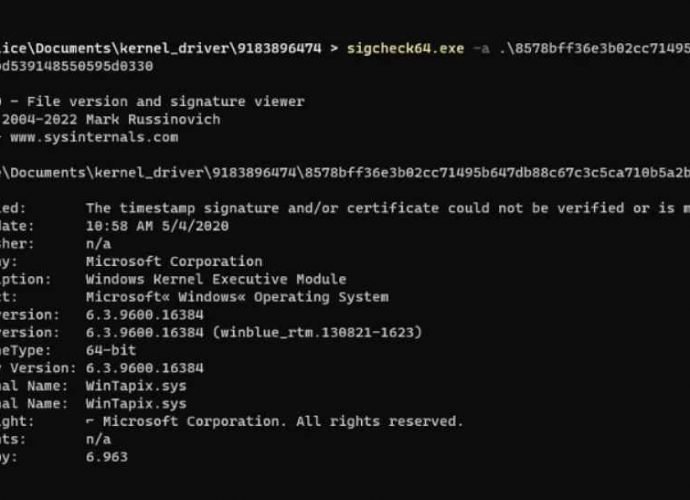
WinTapix: A Windows kernel driver that hackers are exploiting. Check your system processes!
WinTapix is a driver developed by Microsoft for Windows.Donut is a position-independent shellcode that is used by this driver. It loads.NET Assemblies, PE files, and other Windows payloads from memoryRead More →