The exploit code for a serious flaw in printer software was made accessible to the general public on Monday, as part of a release that has the potential to heighten the danger posed by malware attacks, which have already been going on for the last week.
The print management software known as PaperCut, which, according to the website of the firm, has more than 100 million users from 70,000 companies, has a flaw that allows for unauthorized access. At the time that this article was made public, the Shodan search engine revealed that there were around 1,700 instances of the malware that were accessible through the internet. The two security issues, which are listed as CVE-2023-27350 and CVE-2023-27351, make it possible for remote attackers to bypass authentication and execute arbitrary code on compromised PaperCut servers with SYSTEM rights. These types of attacks are low-complexity and do not involve user interaction. Two days after PaperCut disclosed the attacks, a security company called Huntress said that it saw threat actors leveraging CVE-2023-27350 to install two pieces of remote management software on unpatched systems. These pieces of software are known as Atera and Syncro, respectively. After that, evidence proved that the threat actor had installed the malware known as Truebot via the remote management software that was employed. There is a connection between Truebot and a threat organization called Silence, which in turn has connections to a ransomware gang called Clop. Previously, Clop made use of Truebot in attacks that took place in the wild and took use of a serious flaw in a piece of software known as GoAnywhere.
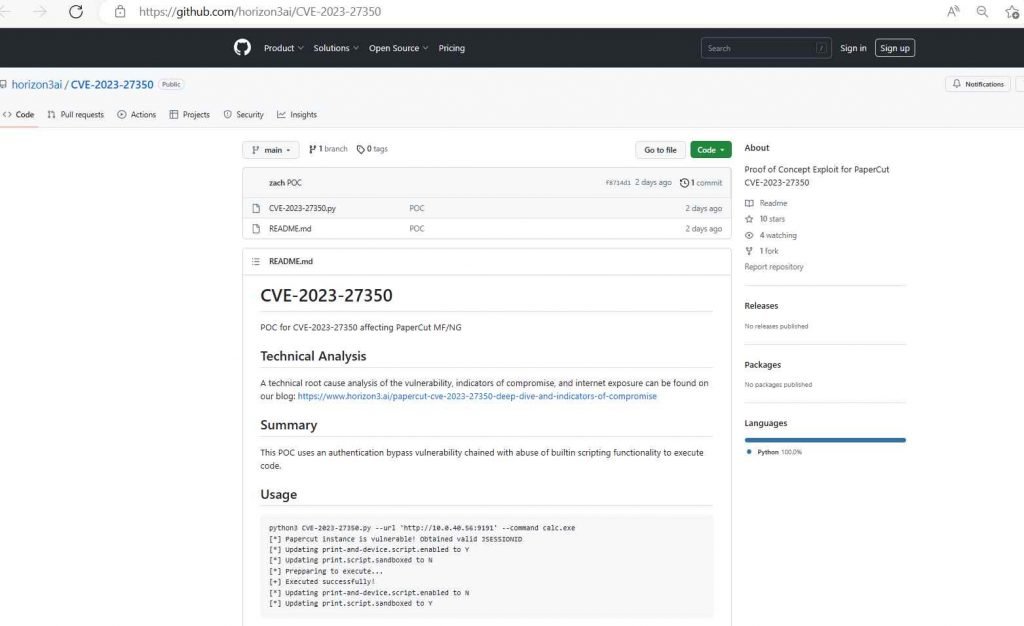
Researchers from the security company Horizon3 released their study of the vulnerabilities on Monday, along with proof-of-concept attack code for the most serious one of the flaws. This attack, which is very similar to the proof-of-concept exploit disclosed by Huntress, takes use of a weakness in the authentication bypass mechanism in order to manipulate the built-in scripting feature and execute code.
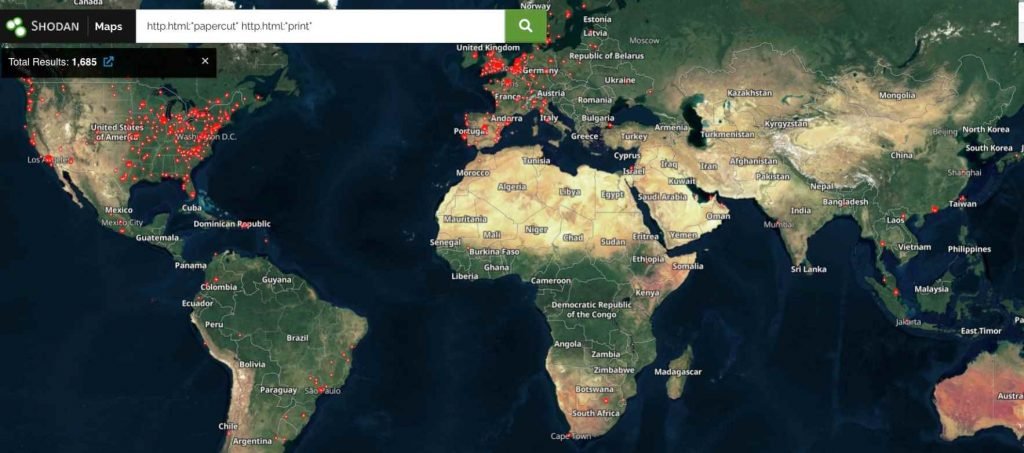
Huntress revealed on Friday that there are around 1,000 Windows computers with the PaperCut application installed in the client settings that it safeguards. Out of them, there were around 900 that lacked a patch. Only one of the three macOS Macs that it monitored had the patch applied to it. Assuming that the statistics are indicative of PaperCut’s wider install base, the data from Huntress shows that thousands of servers are still at risk of being attacked. As was said before, it is possible to locate close to 1,700 servers that are openly accessible over the internet. Investigations of a deeper nature can turn up even more information.
On Friday, CISA added the CVE-2023-27350 vulnerability to its list of actively exploited vulnerabilities. The agency then issued an order to federal agencies instructing them to safeguard their systems against continuing exploitation within three weeks and no later than May 12, 2023.
Administrators that are unable to rapidly fix their PaperCut servers are advised by Huntress to take precautions to avoid remote exploitation.
This involves blocking all traffic to the web management port (default port 9191) from external IP addresses on an edge device. Additionally, this includes blocking all traffic to the same port on the server’s firewall in order to confine administration access entirely to the server and to avoid any network breaches.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











