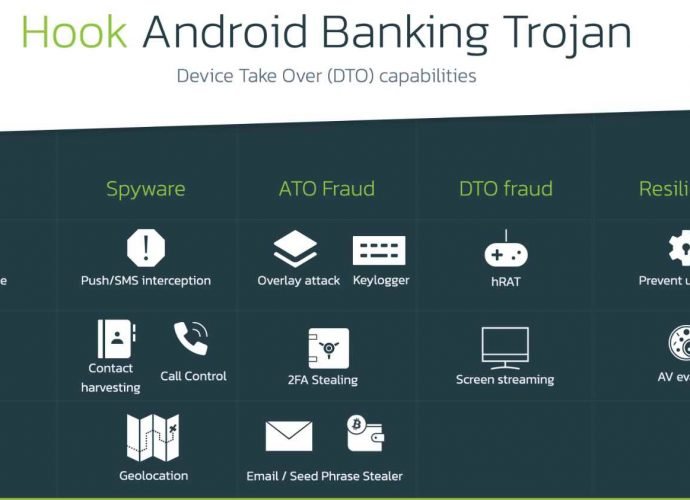
This new android malware allows to hack & spy on any Android phone
Cybercriminals are now peddling a new piece of malicious software for Android called “Hook,” which boasts the ability to remotely take control of mobile devices in real-time via VNC (virtualRead More →