The Federal Bureau of Investigation (FBI) made the announcement on Tuesday that it had successfully disabled a network of compromised computers that Russian agents had been using for years to steal sensitive information from at least 50 nations, including the governments of NATO members. The move seems to be a severe blow to Russia’s internal intelligence arm, the FSB, which is said to have used the sophisticated hacking tool to penetrate US and Western diplomatic and military institutions for over two decades. The action was taken by the US Department of Homeland Security. It is the most recent effort by the Justice Department to crack down on foreign eavesdropping and criminal organizations using FBI technologies that have been specifically designed for that purpose.
According to authorities in the United States, the Federal Bureau of Investigation (FBI) utilized a court order on Monday to prevent the Russian government from accessing the network of computers in the United States that the hackers were using to transport the stolen material across the globe and back to Russia. A senior FBI official said in a teleconference with reporters on Tuesday that it would be “difficult or and untenable” for the FSB to successfully utilize the hacking tool again due to the FBI operation and public cautions issued by the United States about the hacking tool.
For instance, agents from the FSB used the hacking tool to “access and exfiltrate sensitive international relations documents, as well as other diplomatic communications” from a NATO member that was not mentioned in the advice released on Tuesday by the United States and its “Five Eyes” partners.
Experts are almost unanimous in their belief that the Russian hacking organization known as Turla, which the FBI targeted, is one of the most elite cyber-espionage teams in the Russian intelligence services. Both a major security breach that occurred in US military networks in the middle to late 1990s and a hack that occurred at US Central Command in 2008 have been linked to tools developed by Turla.
Snake was dubbed “the FSB’s most sophisticated long-term cyberespionage malware implant,” allowing its users to remotely install malware on compromised devices, steal private documents and information (such as authentication credentials), keep persistence, and conceal their malicious activities when utilizing this “covert peer-to-peer network.”
A unified alert including information that might assist defenders in locating and removing the Snake malware that is present on their networks has been released by the cybersecurity and intelligence agencies of the Five Eyes nations.
According to the evidence shown in court papers, the Federal Bureau of Investigation (FBI) acquired the capacity to decrypt and decode Snake communications by conducting a study of the Snake malware as well as the Snake network. The Federal Bureau of Investigation (FBI) developed a tool known as PERSEUS using the knowledge it obtained from monitoring the Snake network and analyzing the Snake malware. This tool “establishes communication sessions with the Snake malware implant on a particular computer and issues commands that causes the Snake implant to disable itself without affecting the host computer or legitimate applications on the computer.”
When decrypting network traffic between United States and NATO devices infiltrated by Snake malware, the FBI discovered that Turla operators exploited the implant in efforts to acquire what appeared to be classified United Nations and NATO papers. The search warrant that the FBI was able to get enabled the agency to access the infected devices, replace the malicious software without impacting authorized programs and data, and shut down the malicious software that was operating on the hacked systems.
The Federal Bureau of Investigation (FBI) is now telling all owners or operators of computers that have been remotely accessed to delete the Snake malware and advising them that they may need to remove additional dangerous tools or software planted by the attackers, such as keyloggers that Turla often also installs on affected systems. This notification is being sent to all owners or operators of computers that have been remotely accessed.
HOW TO DETECT SNAKE MALWARE IN YOUR NETWORK
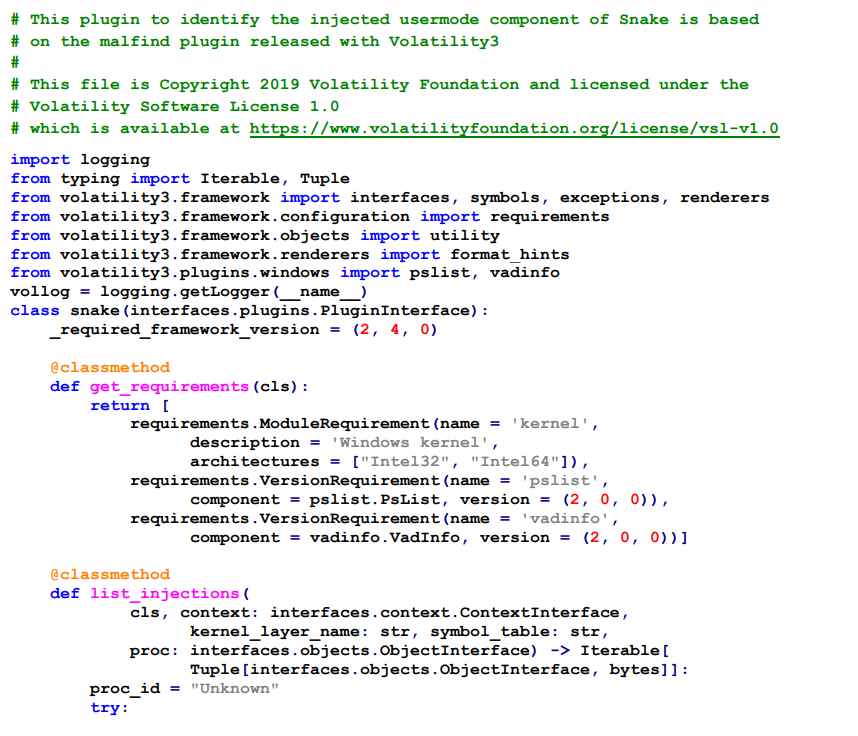
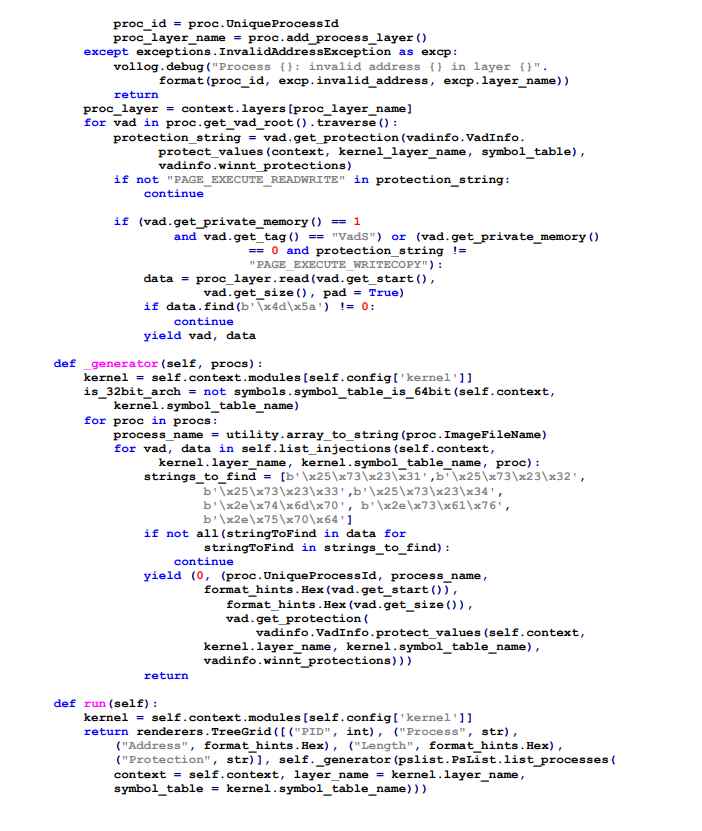
The following plugin for the Volatility memory analysis framework will search through every process on the machine in search of the Snake user mode component that has been injected into a process. If it is discovered, the plugin will show both the injected process and the virtual memory location at which the Snake user mode component is loaded. If it is not found, the plugin will do nothing.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











