VRealize Log Insight is a log collecting and analytics virtual appliance that gives administrators the ability to collect, display, manage, and analyze syslog data. Log Insight was developed by Logrotate. Application logs, network traces, configuration files, messages, and performance statistics can all be monitored in real time using Log Insight. It has been purpose-built for use in a heterogeneous data center and a hybrid cloud environment. It provides and maintains the infrastructure and applications in order to boost the business’s agility while while keeping IT in control.
VMware has published a security bulletin that contains information about 4 vulnerabilities.
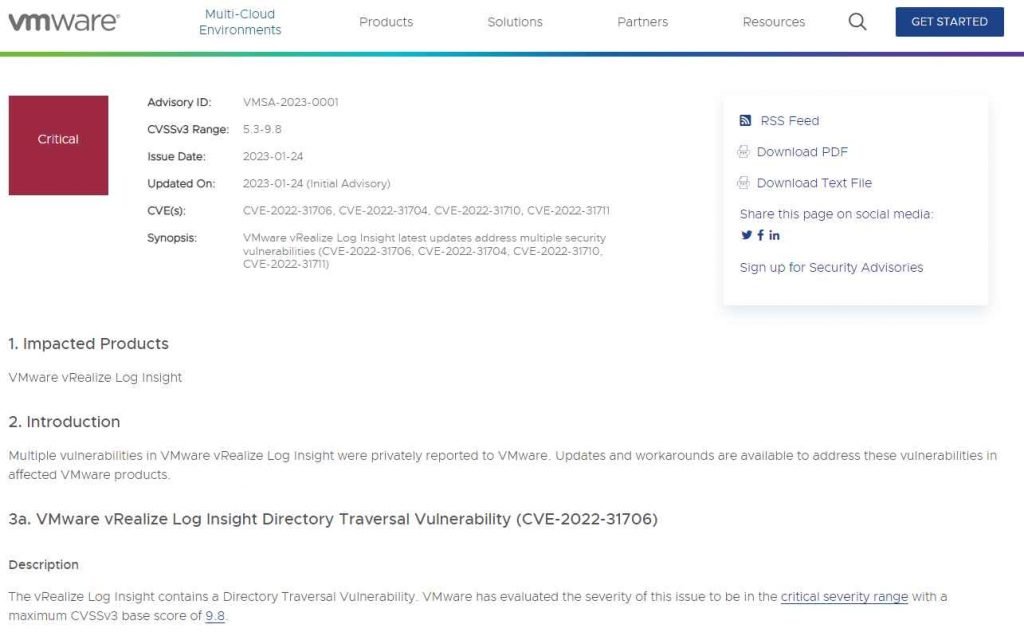
1) Path traversal
Risk: High
CVE-ID: CVE-2022-31703
There is a flaw in the input validation that causes the vulnerability, and it manifests itself during the execution of directory traversal sequences inside the vRNI REST API. An attacker from a remote location is able to access arbitrary files on the system by sending a carefully crafted HTTP request. Because to this vulnerability, an outside attacker might potentially carry out directory traversal attacks.
2) Improper access control
Risk: Critical
CVE-ID: CVE-2022-31704
Because of the vulnerability, an off-site attacker is able to get access to the compromised system. Because inappropriate access limits were implemented, the vulnerability still persists. An external attacker is able to circumvent the security constraints that have been established and run arbitrary code on the system.
3) Deserialization of Untrusted Data
Risk: Medium
CVE-ID: CVE-2022-31710
A denial of service (DoS) attack may be carried out by an unauthorized remote user because of the vulnerability. When processing serialized data, the input validation was not sufficiently secure, which led to the vulnerability. A denial of service (DoS) attack may be carried out against an application by sending specially prepared data to it while the attacker is located remotely and not authorized.
4) Information disclosure
Risk: Medium
CVE-ID: CVE-2022-31711
Because of the vulnerability, an off-site attacker might obtain access to information that could be considered sensitive. The program generates an enormous amount of data, which is the root cause of the vulnerability. An attacker operating from a distant location has the ability to get unauthorized access to sensitive session and application data.
vRealize Log Insight: Versions 8.0.0 through 8.10 are the ones that are vulnerable to attack. Download and install the update from the company’s website.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











