Argo CD is a Kubernetes-based declarative GitOps continuous delivery platform. It is built as a Kubernetes controller that constantly monitors running apps and compares their current, live state to the intended goal state (as specified in the Git repo). 257 enterprises, including Alibaba Group, BMW Group, Deloitte, Gojek, IBM, Intuit, LexisNexis, Red Hat, Skyscanner, Swisscom, Tesla, and Ticketmaster, utilize Argo CD.
CVE-2023-22482 (CVSS score of 9.0) affects versions 1.8.2 through 2.6.0-rc4, v2.5.7, v2.4.18, and v2.3.13, and has been fixed in versions 2.6.0-rc5, v2.5.8, v2.4.20, and v2.3.14.
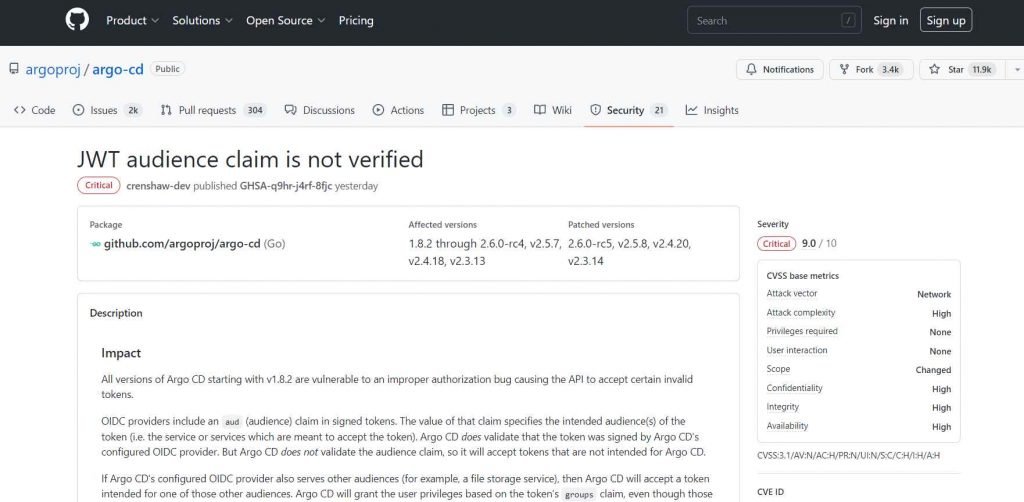
Beginning with v1.8.2, all versions of Argo CD are subject to an inappropriate authorisation problem that causes the API to accept certain erroneous tokens.
In signed tokens, OIDC providers add an aud (audience) claim. The value of that claim identifies the token’s intended audience(s) (i.e. the service or services which are meant to accept the token). Argo CD verifies that the token was signed by the selected OIDC provider. However, since Argo CD does not confirm the audience claim, it will accept tokens that are not meant for Argo CD.”
Users of Argo CD are urged to upgrade to a patched version of the platform as soon as possible since there are no workarounds for CVE-2023-22482.
The vulnerability, identified as CVE-2023-22736 (CVSS score of 8.5), is an authorisation bypass that enables an attacker to deploy Applications outside of the set authorized namespaces. This vulnerability was addressed in Argo CD versions 2.5.8 and 2.6.0-rc5.
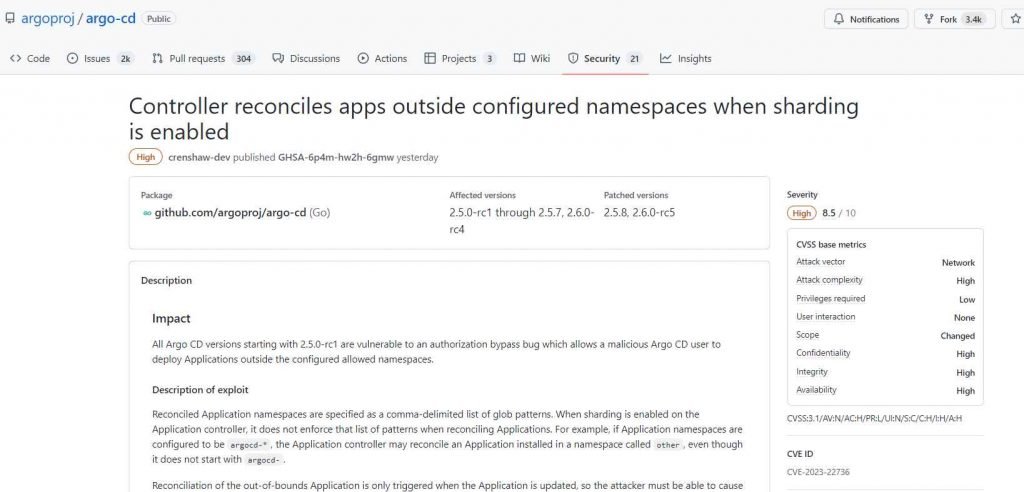
There is a fix for this issue that does not need updating
“Running just one replica of the Application controller will prevent this flaw from being exploited. Making ensuring that all AppProjects’ sourceNamespaces are confined inside the limits of the set Application namespaces will also prevent this flaw from being exploited.
After two vulnerabilities were discovered that might enable an attacker to access Argo CD and deploy Applications beyond the defined authorized namespaces, users of the Argo continuous deployment (CD) tool for Kubernetes are being asked to roll through fixes.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











