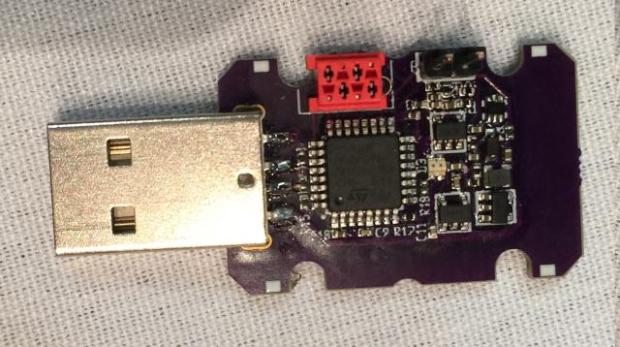
USB Killer, yours for $50, lets you easily fry almost every device
Only real defense for billions of devices is physically capping ports. Last year we wrote about the “USB Killer”—a DIY USB stick that fried almost everything (laptops, smartphones, consoles, cars) thatRead More →