Two security flaws in the Cisco AnyConnect Secure Mobility Client for Windows are being used in the wild, Cisco informed customers today. This alert supports the Cybersecurity and Infrastructure Security Agency’s (CISA) Monday statement that both security flaws have been added to its list of “Known Exploited Vulnerabilities.”
CVE-2020-3433
An authorized, local intruder could be able to launch a DLL hijacking attack thanks to a flaw in the Cisco AnyConnect Secure Mobility Client for Windows’ interprocess communication (IPC) channel. The intruder would need to obtain legitimate access credentials to the Windows computer in order to exploit this flaw.
The application’s poor run-time resource verification is what has led to the bug. By sending the AnyConnect process a specially designed IPC message, an adversary might take advantage of this weakness. With a successful exploit, the attacker could be able to run arbitrary code with SYSTEM rights on the impacted computer. The adversary would need to obtain legitimate access credentials to the Windows system in order to exploit this vulnerability.
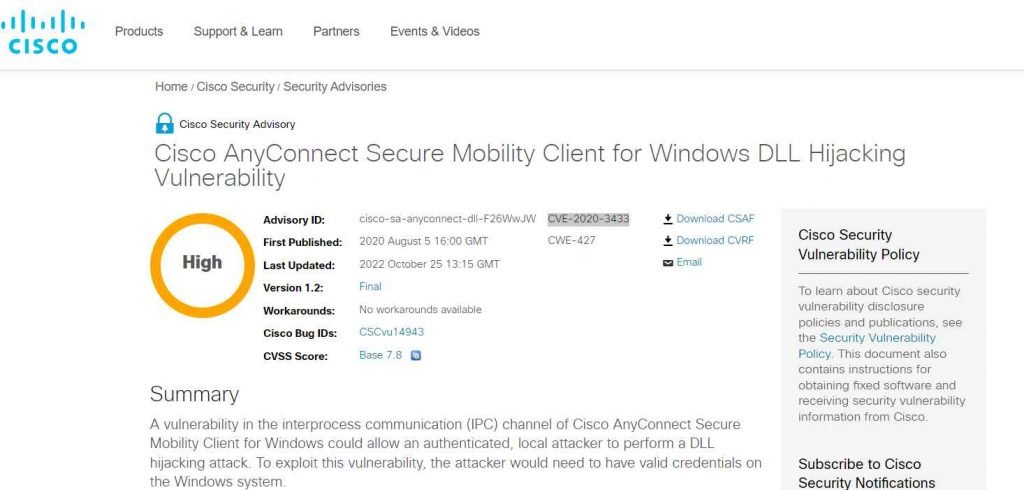
Software patches from Cisco have been made available to fix this issue. There are no alternatives.
Exploit Code
Given that a proof-of-concept attack for this CVE is currently accessible online, it could be linked to the Windows privilege escalation problem.
CVE-2020-3153
An authorized local intruder might copy user-supplied files to system level folders with system level rights if the Cisco AnyConnect Secure Mobility Client for Windows installer contains a flaw.
The improper processing of directory paths is what causes the bug. This flaw might be used by an intruder by creating a malicious payload and moving it to a system directory. An exploit might provide the adversary the ability to transfer malicious files with system-level privileges to any place. DLL pre-loading, DLL hijacking, and other similar attacks could fall under this category. The adversary need legitimate Windows system credentials in order to exploit this issue.
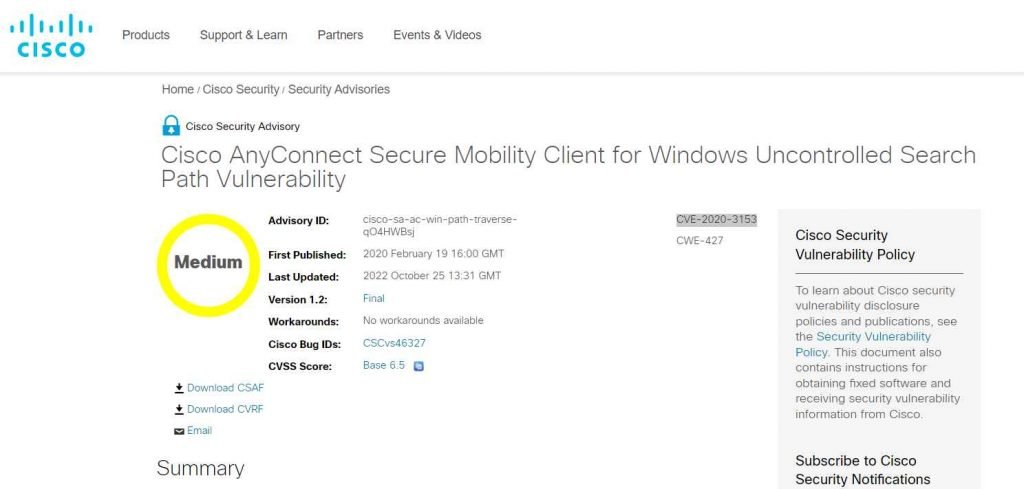
Software upgrades from Cisco have been made available that fix the flaw mentioned in this warning. There aren’t any solutions for this weakness.
Exploit Code
Given that a proof-of-concept attack for this CVE is currently accessible online, it could be linked to the Windows privilege escalation problem.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











