BIG-IP has a high-severity format string vulnerability, according to F5, which might enable an authorized attacker to create a denial-of-service (DoS) scenario and perhaps execute arbitrary code. F5 has issued a warning about this vulnerability.
Because to this vulnerability, an authorized attacker who has network access to iControl SOAP via the BIG-IP management port and/or self IP addresses may be able to execute arbitrary system instructions or cause a denial of service (DoS) on the iControl SOAP CGI process. In order for an attacker to properly exploit the command execution attack vector, they need to obtain information about the environment in which the component that is susceptible resides. This problem is exclusively related to the control plane; there is no risk to the data plane. Appliance mode is either mandated by a particular license or offered as an option for individual Virtual Clustered Multiprocessing (vCMP) guest instances, where it may be activated or disabled as desired.
The company said that in order to take advantage of the command execution attack vector, the attacker has to obtain information about the target environment that is housing the vulnerable component. The manufacturer also said that this vulnerability solely affects the control plane, and that the data plane is not affected in any way.
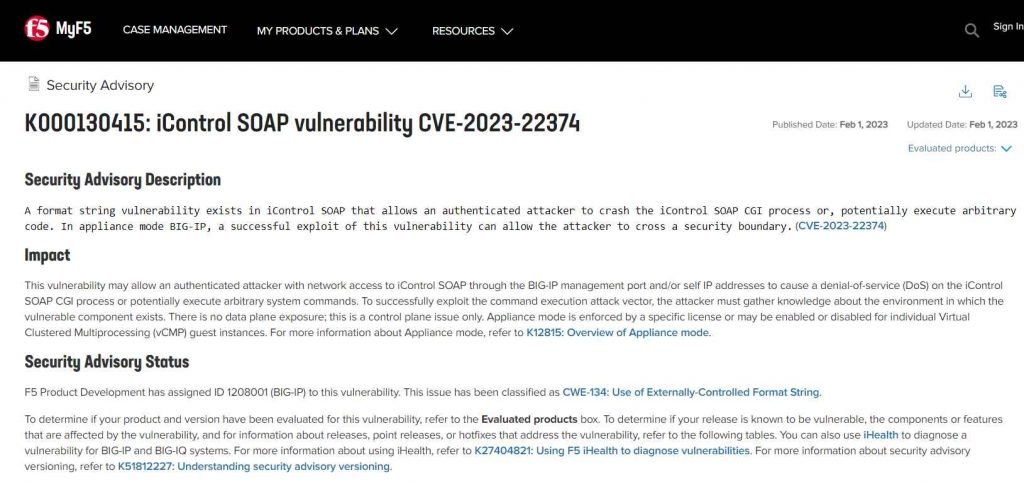
The problem is a format string vulnerability that exists in the iControl SOAP application, which operates with the root user and needs a login to access it administratively. The vulnerability may be exploited by an authorized attacker to either cause the iControl SOAP CGI process to crash or, theoretically, to execute arbitrary code.
An adversary on the network may get access to the SOAP interface by using either the BIG-IP administration port or their own self-assigned IP addresses.
By exploiting this vulnerability in appliance mode BIG-IP, threat actors may be able to circumvent a security barrier.
A CVSS score of 7.5 has been assigned to the vulnerability for deployments in standard mode, while a value of 8.5 has been assigned for installations in appliance mode.
The service may read and write memory locations referred to from the stack by introducing format string specifiers into certain arguments that are provided to the syslog function, according to Rapid7, which discovered the flaw.
However, according to the explanation provided by the cybersecurity company, the attacker is unable to read the memory unless they also have access to the syslog.
According to Rapid7, “It is impossible to affect the precise addresses read and written, which makes it exceedingly difficult to attack (other than crashing the service) in reality.” This is one of the reasons why this vulnerability is so difficult to exploit.
According to the cybersecurity company, an adversary could cause the service to crash by using the ‘%s’ specifier, and they could use the ‘%n’ specifier to write arbitrary data to any pointer on the stack, which could potentially lead to remote code execution. Both of these exploits could be carried out by using the same specifier.
The following versions of BIG-IP are vulnerable due to the flaw:
- F5 BIG-IP 17.0.0
- F5 BIG-IP 16.1.2.2 – 16.1.3
- F5 BIG-IP 15.1.5.1 – 15.1.8
- F5 BIG-IP 14.1.4.6 – 14.1.5
- F5 BIG-IP 13.1.5
This vulnerability has been given the identification number 1208001 (BIG-IP) by F5 Product Development. This problem has been given the identification number CWE-134 and is known as the Use of Externally-Controlled Format String. Refer to the box labeled “Evaluated products” to see whether or not your product and its version have been tested for this vulnerability. If your release is known to be vulnerable, you can also determine which components or features are affected by the vulnerability. You may also detect a vulnerability for BIG-IP and BIG-IQ systems by using iHealth.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











