Researchers from Oxeye identified a critical vm2 vulnerability (CVE-2022-36067) that has the highest CVSS score of 10.0. R&D executives, Application security engineers, and security experts must make sure they rapidly repair the vm2 sandbox if they utilize it in their apps due to the new flaw known as SandBreak.
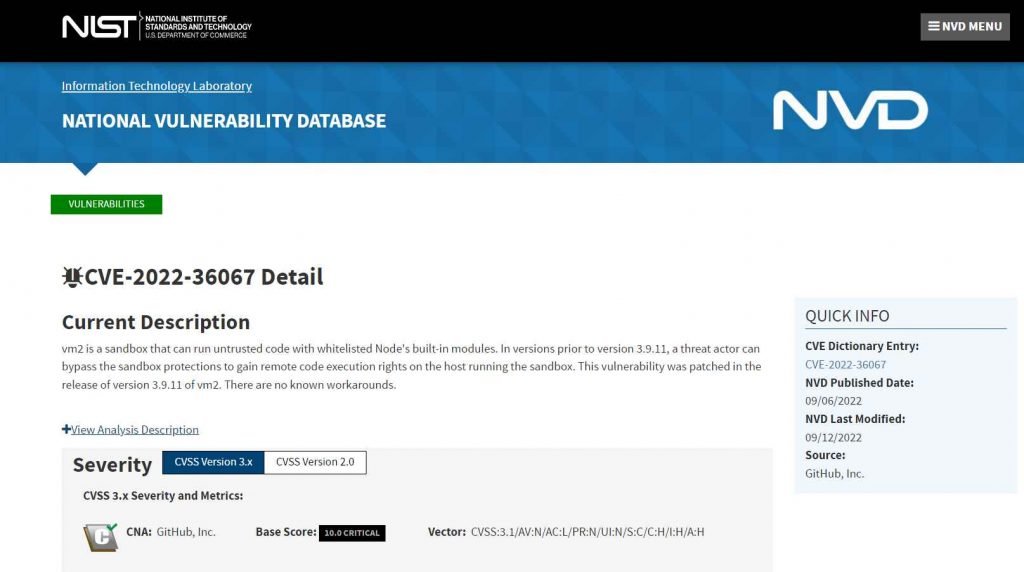
The most widely used Javascript sandbox library is vm2, which receives over 17.5 million downloads per month. It offers a widely used software testing platform that may synchronously execute untrusted code in a single process. A significant sandbox escape vulnerability that permits remote code execution was discovered in vm2 by the Oxeye research team. The project owners were informed of the vulnerability, which was quickly fixed in version 3.9.11. Users are on high alert after GitHub published warning CVE-2022-36067 for this vulnerability and assigned it a CVSS score of 10.
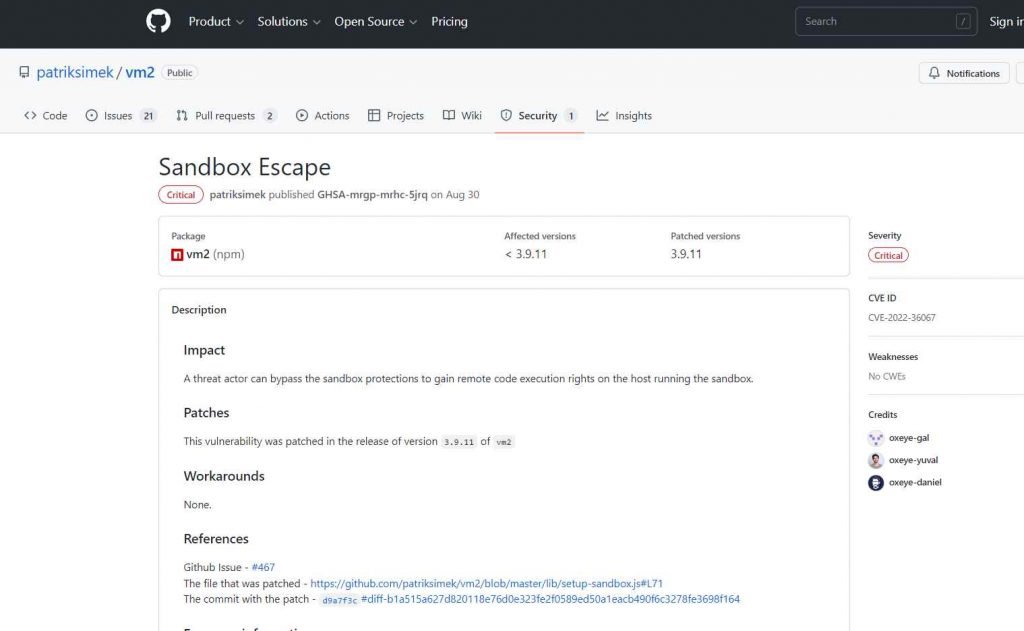
Bypassing the vm2 sandbox environment, a threat actor who takes advantage of this flaw will be able to execute shell commands on the computer hosting it. Modern applications use sandboxes for a variety of functions, including inspecting attached files in email servers, adding an extra layer of protection in web browsers, and isolating running programs in some operating systems.
It is obvious that the vm2 vulnerability might have serious repercussions for apps that utilize vm2 without a fix given the nature of the use cases for sandboxes. Given that this flaw has the highest CVSS score and is quite well-known, its potential impact is both significant and extensive.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











