Claroty cybersecurity specialists report the identification of two serious vulnerabilities whose exploitation would allow threat actors to deploy severe attacks targeting programmable logic controllers (PLC) developed by Rockwell Automation. The company’s findings were disclosed through the Cybersecurity and Infrastructure Security Agency (CISA).
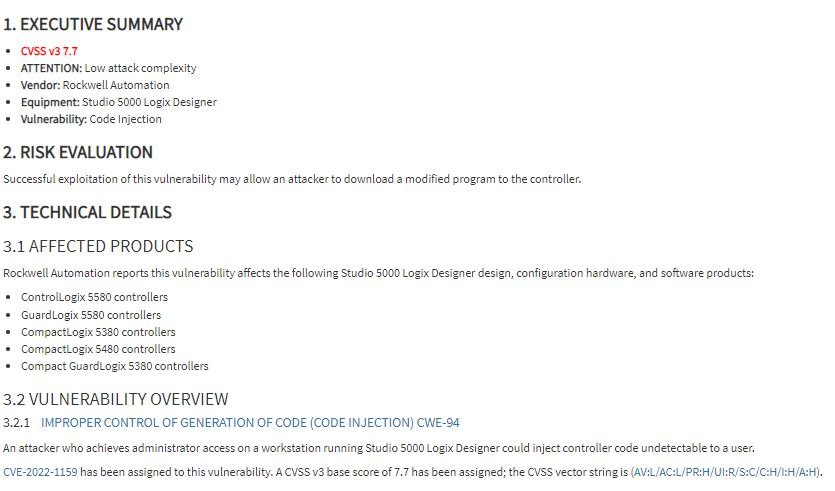
The first of the flaws, tracked as CVE-2022-1161, is considered a critical security bug and resides in several CompactLogix, ControlLogix, GuardLogix, FlexLogix, DriveLogix and SoftLogix controllers. On the other hand, CVE-2022-1159 is a high-severity flaw affecting the Studio 5000 Logix Designer programming software, running on engineering workstations.
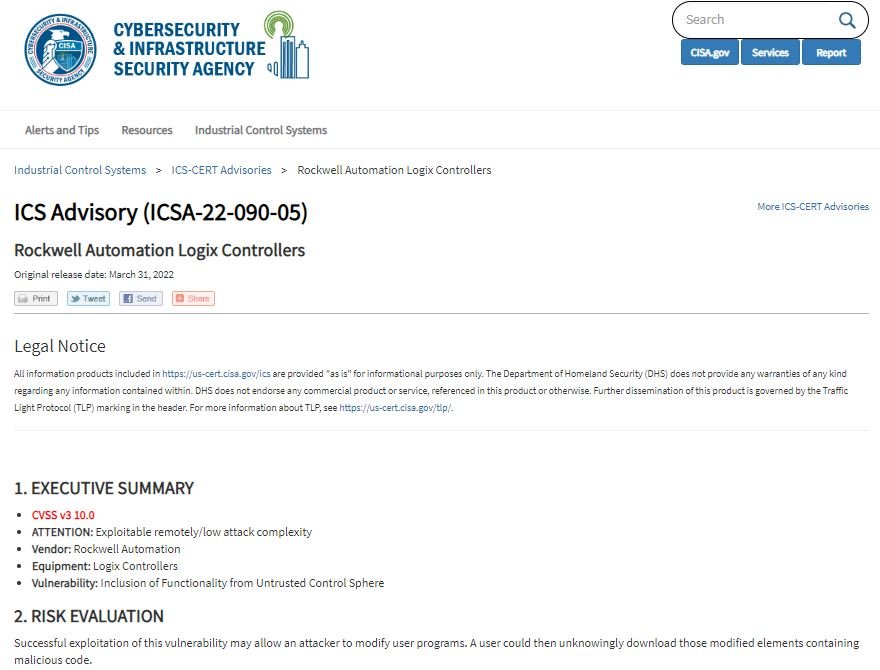
Successful exploitation of the vulnerabilities would allow threat actors with access to the affected systems to make changes to the PLC program code and modify automation processes without being detected. A successful attack could result in severe damage to systems linked to PLC implementations.
As mentioned above, this attack scenario is similar to that of the Stuxnet malware, used more than 10 years ago jointly by the United States and Israel to attack critical infrastructure in Iran.
Claroty’s report points out that those hackers with the ability to modify the logic of PLC implementations could cause critical damage to the industrial environments where they are installed, causing interruptions and flaws in critical systems.
At the time, Stuxnet managed to compromise all kinds of PLC devices developed by Siemens, but in recent years vulnerabilities have also been found that can be exploited to achieve a similar goal in PLCs manufactured by Schneider Electric and other technology firms.
Rockwell product flaws point to the process of code development and transfer to the PLC, which involves developing the code on an engineering workstation using Studio 5000 software, compiling it into PLC-compatible binary code, and transferring that code from the engineering workstation to the PLC, where it will be executed.
Threat actors could send malicious code to a controller while showing the engineer legitimate code in the programming software. The second flaw can be exploited by threat actors with administrator privileges intercepting the build process and injecting their own code into the user’s program without showing signs of suspicious activity.
The manufacturer has shared some methods to prevent this attack, including launching a hidden code detection tool in PLC implementations.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











