A Turkish entity going by the name of Nitrokod has been accused of running a campaign by spoofing a desktop version of Google Translate to actively mine cryptocurrency from its more than 111,000 users across eleven countries (UK, US, Sri Lanka, Greece, etc., Israel, Germany, Turkey, Cyprus, Australia, Mongolia, and Poland) in 2019.
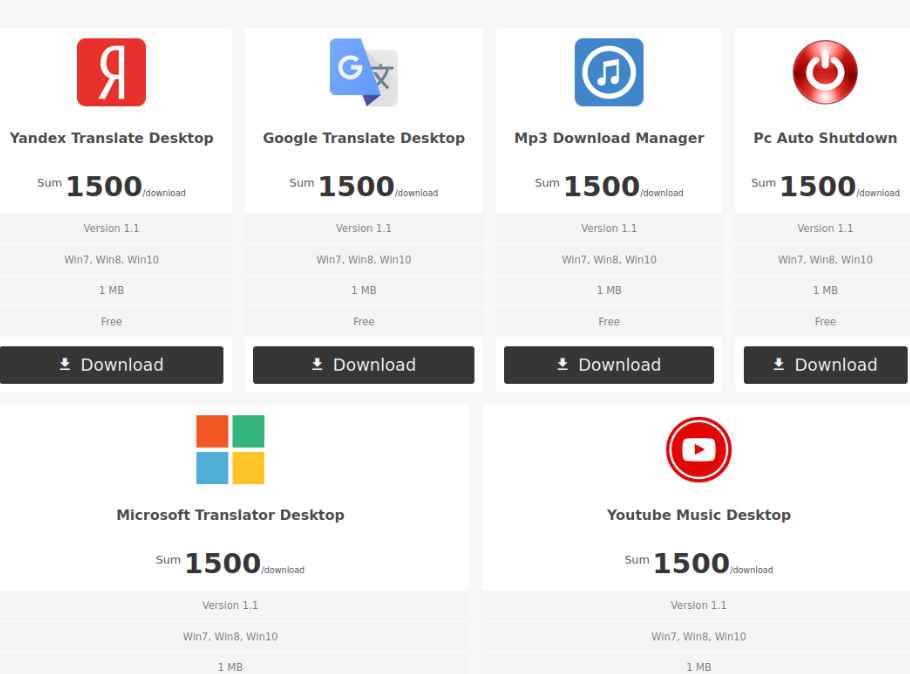
In addition to Google Translate, there are five other fake desktop applications on the Nitrokod website. Most of them impersonate programs that are not officially available as desktop applications, but as web or mobile applications, which makes the desktop version created by the attackers particularly attractive. In any case, they are popular applications that can be found on websites such as Softpedia and UpToDown.
Six fake applications available on the Nitrokod website. When installing any of these programs, the malicious effects do not manifest until after a sequence of dropper for almost a month after installation, in order to hide such effects from the antiviruses.
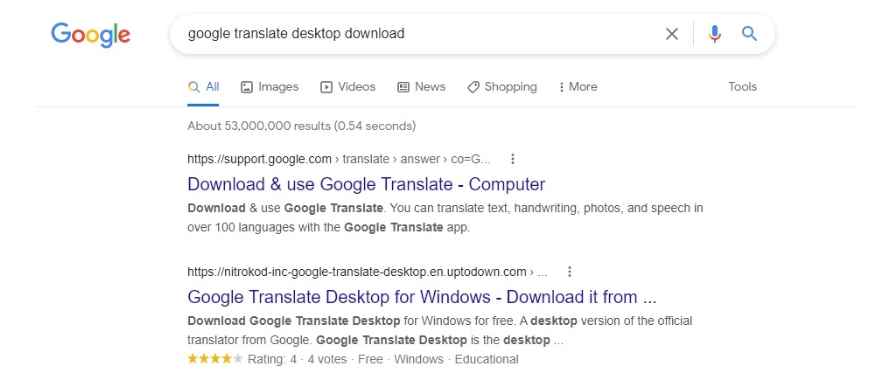
Infection process
When you download the installer of any of the applications from the Nitrokod website and run it, it will download an encrypted RAR file that is hosted on the Nitrokod domain.reveals a second installer (for example, GoogleTranslateDesktop2.50.exe) that checks the version of the installed program and downloads the first dropper (update.exe). Finally, it sends an HTTP request to the Nitrokod domain with details of the infected machine as URL parameters.
