An official notification from the FBI was published on the website of the prominent cybercrime forum on Tuesday. The notice said that the forum had been seized because it was suspected of enabling large-scale identity theft. Genesis Market has been operational since 2018, and their catchphrase has been “Our store offers bots with logs, cookies, and their actual fingerprints” for quite some time. Clients had a number of different choices at their disposal for searching for infected systems. They included searching for infected systems by IP address or by particular domain names connected with stolen credentials.

When a consumer makes a purchase through Genesis, they are really acquiring the opportunity to have all of the victim’s authentication cookies loaded into their browser. This enables the buyer to access online accounts belonging to the victim without the need for a password, and in certain circumstances without the necessity for multi-factor authentication. The price of Genesis bots varied quite a little, but in general, bots that had access to particular financial services like as PayPal and Coinbase, or ones that had a big quantity of passwords and authentication cookies, tended to fetch much higher rates.
During the course of its history, Genesis Market is responsible for a lot of developments that are used by cybercriminals. Genesis Security is probably the greatest example of this because it is a special Web browser plugin that can load a Genesis bot profile. This allows the browser to imitate practically every key characteristic of the victim’s device, from screen size and refresh rate all the way to the one-of-a-kind user agent string that is attached to the victim’s online browser. Genesis Security is probably the best example because it is probably the finest example. According to experts, the administrators of Genesis Market assert that they are a group of experts with “deep expertise in the area of systems metrics.” They claim that they were able to construct the Genesis Security program by doing research on the 47 most popular browser fingerprinting and tracking systems, in addition to the systems used by different banking and payment companies.
According to specialists in cybersecurity, Genesis and a few other bot marketplaces are popular among cybercriminals who strive to locate and acquire bots within corporate networks. These cybercriminals then offer access to these networks to ransomware gangs. One of the aspects of Genesis that sets it apart from other bot shops is the ability for customers to keep access to infected systems in real-time. This means that if the legitimate owner of an infected system establishes a new account online, those new credentials will be stolen and presented in the web-based panel of the Genesis client who bought that bot. This is one of the aspects of Genesis that sets it apart from other bot shops.
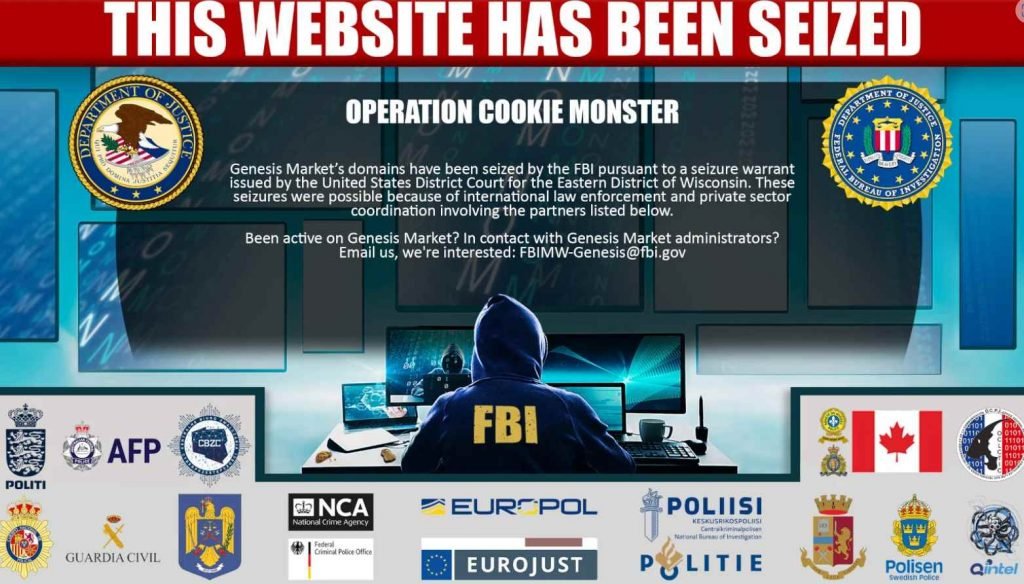
But, at an earlier time today, the homepages of various domains affiliated with Genesis were replaced with a seizure notice from the FBI. The notification said that the domains were taken in accordance with a warrant issued by the United States District Court for the Eastern District of Wisconsin. The law enforcement agencies in the United States, Canada, and throughout Europe are currently serving arrest warrants on dozens of individuals who are believed to support Genesis in one of two ways: either by maintaining the website or by selling the service bot logs from infected systems. The information was provided by the sources. The notice of seizure has the official seals of numerous different law enforcement agencies from across the world, including those from Australia, Canada, Denmark, Germany, the Netherlands, Spain, and Sweden, as well as the United Kingdom.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











