Mockingjay is the name of an innovative process injection approach that has the potential to enable threat actors to avoid being detected by EDR (Endpoint Detection and Response). Process injection is a well-known method that malicious software and attackers use to introduce and execute code into the memory area of a process. This may be accomplished by inserting the code directly into the process itself. Either the process that is carrying out the operation itself (known as self-injection) or another process entirely might be the source of this injection. To gain illegal access, control the behavior of the process, or mask the injected code from security tools and defenders, attackers will often target legitimate processes when injecting code into an external one, such as running apps or system processes.
An attacker will use a collection of Windows APIs, each of which is designed to perform a specific function inside the injection logic, in order to inject and execute code in memory. This may be done either within the same process or within a remote process. Depending on the technological basis of the code injection approach that is used, there may be a difference in the amount of function calls that are made as well as the exact Windows APIs that are used.
Typical methods for process injection include dynamic link library (DLL) injection, portable executable injection, thread execution hijacking, process hollowing, and process doppelganging, amongst others. Some of these methods are more well-known than others.
It is important to note that each of these techniques needs a mix of particular system calls and Windows APIs in order to carry out the injection. This enables defenders to construct proper detection and mitigation processes, which is something that should not be overlooked.
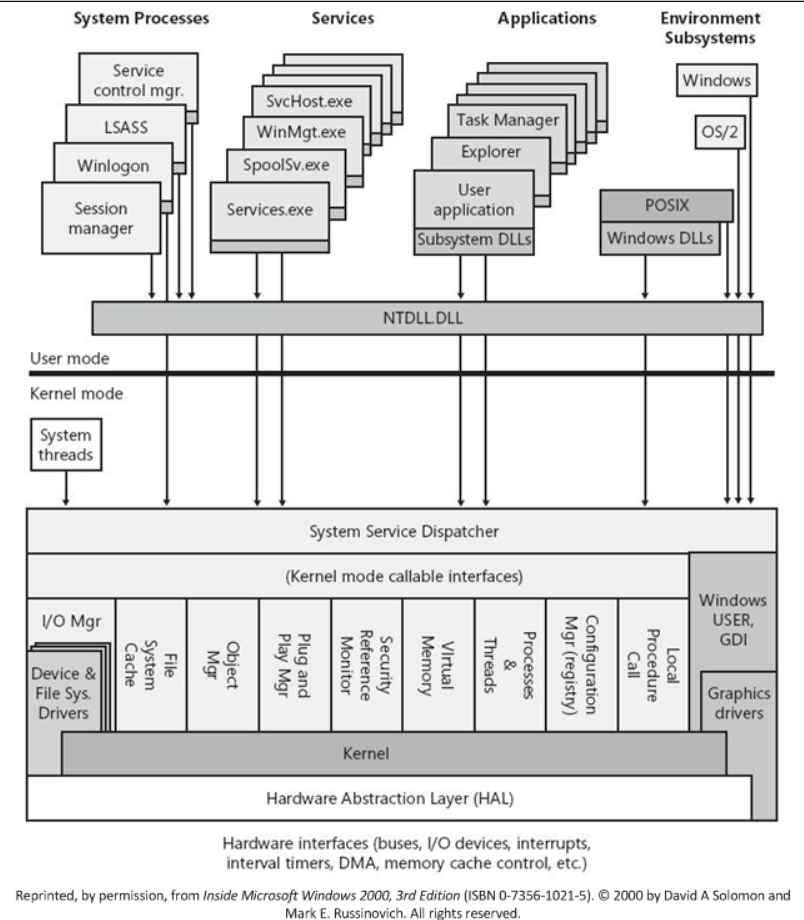
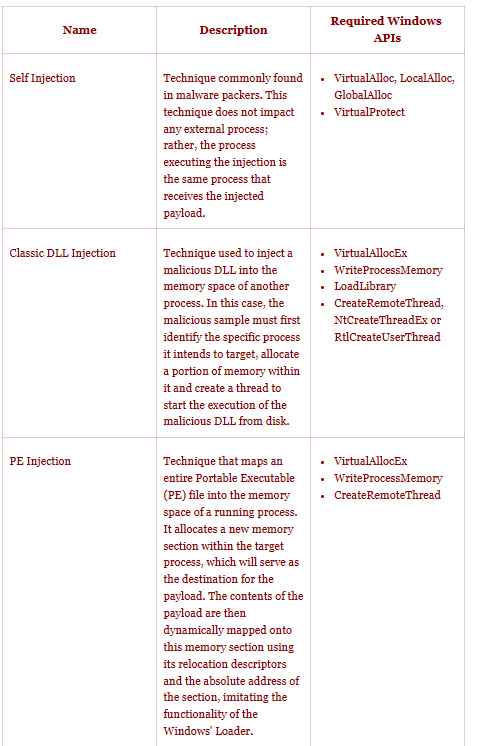
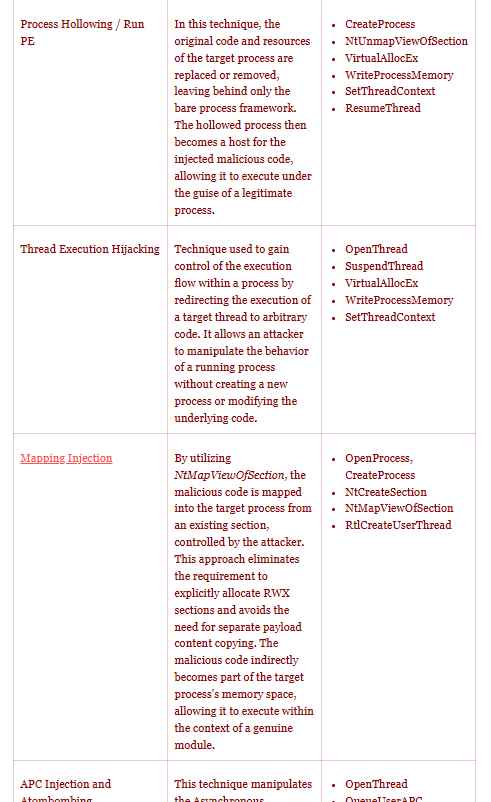
