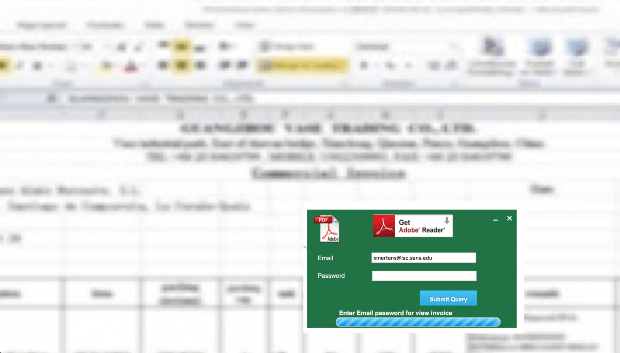
Now it’s easy to see if leaked passwords work on other sites
Freely available tool follows the release of more than 642 million account credentials. Over the past few months, a cluster of megabreaches has dumped account credentials for a mind-boggling 642Read More →