Researchers at Trend Micro identified a set of mobile apps available on the Google Play Store performing malicious tasks in the background, including stealing user credentials and banking details from Android users. Some of these apps have nearly 100,000 downloads, so the scope of the problem is considerable.
In total, the analysis revealed the detection of 200 malicious applications that hide code from dangerous malware variants, capable of putting users of the affected devices in serious trouble.
Simple tools, complex issues
One of the main threats identified is Facestealer, a spyware variant capable of stealing Facebook access credentials, allowing subsequent phishing campaigns, social engineering, and invasive advertising. Facestealer is constantly updated and there are multiple versions, making it easy for them to get into the Play Store.
Daily Fitness OL is described as a fitness tool, offering exercise routines and demonstration videos. Although there doesn’t seem to be anything wrong with this app, an in-depth analysis shows that the app’s code hides a load of The Facestealer spyware.

When a user opens this app, a request is sent to hxxps://sufen168.space/config to download their encrypted settings. This setting sends the user a message requesting to log in to Facebook, after which the app launches a WebView to load a malicious URL. Subsequently, a snippet of JavaScript code is injected into the loaded website, allowing the theft of the user’s credentials.
Once the user logs into their Facebook account, the app collects the cookies and the spyware encrypts the collected information to send it to a remote server.
Other malicious apps, such as Enjoy Photo Editor or Panorama Camera, also hide Facestealer loads and have a very similar attack process, although they may vary in some stages or methods.
Risk for crypto investors
Experts have also identified more than 40 fraudulent cryptocurrency apps disguised as legitimate tools, even taking their image or using similar names. The developers of these tools seek to get affected users to buy supposed Premium versions at high costs with fake ads.
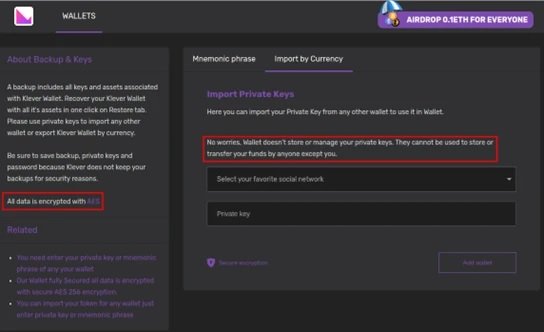
Tools like “Cryptomining Farm Your Own Coin” do not demonstrate invasive behaviors even in test environments, so they effectively evade security mechanisms in the Play Store. However, when trying to connect a Bitcoin wallet to this application, a message appears asking the user to enter their private keys, a clear red flag alerting that something’s wrong.
A sample of the code was developed using Kodular, a free online suite for mobile app development. Trend Micro notes that most fake cryptocurrency apps use the same framework.
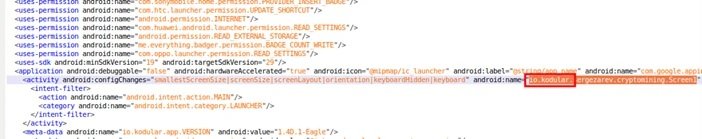
The analyzed app only loads a website and does not even have capabilities to simulate mining processes or cryptocurrency transactions.
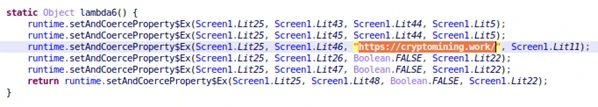
The uploaded website mentions users who can participate in a cloud mining project in order to lure them to the true start of the attack. Next, threat actors ask users to link a digital wallet to this website, in an attempt to collect private keys, which are further processed with no encryption at all.
Although the malicious applications were reported to Google and have already been removed from the official store, the researchers believe that the company must considerably improve security measures in the Play Store, as many developers of malicious applications continue to find methods to evade the security of the app repository, putting millions of users at risk.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











