The significance of keeping one’s data safe has never been more pressing than it is in today’s increasingly linked society. Zero-day vulnerabilities are known to often hide in the shadows of our digital landscapes, where they patiently wait to be exploited. Today, we are going to shed light on one of these recently discovered vulnerabilities known as CVE-2023-34362, which is a SQL injection vulnerability that was found to be present in the MOVEit Transfer online application. The well-known application MOVEit Transfer, which is used for controlled file transfers, has been the target of an attack. SQL injection vulnerabilities were present in versions prior to 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1). Unauthenticated attackers have been taking advantage of these vulnerabilities. Because to this vulnerability, they have the opportunity to access the database of MOVEit Transfer, which contains a great treasury of sensitive information.These cyber bandits may be able to acquire insights into the structure of the database as well as the contents of the database depending on the database engine that is being used (MySQL, Microsoft SQL Server, or Azure SQL). They also have the ability to execute SQL commands, which allows them to edit, change, or even destroy important database components. Unpatched systems are very vulnerable to the risk of being exploited using either HTTP or HTTPS.
According to Rapid7, as of the 31st of May in 2023, an alarming 2,500 instances of MOVEit Transfer were available to the general public over the internet. The United States was discovered to be the location of the bulk of these exposed cases, which raises substantial issues about cybersecurity.
As soon as this information became public, the United States Cybersecurity and Infrastructure Security Agency (CISA) issued a warning about the potential threat. It recommended any and all users and organizations who utilize MOVEit Transfer to take certain preventative measures in order to protect themselves from the possibility of criminal activities.
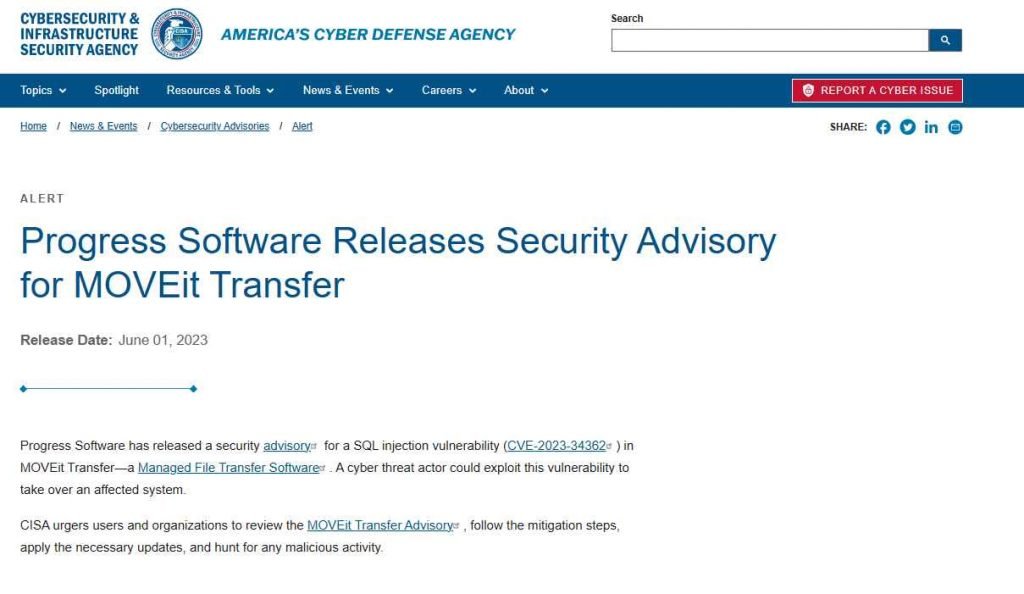
Isolating servers is one of the recommended stages, and it is of the highest significance. It is possible to drastically reduce the scope of potential attacks by blocking traffic in both directions (inbound and outbound). It is also vital to conduct exhaustive inspections of settings in search of potential indicators of compromise (IoCs). Before making the required adjustments, it is strongly suggested to get rid of any IoCs that have been found.
The finding of CVE-2023-34362 serves as a further reminder of the persistent dangers that constantly lurk in our digital environment. This SQL injection vulnerability in the MOVEit Transfer online application is a striking reminder of the constant cybersecurity threats we face. It was discovered in the wild in May and June 2023.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











