Nintendo has secretly released a fix for a security flaw that might have allowed hackers to access compromised Switch, 3DS, and Wii consoles.
Do you remember when Nintendo finally issued an update for Mario Kart 7 after an absence of ten years? It has come to our attention that this was done in order to patch a major vulnerability that “may let an attacker to obtain full console control.”
Despite the fact that the problem was apparently discovered for the first time in 2021, PabloMK7, Rambo6Glaz, and Fishguy6564 have been attributed with the discovery of “ENLBufferPwn.” This vulnerability is considered to be so severe that the CVSS 3.1 calculator assigned it a critical score of 9.8/10.
An online publication included a proof-of-concept (PoC) attack as well as technical details relating to a remote code execution vulnerability that affected many Nintendo titles and was fixed by Nintendo between the years 2021 and 2022.
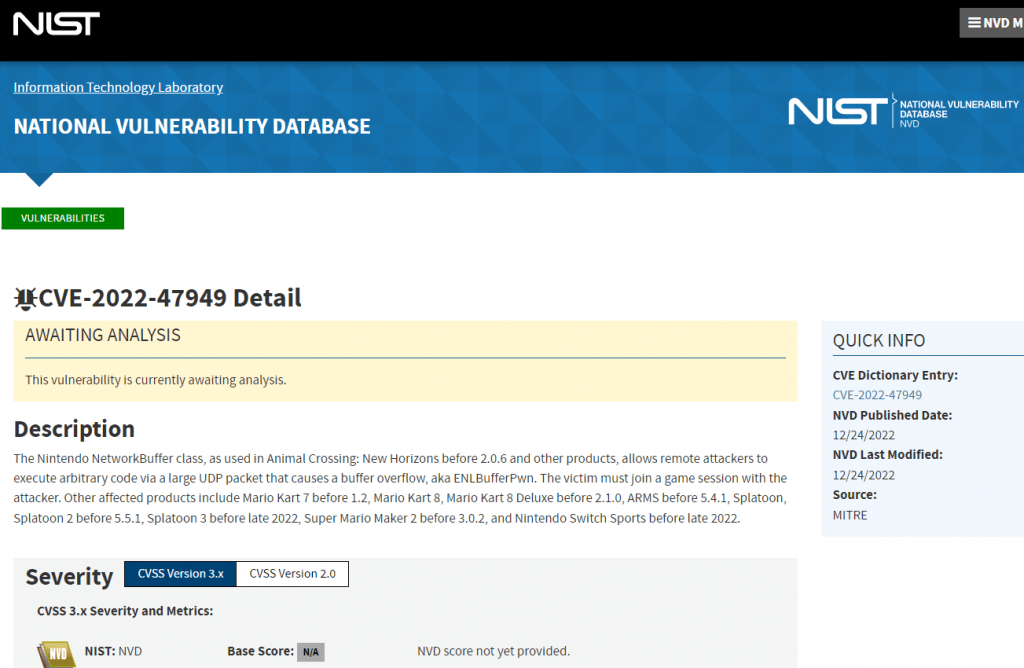
The security flaw, which has been given the identifier CVE-2022-47949, might make it possible for an attacker to remotely execute code on the victim’s console if they just played an online game with the victim. The CVSS 3.1 calculator assigned the vulnerability a score of 9.8 out of 10, which is the Critical rating.
A significant number of first-party Nintendo games make use of the network library known as enl (or Net in Mario Kart 7), which contains the C++ class NetworkBuffer. Incorrect bounds checking performed by the NetworkBuffer class is the root cause of the vulnerability. A remote attacker may overrun a buffer and execute arbitrary code on the system if they sent a UDP packet that they had specifically prepared for that purpose. The researchers referred to the flaw as “ENLBufferPwn” in their research.
The CVE-2022-47949 flaw has been validated and shown to function properly in the following games, according to testing and confirmation.
- Mario Kart 7 (fixed in v1.2)
- Mario Kart 8
- Mario Kart 8 Deluxe (fixed in v2.1.0)
- Animal Crossing: New Horizons (fixed in v2.0.6)
- ARMS (fixed in v5.4.1)
- Splatoon
- Splatoon 2 (fixed in v5.5.1)
- Splatoon 3 (fixed in late 2022, exact version unknown)
- Super Mario Maker 2 (fixed in v3.0.2)
- Nintendo Switch Sports (fixed in late 2022, exact version unknown)
The ENLBufferPwn vulnerability allows an attacker to take advantage of a buffer overflow in the C++ class NetworkBuffer that is included in the enl (Net in Mario Kart 7) network library. This library is utilized by a large number of first-party Nintendo titles. These two methods, Add and Set, are included in this class, and they are responsible for populating a network buffer with data arriving from other players. None of these approaches, however, verify that the data being entered can really be accommodated inside the network buffer. Because the data that is entered may be controlled by the attacker, it is possible for them to cause a buffer overflow on a remote console by simply engaging in an online gaming session with the victim. If everything is done correctly, the person who was exploited could not even realize that a vulnerability was exploited in their console. The results of this buffer overflow are unique to each game, ranging from relatively harmless modifications to the game’s memory (such as repeatedly opening and closing the home menu on the 3DS) to more severe actions, such as taking full control of the console, as will be demonstrated in the following paragraphs.
The vulnerability was been addressed in Splatoon 3, Mario Kart 8, Mario Kart 8 Deluxe, Animal Crossing: New Horizons, ARMS, Splatoon 2, and Super Mario Maker 2, in addition to Mario Kart 8 and Mario Kart 8. One of the persons who found the vulnerability said that “coupled with other OS vulnerabilities, the vulnerability might enable an attacker to accomplish complete console control.”

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











