SpaceX has opened the door for investigative hackers to hack into Starlink, its satellite internet network. The company has also added that it could pay them up to $25,000 (24,654.88 euros) for discovering some errors in the service.
The announcement comes after Lennert Wouters, a cybersecurity researcher, said last week that he was able to hack Starlink using a $25 homemade device.
The cybersecurity expert conducted the test as part of SpaceX’s bug bounty program, to which researchers submit findings about possible vulnerabilities in the Starlink network.
In a document 6-page Starlink welcomes security researchers (bring on the bugs) –Starlink welcomes security researchers (bring on the bugs), for its translation into Spanish–, SpaceX has congratulated Wouters on his discovery.
“The attack is technically impressive, and is the first of its kind that we are aware of on our system,” SpaceX said in the document.
Wouters’ hack, which involves a homemade circuit board, shouldn’t worry Starlink users and won’t directly affect satellites, according to the company itself.
The company’s own engineers always try to hack Starlink to improve the service and make it more secure.
For its part, SpaceX has opened the doors to any security researcher who wants to help make Starlink more secure, even with the possibility of joining the team or paying a certain amount of money to discover vulnerabilities.
“We allow responsible security researchers to conduct their own tests and offer monetary rewards when they find and report vulnerabilities,” SpaceX added.
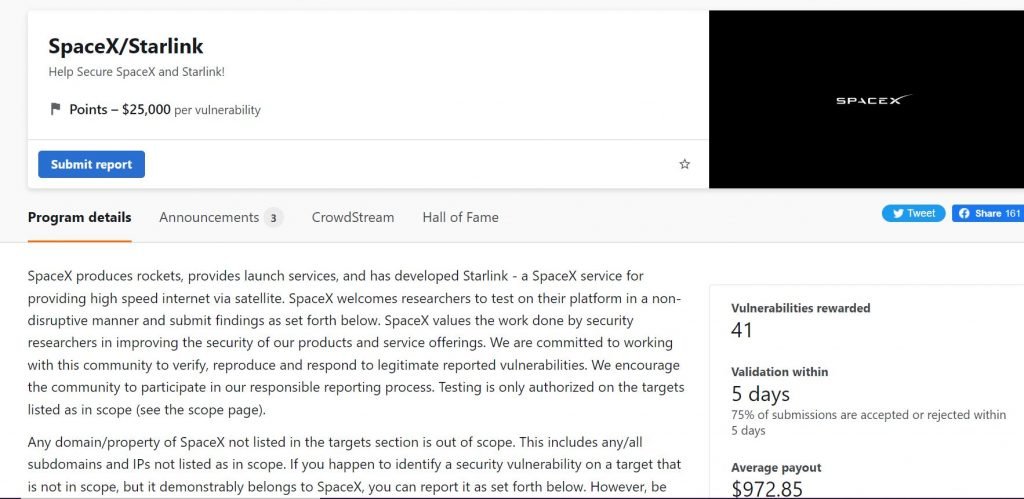
On website ‘s bug bounty SpaceX, it says that researchers who perform non-disruptive tests on Starlink, report findings, and discover in-scope vulnerabilities can receive a bounty of between $100 and $25,000. ).
The website lists 32 researchers who have already reported major security breaches at Starlink. It also highlights that the average payment in the last 3 months has been 973 dollars (959.57 euros).
Disruptive testing for users, large-scale physical attacks on infrastructure, and email spoofing are some of the findings that are out of scope in this bounty program.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











