Avast researchers developed a decryption tool for the TaRRaK ransomware, a malware variant detected in mid-2021 and characterized by multiple errors in its coding and encryption process. Thanks to this tool, victims will be able to recover their encrypted files without negotiating with TaRRaK operators.
Before learning about the decryption tool, let’s take a look at some details on the development of ransomware, in addition to its encryption process and mistakes made by its creators.
Development & behavior
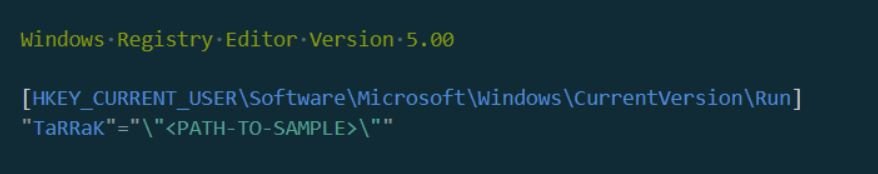
TaRRaK is written in .NET and its code is not protected with obfuscation or any other bypass method. When executed, the ransomware creates a mutex identified as TaRRaK to ensure that only one instance of the malware runs, in addition to creating an auto-start registry entry to run the ransomware on each login of the target system:
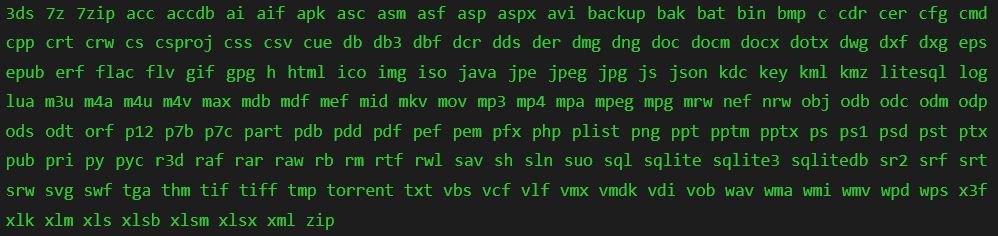
The ransomware contains a list of 178 file extensions:
After avoiding folders with strings such as $Recycle.Bin, :\Windows, \Program Files, \Local\Microsoft\, and :\ProgramData\, the encrypted files receive the .TaRRaK file extension:
Flaws at encryption
The source code and encryption process are riddled with bugs:
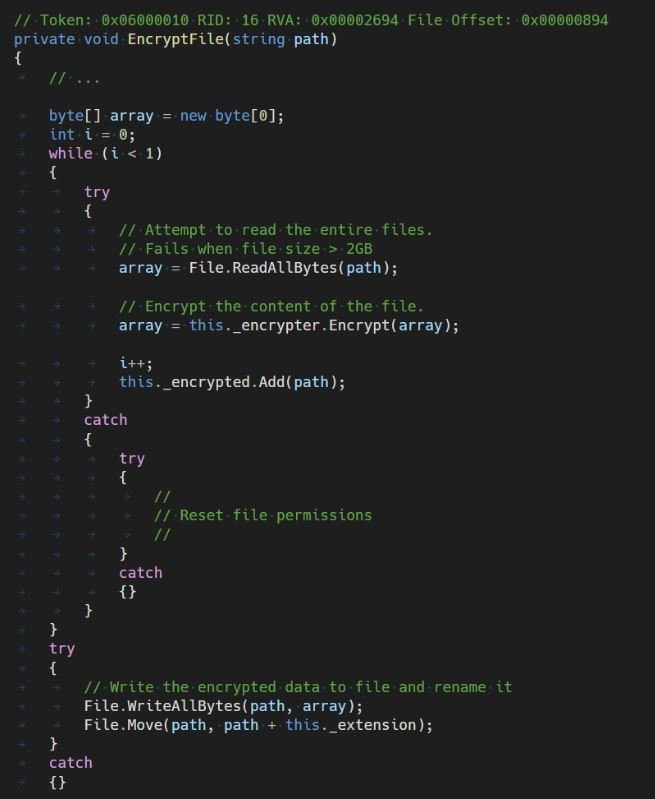
The malware sample attempts to read the entire file into memory using File.ReadAllBytes(). This feature has an internal limit that states that a maximum of 2 GB of data can be loaded; in case the file is larger, the function throws an exception, which is then handled by the try-catch block, which only handles a permission denied condition.
