A recently detected vulnerability affecting Flux, a popular continuous delivery (CD) tool for Kubernetes, would reportedly allow tenants to sabotage the activities of “neighbors” who use the same infrastructure outside of their own facilities.
Flux is an open and extensible CD solution to keep Kubernetes clusters in sync with configuration sources, and is used by firms across all industries, including Maersk, SAP, Volvo, and Grafana Labs, among many others. In its most recent version (Flux2), multi-tenant support was introduced, among other features.
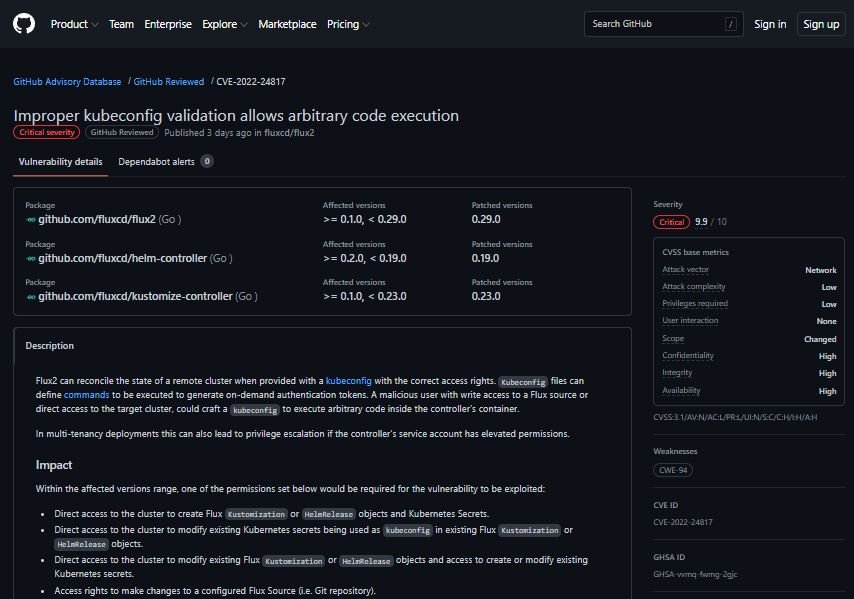
The vulnerability was described as a remote code execution (RCE) error that exists due to improper validation of kubeconfig files, which define commands that will be executed to generate on-demand authentication tokens: “Flux2 can reconcile the state of a remote cluster when a kubeconfig file exists with the correct access rights,” points a report posted on GitHub.
Paulo Gomes, a software engineer who collaborates at the Cloud Native Computing Foundation (CNCF), which originated GitOps and provides support for Flux and Kubernetes, mentions: “The tool can synchronize the declared state defined in a Git repository with the cluster in which it is installed, which is the most commonly used approach, or it can target a remote group.”
Gomes adds that the access required to target remote clusters depends largely on the intended scope. This is completely flexible and is based on the fact that Kubernetes RBAC has a wide range of granularity. This behavior allows a malicious user with write access to a Flux source or direct access to the target cluster to create a specially crafted kubeconfig file to execute arbitrary code in the controller container.
When analyzed according to version 2 of the Common Vulnerability Scoring System (CVSS), this vulnerability was considered of medium severity and received a score of 6.8/10, because in single-tenant deployments, the error is less dangerous and the attackers obtain almost the same privileges required for exploitation.
However, the flaw receives a score of 9.9/10 according to CVSS v3.1, as this release includes a metric around ‘scope’ changes, which means that the flaw can affect resources beyond the security scope managed by the developers of the vulnerable component.
The flaw has already been addressed by the creators of the tool, so users of affected deployments are advised to upgrade as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











