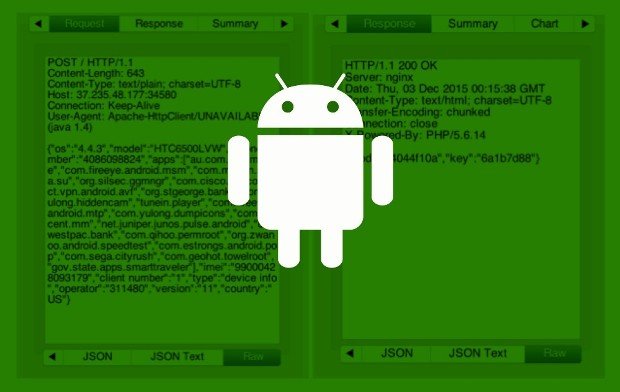
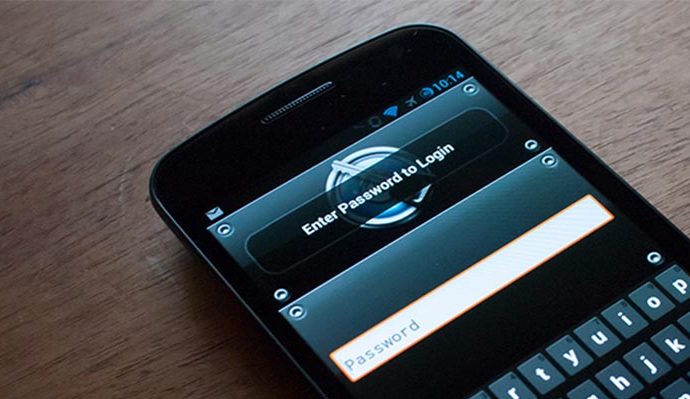
SlemBunk Android Banking Trojan Targets 31 Banks Across the World
Trojan works by injecting fake logins into legitimate apps.A new Android banking trojan, named SlemBunk, has been uncovered by FireEye’s security team, one that targets users utilizing mobile banking appsRead More →