The research team at cyber security company has identified a flaw that makes it possible to hack video entrance systems with an NFC tag. Promon researchers found that attackers can conduct an attack on the entry system to get the admin passcode using a mobile device with NFC capabilities.

Once the passcode has been discovered, it is then possible to inject the serial number of a new NFC tag—which now contains the admin passcode—back into the database of authorized tags, giving the attacker access to both the plain-text passcode that can be entered into the keypad and an NFC tag that can be used to enter the building without having to touch any buttons.
It takes a modified app to exploit the vulnerability. a customized administrative tool app for Android that emulates the functionality of an NFC host.
A variety of video entry systems made by AIPHONE, a well-known multinational producer of intercom and security communication solutions, are vulnerable. Aiphone has been offering high-quality intercom and security communication systems for more than 50 years. The renowned Deming Prize has twice been awarded to Aiphone, the top international maker of intercom and security communication equipment.
The aforementioned devices (GT-DMB-N, GT-DMB-LVN, and GT-DB-VN) are used to safeguard commercial and residential buildings all over the world.

The Common Vulnerabilities and Exposures (CVE) ID for the vulnerability is CVE-2022-40903.
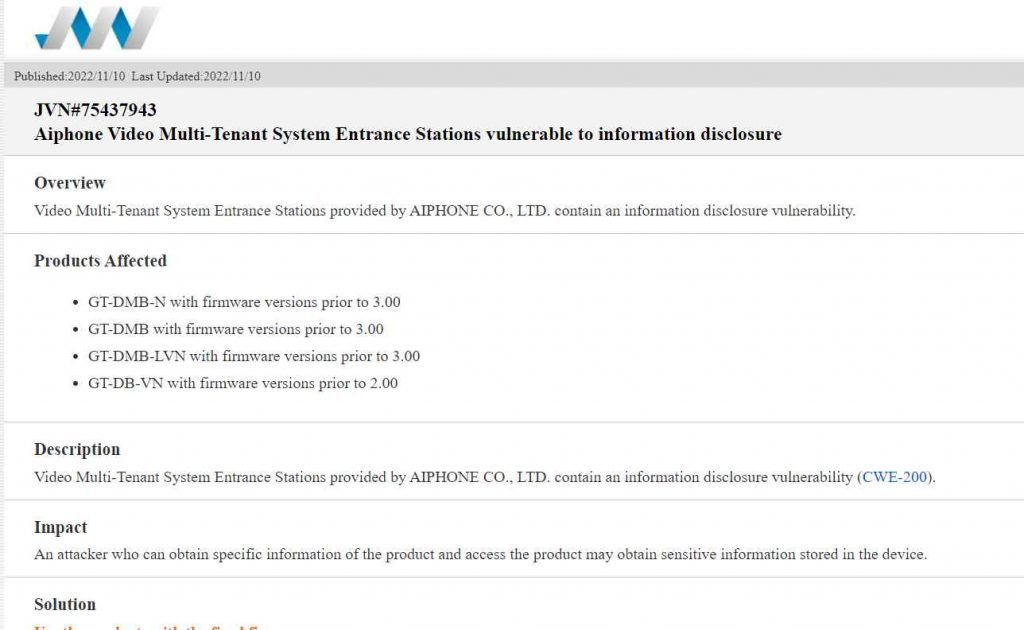
The attack is not applicable to models created after December 7, 2021. Customers with impacted systems produced before December 7, 2021, are urged to get in touch with AIPHONE for further information as no fix is available as of now. Customers have also received a warning from AIPHONE informing them of the existence of the vulnerability.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











