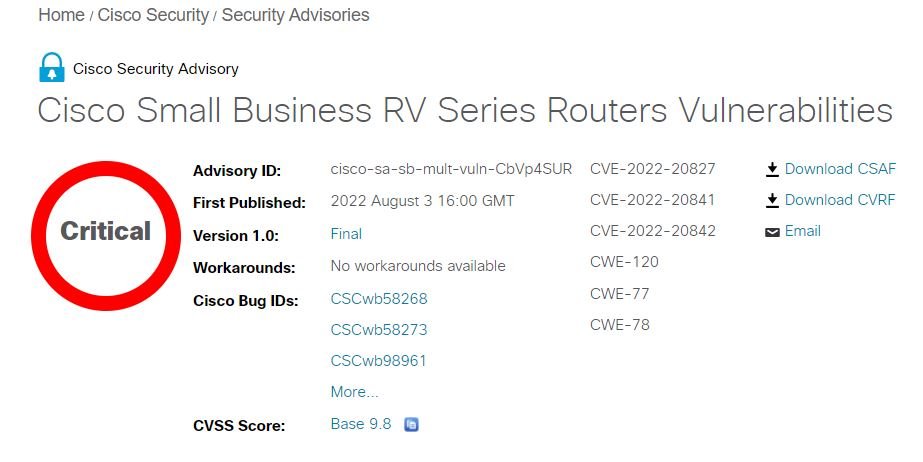
3 vulnerabilities in Cisco Small Business RV160, RV260, RV340, and RV345 Series Routers could allow an unauthenticated threat actor to remotely execute arbitrary code or cause a denial of service (DoS) condition on the router.
Affected Products
- Vulnerable Products
CVE-2022-20827 and CVE-2022-20841 affect the following Cisco products:- RV160 VPN Routers
- RV160W Wireless-AC VPN Routers
- RV260 VPN Routers
- RV260P VPN Routers with PoE
- RV260W Wireless-AC VPN Routers
- RV340 Dual WAN Gigabit VPN Routers
- RV340W Dual WAN Gigabit Wireless-AC VPN Routers
- RV345 Dual WAN Gigabit VPN Routers
- RV345P Dual WAN Gigabit POE VPN Routers
- CVE-2022-20842 affects the following Cisco products:
- RV340 Dual WAN Gigabit VPN Routers
- RV340W Dual WAN Gigabit Wireless-AC VPN Routers
- RV345 Dual WAN Gigabit VPN Routers
- RV345P Dual WAN Gigabit POE VPN Routers
Details
These vulnerabilities are interdependent on each other for exploitation. In addition, a software that is affected by one of the vulnerabilities may not be affected by the other vulnerabilities.
CVE-2022-20842
Remote Code Execution and Denial of Service Vulnerability
CVSS Base Score: 9.8
A vulnerability affects on the web-based management interface of Cisco RV340, RV340W, RV345, and RV345P Dual WAN Gigabit VPN Routers that allow an unauthenticated threat actor to remotely execute arbitrary code or cause an affected device to restart via a denial of service (DoS) attack.
This vulnerability exists due to insufficient validation of user-supplied input to the web-based management interface. A threat actor could exploit this vulnerability by sending crafted HTTP packets. A successful exploit allows a threat actor to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a DoS condition.
CVE-2022-20827:
Command Injection Vulnerability
CVSS Base Score: 9.0
A vulnerability affects the web filter database update feature of Cisco Small Business RV160, RV260, RV340, and RV345 Series Routers could allow an unauthenticated threat actor to remotely perform a command injection and execute commands on the underlying operating system with root privileges.
This vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by submitting crafted input to the web filter database update feature. A successful exploit could allow the attacker to execute commands on the underlying operating system with root privileges.
CVE-2022-20841:
Command Injection Vulnerability
CVSS Base Score: 8.3
A vulnerability affects the Open Plug and Play (PnP) module of Cisco Small Business RV160, RV260, RV340, and RV345 Series Routers. It allows an unauthenticated threat actor to remotely o inject and execute arbitrary commands on the underlying operating system.
This vulnerability is due to insufficient validation of user-supplied input. A threat actor could exploit this vulnerability by sending malicious input to an affected device. A successful exploit could allow the threat actor to execute arbitrary commands on the underlying Linux operating system. To exploit this vulnerability, an attacker must leverage a man-in-the-middle position or have an established foothold on a specific network device that is connected to the affected router.
Mitigation
There are no workarounds that address these vulnerabilities. Cisco has released software updates to patch these vulnerabilities.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











