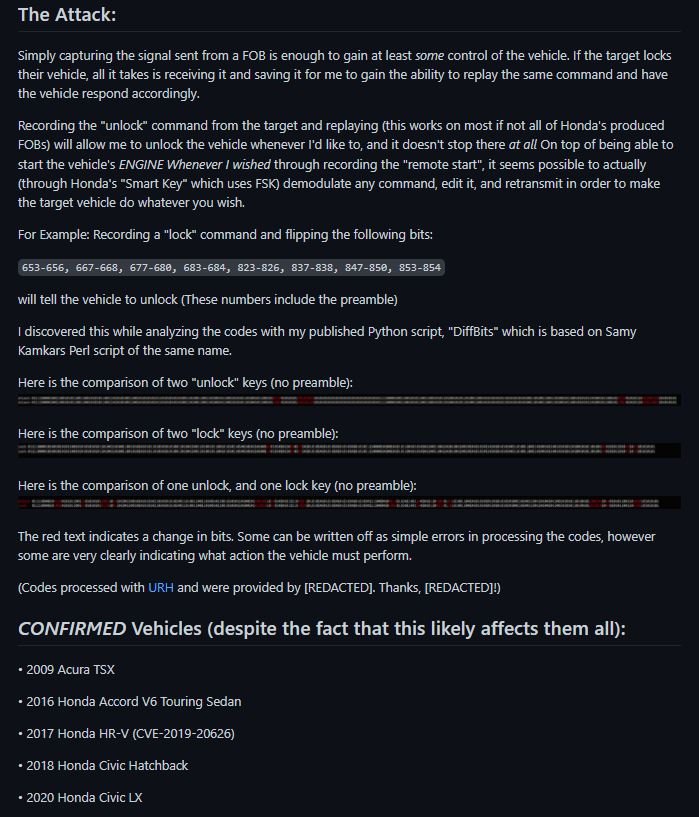
- 2016 Honda Accord V6 Touring Sedan
- 2017 Honda HR-V
- 2018 Honda Civic Hatchback
- 2020 Honda Civic LX
Apparently this will be the case for this new vulnerability, as Honda has shown no plans for cars with legacy technology: “It appears that these attacks only work from a location very close to the target car, which requires local reception of radio signals from the vehicle owner’s key fob when the vehicle is opened and turned on nearby,” a company spokesperson said.
Honda does not confirm or deny that some of its models may be affected by this specific vulnerability, although it acknowledges that, if so, there are no plans to upgrade older vehicles, at least for the time being: “It is important to remember that while we are working to implement more advanced security features in the new models, threat actors are also working to improve their forms of attack,” the spokesperson adds.
Given this panorama, the researchers recommend that the owners of these vehicles keep the keys in a container capable of inhibiting the radio frequency signals emitted by these devices, in the effect known as Faraday’s cage. These attacks depend entirely on intercepting the signal, so an inhibitor will almost completely mitigate the risk of theft.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











