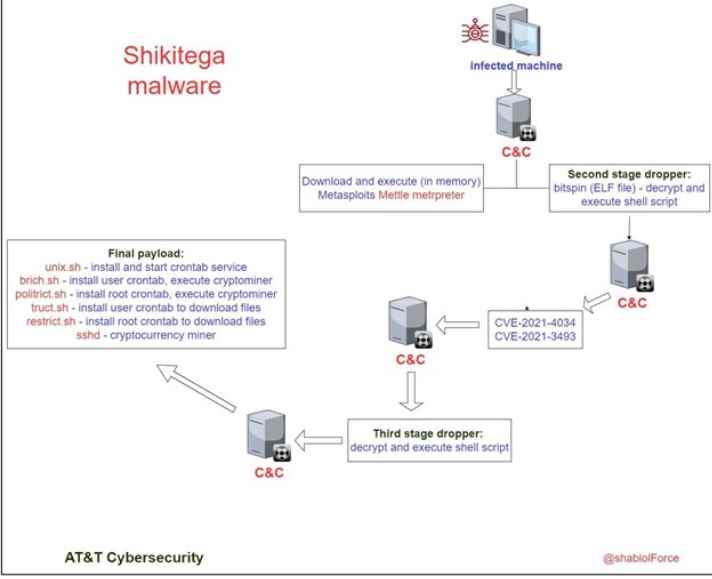
A new stealthy Linux malware known as Shikitega that infects computers and IoT devices via a series of payloads. The malware makes use of privilege elevation, adds persistence on the host via crontab, and finally launches a crypto-miner on infected devices. Shikitega is quite stealthy, managing to evade antivirus detection by using a polymorphic encoder that makes static detection based on digital signatures impossible.
Although the initial infection method is unknown at this time, the AT&T researchers who discovered Shikitega say the malware uses a multi-step infection chain in which each layer uploads just a few hundred bytes, triggering a simple module, and proceeding to Next.
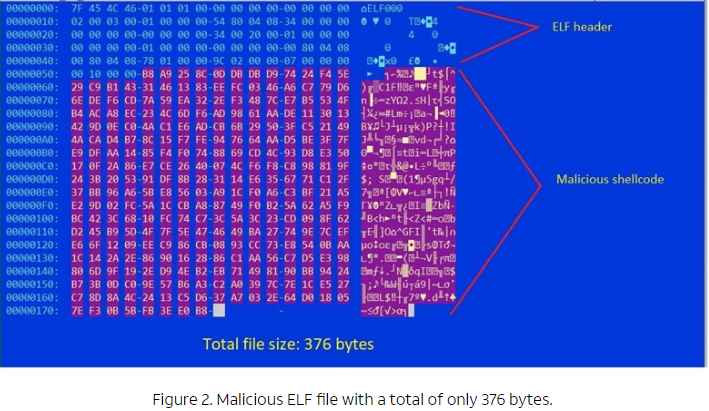
The infection starts with a 370-byte ELF file, which is the one that contains the encrypted shellcode. The encoding is done using XOR polymorphic encoder additive feedbackShikata Ga Nai’, previously analyzed by Mandiant.
“Using the encoder, the malware runs through several decryption loops, where each loop decrypts the next layer until the final shellcode payload is decrypted and executed,” the report continues.
“The encoder output is generated based on dynamic instruction substitution and dynamic block ordering. Also, records are dynamically selected.”
Once decrypted, the shellcode is executed by contacting the Command and Control (C2) from which it downloads more shellcodes that will be executed directly in memory.
One of these commands downloads and executes ‘Mettle Metasploit payload that allows remote control and command execution by the attacker.
Mettle collects an even smaller ELF file that makes use of the CVE-2021-4034 (PwnKit) and CVE-2021-3493 vulnerabilities to perform privilege and download the last stage of the payload, a crypto miner, and run it as the root user.
PwnKit exploit for privilege escalation
For Pprsistence the crypto-miner is achieved by downloading five scripts that add four cronjobs, two for the root user and two for the user from which the infection is initially performed.
Using crontab is a very efficient form of persistence, so all downloaded files are subsequently removed to avoid detection of malware.
The crypto-miner used is XMRig version 6.17.0, which focuses on mining Monero, a cryptocurrency geared towards anonymity and untraceability.
To further reduce the probability of malware being detected, the Shikitega team uses legitimate cloud servers to host their Command and Control (C2) infrastructure.
This choice incurs a higher outlay and puts operators at risk of being tracked down and identified by law enforcement but offers more discretion for compromised devices.
The AT&T team reports an increase in the amount of Linux-targeted malware this year, advising sysadmins to ensure they keep security updates up to date, use EDR on all endpoints, and perform regular backups .

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











