It may not sound familiar to millions of mobile phone users, but Chinese chipmaker UNISOC has been a major member of the industry for just over 20 years. Founded as Spreadtrum Communications in 2001, the company grew rapidly to be present on more than half of Chinese phones by 2011. Currently, the firm produces budget chipsets for Android devices compatible with 2G, 3G, 4G and 5G technology, in addition to smart TVs and more, with a predominant presence in Asia and some regions of Africa and only behind giants such as Qualcomm and MediaTek.
While UNISOC is a major chip producer, its technology has been little analyzed by mobile security specialists, so it is difficult to know what the security risks are present in devices with these chips and there are not even references to any vulnerability detected in their firmware.
A recent research effort was led by Check Point Research, and focuses on the modem of smartphones with UNISOC chips could be a very attractive attack target for cybercriminals, as this component can be accessed remotely and relatively easily, with the potential to deploy denial of service (DoS) attacks and block the communications of the affected devices.
Basic attack concepts
The Long-Term Evolution (LTE) network is made up of a dozen protocols and components, and you need to understand it to understand how the UNISOC modem works. The 3GPP Group introduced the Evolved Packet System (EPS), an LTE technology architecture consisting of three key interconnected components:
- User equipment (UE)
- Evolved UMTS terrestrial radio access network (E-UTRAN)
- Evolved Packet Core (EPC)
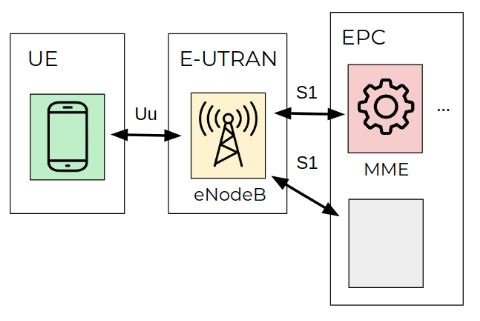
E-UTRAN has only one stack, the eNodeB station, which controls radio communications between the EU and the EPC. A UE can be connected to one eNodeB at a time.
The EPC component consists of four stacks, one of which is the Mobility Management Entity (MME). The MME controls the high-level operations of mobile devices on the LTE network. This component sends signaling messages related to security control, management of tracking areas, and mobility maintenance.
Check Point Research’s tests, conducted by a smartphone with a UNISOC modem, focus on communications between MME and UE stacks, which occur via EPS session management (ESM) and mobility management (EMM) protocols. The following screenshot shows the protocol stack of the modem. The no-access stratum (NAS) level hosts EPS and EMM signaling messages.
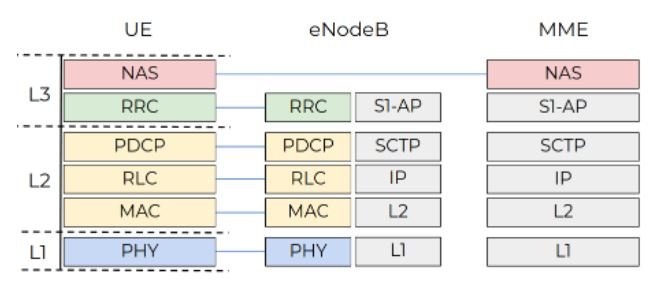
The NAS protocol operates with high-level structures, which would allow threat actors to create specially crafted EMM packets and send them to a vulnerable device, whose modem will analyze it and create internal objects based on the information received.
A bug in the scanning code would allow hackers to lock the modem and even perform remote code execution (RCE) attacks.
Security flaws in NAS handlers
Most NAS message analyzers have three arguments: an output buffer, which is an object of the appropriate message structure, the NAS message data blob for decoding, and the current offset in the message blob.
The unified function format allows you to easily implement the harness to fuzz the NAS analysis functions. Check Point experts used the classic combination of AFL and QEMU to fuzz the modem binary on a PC, patching the modem binary to redirect malloc calls to the libc equivalent. The fuzzer swapped the NAS message data and passed it as an input buffer to the analysis function.
One of the optional fields ATTACH_ACCEPT is mobile identity. The modem firmware implements an unpacking function such as liblte_mme_unpack_mobile_id_ie of srsRAN to extract the mobile identity from the NAS message. The identity data block begins with the length of the identity; if the device is represented by an International Mobile Subscriber Identity (IMSI), the 2-byte length of message data is copied to the output buffer as the IMSI number.
The check is bypassed to ensure that the provided length value is greater than one. Therefore, if the value of the length field is zero, 0-2 = 0xFFFFFFFE bytes of the NAS message are copied to the heap memory, leading to a DoS condition.
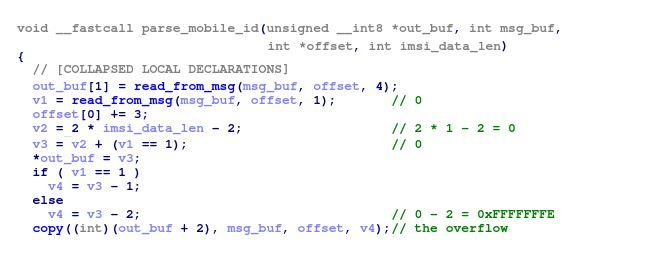
In the following screenshot, you can see the message ATTACH_ACCEPT, which causes the overflow.
Conclusions
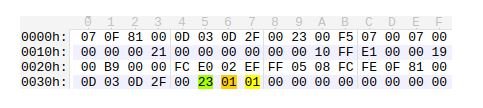
The highlighted 0x23 value indicates that the following data is the identity block of the message, where the first 0x01 is the length and the second 0x01 is the IMSI type.
UNISOC is aware of this condition, and has already been assigned the identification key CVE-2022-20210. While the hacking variants described by Check Point are not easy to exploit and require great resources and planning, the possibility of exploitation is real and should not be dismissed.
Errors will be properly addressed, protecting millions of smart device users. Google is also aware of the report and will issue some additional protections for the Android system.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