TaRRaK adds an ACL entry that grants full access to everyone and retrys the data read operation. In case any other error occurs, the exception is regenerated and the ransomware enters an infinite loop.
Even if the upload operation is successful and data from the file may enter memory, the Encrypt function converts the byte array to a 32-bit array of integers.
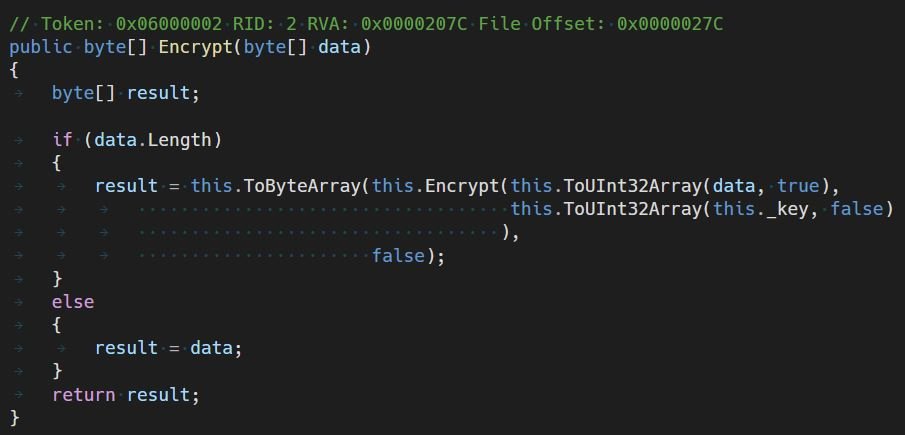
The malware allocates another block of memory with the same size as the file size and then performs an encryption operation, using a custom encryption algorithm. The encrypted Uint32 array is converted to another byte array and written to the file. Therefore, in addition to the memory allocation for the data in the original file, two additional blocks are allocated; if any of the memory allocations fail, it throws an exception and the ransomware loops again.
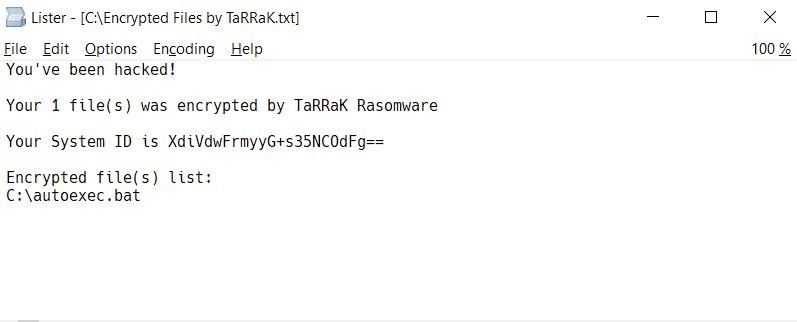
In the unusual scenarios where ransomware manages to complete the encryption process without errors, a ransom note will appear in the root folder of the compromised drives, in addition to displaying an advertisement on the user’s desktop:

Decryption tool
Avast specialists detailed the process to decrypt files infected with TaRRaK ransomware:
- Log in to the same account as the affected user
- Download the free Avast decryptor for Windows 32-bit or 64-bit
- Run the downloaded file
- On the home page, after reading the license information, click “Next”
- On the next page, select the list of locations where you want to apply decryption. By default, the tool contains a list of all local drives:
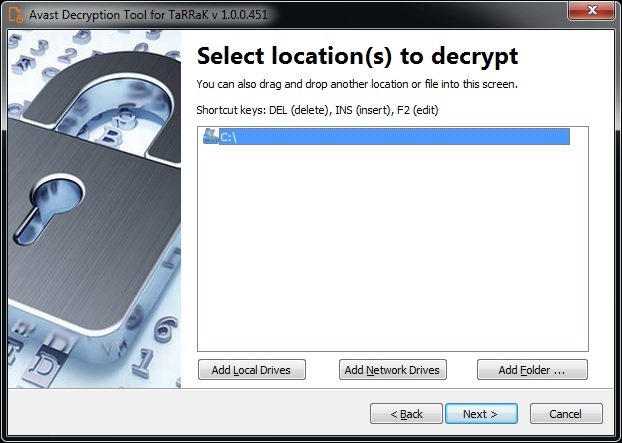
- You can choose to back up the encrypted files in case something goes wrong during the decryption process. Finally, click “Decrypt” to recover your information.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