Five days after installation, update.exe on every boot of the infected system. This executable checks if the date of the last run of update.exe matches the current day, and once this has happened four times, it downloads the second dropper, chainlink1.07.exe. Therefore, the activation of the malicious behavior requires at least four reboots on different days. This strategy is a good way to evade malware using sandboxes, since sandboxes don’t run for multiple days or restart multiple times.
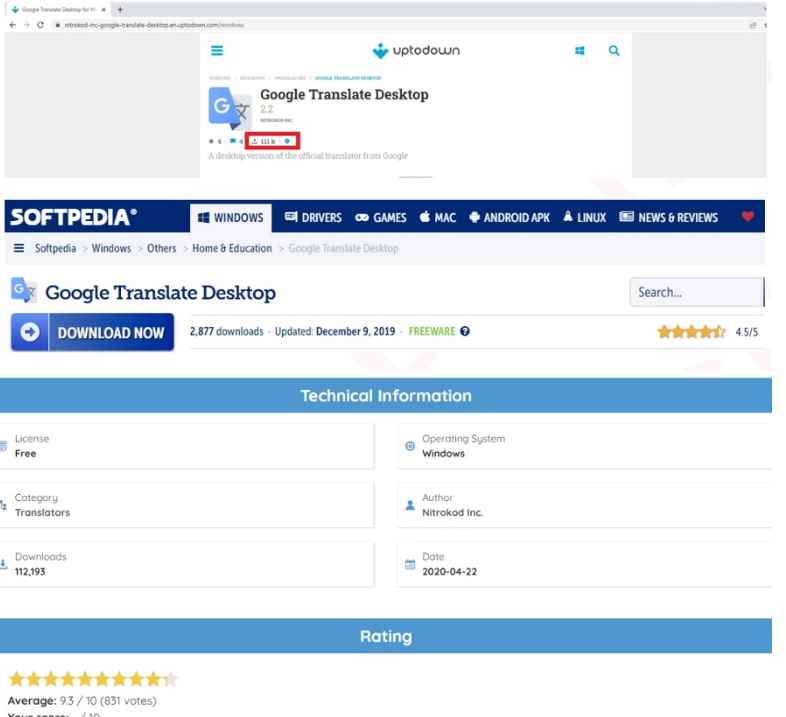
chainlink1.07.exe is responsible for creating four periodic tasks in the Task Scheduler:
| Name | Description | Frequency |
| InstallService\1 | Download an encrypted RAR file using wget | Every 15 days |
| InstallService\2 | Extract the third dropper from the RAR file | Every 2 days |
| InstallService\3 | Run the third dropper | Every day |
| InstallService\4 | Clean the logs system | Every 3 days |
Tasks that the dropper chainlink1.07.exe creates.
After creating the tasks, running chainlink1.07.exe cleans the logs and removes the chainlink1.07.exe and update.exe, as well as all related files. The next phase of the infection process would start in at least 15 days by downloading, extracting and running the third dropper. In this way, the first phases of the attack are separated from the following ones, which makes it difficult to follow the infection chain and block the initial executables.
When executing the third dropper, it checks if there are certain processes on the infected machine about virtual machines or cybersecurity products and if it finds any in its lists, it aborts its execution. Instead, if there is none, a rule is added to firewall the operating system’s dropper, called nniawsoykfo.exe and run it with Windows Defender disabled.
This fourth dropper is the one that is ultimately responsible for downloading the malware that performs cryptocurrency mining (powermanager.exe) and scheduling it to run daily. After checking the cybersecurity products installed on the machine and whether it is a laptop or desktop, powermanager.exe connects to a command and control (C&C) server nvidiacenter[.]com to receive instructions from the attacker.
Conclusions
As can be seen, the preparation of the attack consists of several phases and the mining does not start until almost a month after the installation of the program. By then the malware has already removed the evidence, making it very difficult to detect the infection and trace its actions to recognize its origin.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