Several different approaches have been created throughout the course of time in order to accomplish the goals of code injection and execution inside the memory area of programs running under Windows. The most frequent Process Injection techniques are outlined and contrasted in the following table, which serves as a reference according to Joes Security company. The table is organized according to the Windows API calls that are necessary for the methods’ effective implementation.
Mockingjay is distinguished from other programs due to the fact that it circumvents these security layers. It does this by removing the requirement to run Windows application programming interfaces (APIs), which are typically monitored by security solutions. Instead, it makes use of pre-existing Windows portable executable files that already come with a memory block that is protected with Read-Write-Execute (RWX) permissions.
This, in turn, is achieved with the help of msys-2.0.dll, which comes with a “generous 16 KB of available RWX space,” making it an excellent candidate to load malicious code and slip under the radar at the same time. Having said that, it is important to highlight the possibility that there might be more vulnerable DLLs that have comparable qualities.
The business said it investigated two distinct approaches, known as self injection and remote process injection, to perform code injection in a way that not only enhanced the effectiveness of the attack but also evaded detection.
The first method involves using a specialized program in order to directly load the vulnerable DLL into the address space of the application, which then allows the RWX section to finally carry out the intended execution of code. In contrast, remote process injection involves using the RWX section of a vulnerable DLL in order to carry out process injection in a remote process such as ssh.exe. This may be accomplished by leveraging the vulnerable DLL.
The distinctiveness of this approach lies in the fact that it is not necessary to allocate memory, set permissions, or create a new thread within the target process in order to initiate the execution of our injected code.It is difficult for Endpoint Detection and Response (EDR) systems to identify this tactic since it differs from other currently used strategies.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











